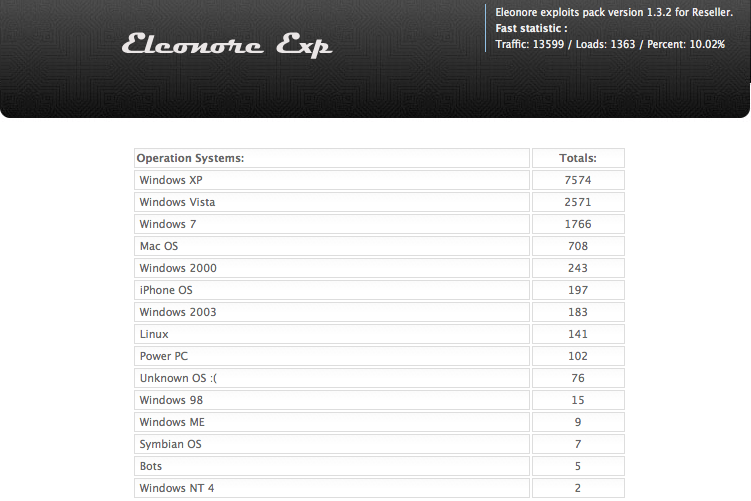
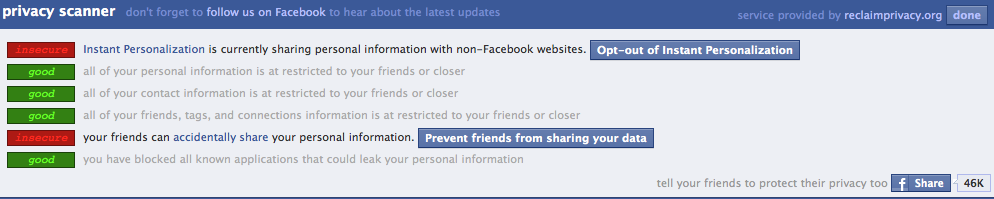
ATM skimmers –or fraud devices that criminals attach to cash machines in a bid to steal and ultimately clone customer bank card data — are marketed on a surprisingly large number of open forums and Web sites. For example, ATMbrakers operates a forum that claims to sell or even rent ATM skimmers. Tradekey.com, a place where you can find truly anything for sale, also markets these devices on the cheap.
The truth is that most of these skimmers openly advertised are little more than scams designed to separate clueless crooks from their ill-gotten gains. Start poking around on some of the more exclusive online fraud forums for sellers who have built up a reputation in this business and chances are eventually you will hit upon the real deal.
Generally, these custom-made devices are not cheap, and you won’t find images of them plastered all over the Web. Take these pictures, for instance, which were obtained directly from an ATM skimmer maker in Russia. This custom-made skimmer kit is designed to fit on an NCR ATM model 5886, and it is sold on a few criminal forums for about 8,000 Euro — shipping included. It consists of two main parts: The upper portion is a carefully molded device that fits over the card entry slot and is able to read and record the information stored on the card’s magnetic stripe (I apologize for the poor quality of the pictures: According to the Exif data included in these images, they were taken earlier this year with a Nokia 3250 phone).
The second component is a PIN capture device that is essentially a dummy metal plate with a look-alike PIN entry pad designed to rest direct on top of the actual PIN pad, so that any keypresses will be both sent to the real ATM PIN pad and recorded by the fraudulent PIN pad overlay.
 Both the card skimmer and the PIN pad overlay device relay the data they’ve stolen via text message, and each has its own miniature GSM device that relays SMS messages (buyers of these kits are responsible for supplying their own SIM cards). According to the vendor of this skimmer set, the devices are powered by lithium ion batteries, and can run for 3-5 days on a charge, assuming the skimmers transmit on average about 200-300 SMS messages per day.
Both the card skimmer and the PIN pad overlay device relay the data they’ve stolen via text message, and each has its own miniature GSM device that relays SMS messages (buyers of these kits are responsible for supplying their own SIM cards). According to the vendor of this skimmer set, the devices are powered by lithium ion batteries, and can run for 3-5 days on a charge, assuming the skimmers transmit on average about 200-300 SMS messages per day.