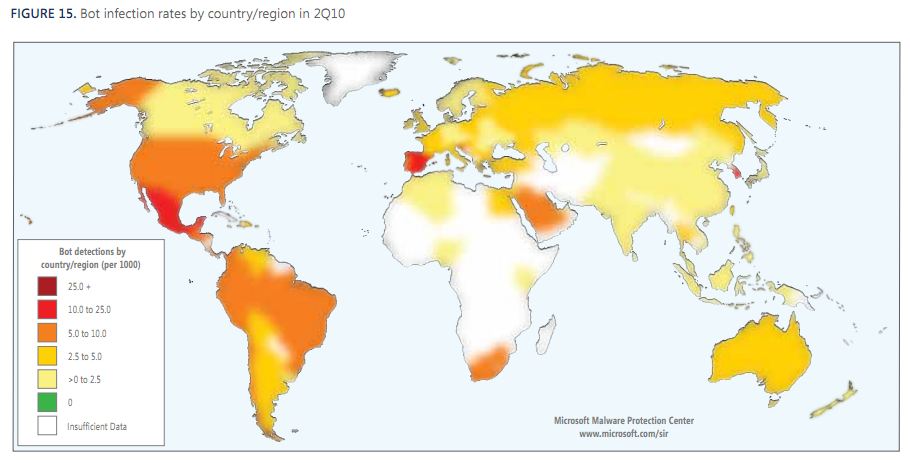
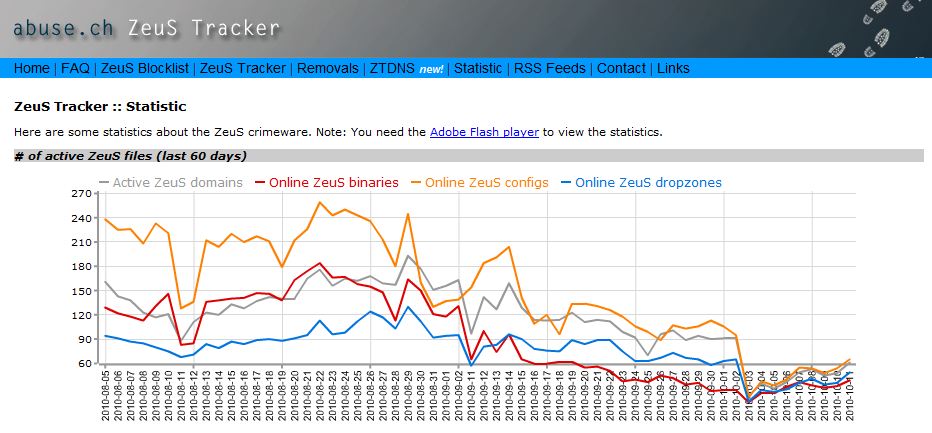
Leading malware developers within the cyber crime community have conspired to terminate development of the infamous ZeuS banking Trojan and to merge its code base with that of the up-and-coming SpyEye Trojan, new evidence suggests. The move appears to be aimed at building a superior e-banking threat whose sale is restricted to a more exclusive and well-heeled breed of cyber crook.
Underground forums are abuzz with rumors that the ZeuS author — a Russian hacker variously known by the monikers “Slavik” and “Monstr” — is no longer planning to maintain the original commercial crimeware kit.
According to numerous hacker forums, the source code for ZeuS recently was transferred to the developer of the SpyEye Trojan, a rival malware maker who drew attention to himself by dubbing his creation the “ZeuS Killer.” The upstart banking Trojan author constantly claimed that his bot creation kit bested ZeuS in functionality and form (SpyEye made headlines this year when investigators discovered it automatically searched for and removed ZeuS from infected PCs before installing itself).
In an era when it has become a truism to say that malicious hackers seek riches over renown, the SpyEye author — a coder known as either “Harderman” and “Gribodemon” on different forums — appears to have sought both, boasting on numerous forums about the greatness of his malware, using flashy logos to promote it (see below), and granting an interview with security researchers about the riches it will bring him. Although the ZeuS author chose to license his botnet creation kit to private groups through multiple intermediaries, the SpyEye creator has peddled his kit directly to buyers via online forums and instant messages.
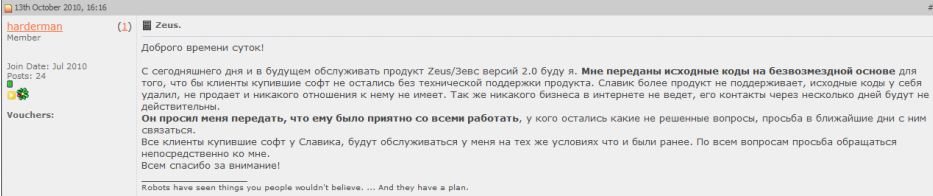
But — very recently — the public rivalry died down, and forum members on different sites where Harderman maintained a presence began complaining that they could no longer reach him for support issues. In an Oct. 11 message to one of the UnderWeb’s most exclusive hacker forums, Harderman can be seen breaking the news to fellow forum members. A screen shot of that message is below, followed by a translated version of it:
Good day!
I will service the Zeus product beginning today and from here on. I have been given the source codes free of charge so that clients who bought the software are not left without tech support. Slavik doesn’t support the product anymore, he removed the source code from his [computer], he doesn’t sell [it], and has no relationship to it. He also doesn’t conduct any business on the Internet and in a few days his contact [information] will not be active.
He asked me to pass on that he was happy to work with everyone. If you have any unresolved issues remaining [there is a] request to get in touch with him as soon as possible.
All clients who bought the software from Slavik will be serviced from me on the same conditions as previously. [I] request that [you] come directly to me regarding all issues.
Thanks to everyone for [your] attention!