A financial cybercrime group calling itself the Disneyland Team has been making liberal use of visually confusing phishing domains that spoof popular bank brands using Punycode, an Internet standard that allows web browsers to render domain names with non-Latin alphabets like Cyrillic.
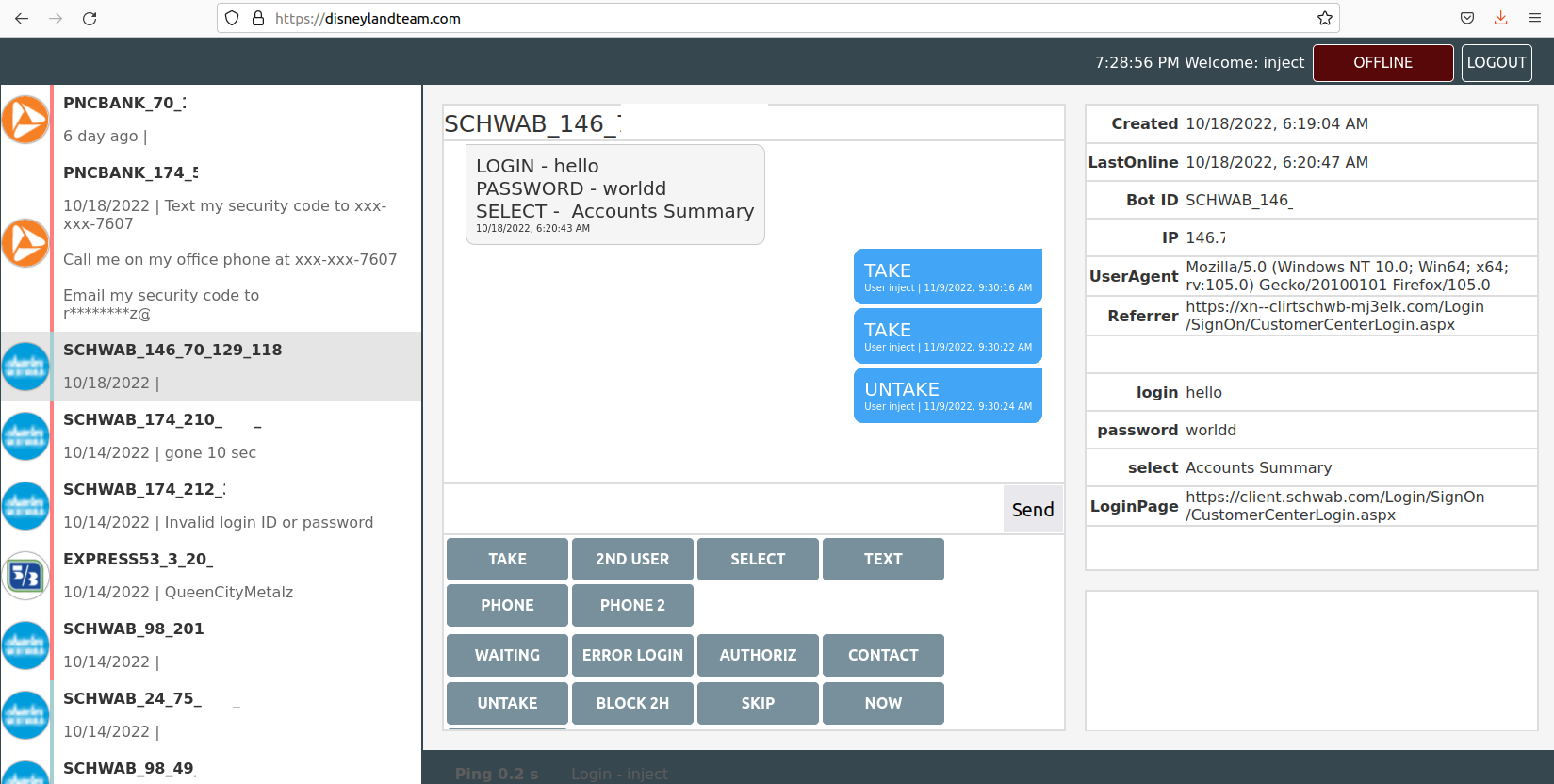
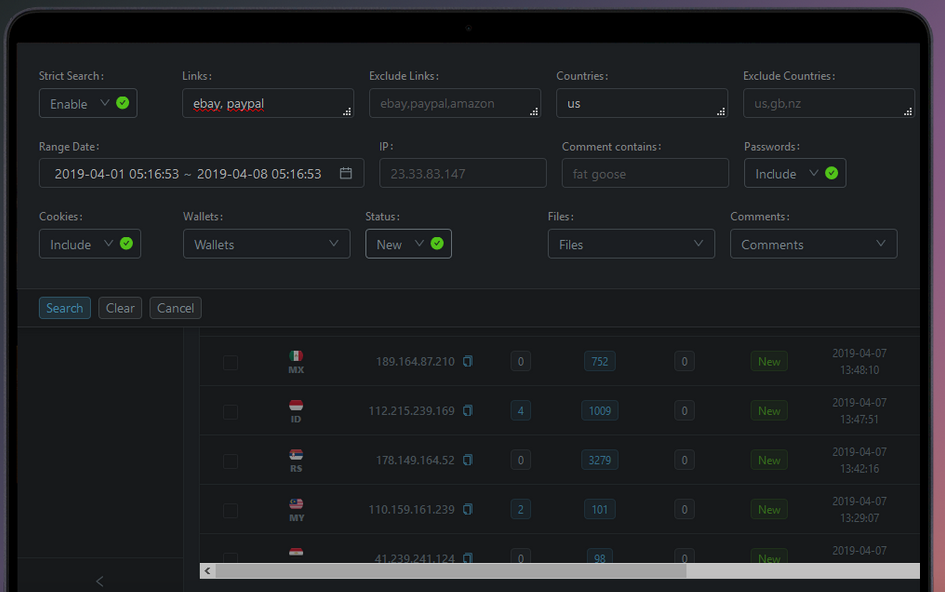
The Disneyland Team’s Web interface, which allows them to interact with malware victims in real time to phish their login credentials using phony bank websites.
