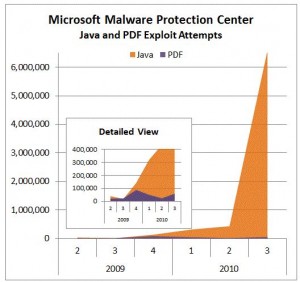
I’ve received several e-mails from readers concerned about a mysterious, undocumented software patch that Microsoft began offering to Windows 7 users through Windows Update this week. Some Microsoft users have been spinning conspiracy theories about this patch because it lacks any real description of its function, and what little documentation there is about it says that it cannot be removed once installed and that it may be required as a prerequisite for installing future updates.
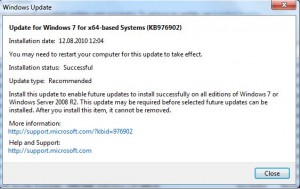 Normally, when Microsoft offers a patch through Windows Update, it also will publish a corresponding “knowledgebase” article that describes in great detail what the patch does and why users should install it — and how applying the update may impact current and future operations on the system.
Normally, when Microsoft offers a patch through Windows Update, it also will publish a corresponding “knowledgebase” article that describes in great detail what the patch does and why users should install it — and how applying the update may impact current and future operations on the system.
This fix went out via Windows Update on Oct. 26 as a “recommended” and “important” patch, but it lacked any additional details, prompting conspiracy theories and speculation on message boards from users wondering whether they should ignore or install this update — which for many users was sandwiched between the dozens of security patches Microsoft began offering earlier this month as part of its regular Patch Tuesday security update cycle.
To make matters worse, many Windows 7 users said the patch was no longer offered after they declined installing it the first time, leading some curious researchers to dub it the “Blackhole” update.
I have verified with Microsoft that this update is designed to smooth the way for the deployment of future updates on Windows 7 systems (read on to the very end if you’d like the official response from Microsoft). The confusion appears to stem from a timing mistake by the folks at Microsoft, but this incident illustrates the hysteria that can ensue when the world’s largest software company fails — for whatever reason — to be fully transparent with a user base that has come to expect detailed advisories with every patch.
When I was researching this patch, I found an amusing thread on the Microsoft Answers forum — where several Microsoft most valuable professional experts urged other forum members to hold off installing the patch until more information was available. Others offered more speculative answers, suggesting that the patch was instead:
-A new service pack for Windows 7
-A “heuristic scanner to the machine that turned on whenever the machine went idle, and searched all attached storage devices for ‘terrorism-related’ information, then alerting ‘somebody’ over the Internet”
-The result of Microsoft having been hacked, with the patch being some kind of malicious third-party code being sent out to infect all Windows machines
-A new anti-piracy check from Microsoft.