The Disneyland Team uses common misspellings for top bank brands in its domains. For example, one domain the gang has used since March 2022 is ushank[.]com — which was created to phish U.S. Bank customers.
But this group also usually makes use of Punycode to make their phony bank domains look more legit. The U.S. financial services firm Ameriprise uses the domain ameriprise.com; the Disneyland Team’s domain for Ameriprise customers is https://www.xn--meripris-mx0doj[.]com [brackets added to defang the domain], which displays in the browser URL bar as ạmeriprisẹ[.]com.
Look carefully, and you’ll notice small dots beneath the “a” and the second “e”. You could be forgiven if you mistook one or both of those dots for a spec of dust on your computer screen or mobile device.
This candid view inside the Disneyland Team comes from Alex Holden, founder of the Milwaukee-based cybersecurity consulting firm Hold Security. Holden’s analysts gained access to a Web-based control panel the crime group has been using to keep track of victim credentials (see screenshot above). The panel reveals the gang has been operating dozens of Punycode-based phishing domains for the better part of 2022.
Have a look at the Punycode in this Disneyland Team phishing domain: https://login2.xn--mirtesnbd-276drj[.]com, which shows up in the browser URL bar as login2.ẹmirạtesnbd[.]com, a domain targeting users of Emirates NBD Bank in Dubai.
Here’s another domain registered this year by the Disneyland Team: https://xn--clientchwb-zxd5678f[.]com, which spoofs the login page of financial advisor Charles Schwab with the landing page of cliẹntșchwab[.]com. Again, notice the dots under the letters “e” and “s”. Another Punycode domain of theirs sends would-be victims to cliẹrtschwạb[.]com, which combines a brand misspelling with Punycode.
We see the same dynamic with the Disneyland Team Punycode domain https://singlepoint.xn--bamk-pxb5435b[.]com, which translates to singlepoint.ụșbamk[.]com — again phishing U.S. Bank customers.
What’s going on here? Holden says the Disneyland Team is Russian-speaking — if not also based in Russia — but it is not a phishing gang per se. Rather, this group uses the phony bank domains in conjunction with malicious software that is already secretly installed on a victim’s computer.
Holden said the Disneyland Team domains were made to help the group steal money from victims infected with a powerful strain of Microsoft Windows-based banking malware known as Gozi 2.0/Ursnif. Gozi specializes in collecting credentials, and is mainly used for attacks on client-side online banking to facilitate fraudulent bank transfers. Gozi also allows the attackers to connect to a bank’s website using the victim’s computer.
In years past, crooks like these would use custom-made “web injects” to manipulate what Gozi victims see in their Web browser when they visit their bank’s site. These web injects allowed malware to rewrite the bank’s HTML code on the fly, and copy and/or intercept any data users would enter into a web-based form, such as a username and password.
Most Web browser makers, however, have spent years adding security protections to block such nefarious activity. As a result, the Disneyland Team simply tries to make their domains look as much like the real thing as possible, and then funnel victims toward interacting with those imposter sites.
“The reason that it is infeasible for them to use in-browser injects include browser and OS protection measures, and difficulties manipulating dynamic pages for banks that require multi-factor authentication,” Holden said.
In reality, the fake bank website overlaid by the Disneyland Team’s malware relays the victim’s browser activity through to the real bank website, while allowing the attackers to forward any secondary login requests from the bank, such as secret questions or multi-factor authentication challenges. Continue reading