Data Viper, a security startup that provides access to some 15 billion usernames, passwords and other information exposed in more than 8,000 website breaches, has itself been hacked and its user database posted online. The hackers also claim they are selling on the dark web roughly 2 billion records Data Viper collated from numerous breaches and data leaks, including data from several companies that likely either do not know they have been hacked or have not yet publicly disclosed an intrusion.
The apparent breach at St. Louis, Mo. based Data Viper offers a cautionary and twisted tale of what can happen when security researchers seeking to gather intelligence about illegal activity online get too close to their prey or lose sight of their purported mission. The incident also highlights the often murky area between what’s legal and ethical in combating cybercrime.

Data Viper is the brainchild of Vinny Troia, a security researcher who runs a cyber threat intelligence company called Night Lion Security. Since its inception in 2018, Data Viper has billed itself as a “threat intelligence platform designed to provide organizations, investigators and law enforcement with access to the largest collection of private hacker channels, pastes, forums and breached databases on the market.”
Many private companies sell access to such information to vetted clients — mainly law enforcement officials and anti-fraud experts working in security roles at major companies that can foot the bill for these often pricey services.
Data Viper has sought to differentiate itself by advertising “access to private and undisclosed breach data.” As KrebsOnSecurity noted in a 2018 story, Troia has acknowledged posing as a buyer or seller on various dark web forums as a way to acquire old and newly-hacked databases from other forum members.
But this approach may have backfired over the weekend, when someone posted to the deep web a link to an “e-zine” (electronic magazine) describing the Data Viper hack and linking to the Data Viper user base. The anonymous poster alleged he’d been inside Data Viper for months and had exfiltrated hundreds of gigabytes of breached data from the service without notice.
The intruder also linked to several dozen new sales threads on the dark web site Empire Market, where they advertise the sale of hundreds of millions of account details from dozens of leaked or hacked website databases that Data Viper allegedly acquired via trading with others on cybercrime forums.
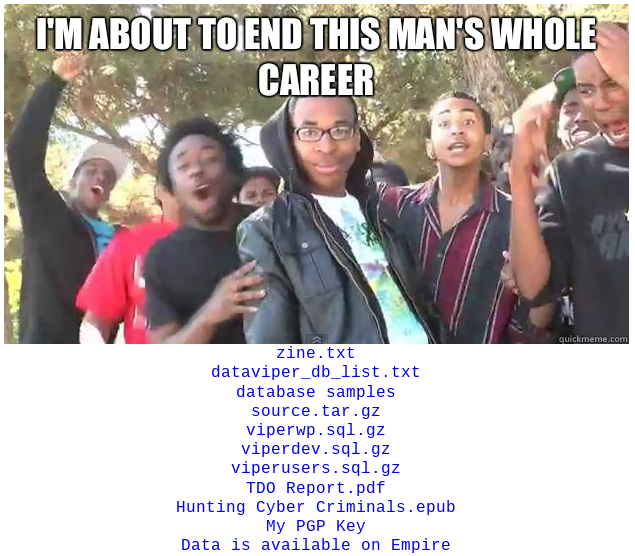
An online post by the attackers who broke into Data Viper.
Some of the databases for sale tie back to known, publicly reported breaches. But others correspond to companies that do not appear to have disclosed a security incident. As such, KrebsOnSecurity is not naming most of those companies and is currently attempting to ascertain the validity of the claims.
KrebsOnSecurity did speak with Victor Ho, the CEO of Fivestars.com, a company that helps smaller firms run customer loyalty programs. The hackers claimed they are selling 44 million records taken from Fivestars last year. Ho said he was unaware of any data security incident and that no such event had been reported to his company, but that Fivestars is now investigating the claims. Ho allowed that the number of records mentioned in the dark web sales thread roughly matches the number of users his company had last year.
But on Aug. 3, 2019, Data Viper’s Twitter account casually noted, “FiveStars — 44m breached records added – incl Name, Email, DOB.” The post, buried among a flurry of similar statements about huge caches of breached personal information added to Data Viper, received hardly any attention and garnered just one retweet.
GNOSTIC PLAYERS, SHINY HUNTERS
Reached via Twitter, Troia acknowledged that his site had been hacked, but said the attackers only got access to the development server for Data Viper, and not the more critical production systems that power the service and which house his index of compromised credentials.
Troia said the people responsible for compromising his site are the same people who hacked the databases they are now selling on the dark web and claiming to have obtained exclusively from his service.
What’s more, Troia believes the attack was a preemptive strike in response to a keynote he’s giving in Boston this week: On June 29, Troia tweeted that he plans to use the speech to publicly expose the identities of the hackers, who he suspects are behind a large number of website break-ins over the years.
Hacked or leaked credentials are prized by cybercriminals engaged in “credential stuffing,” a rampant form of cybercrime that succeeds when people use the same passwords across multiple websites. Armed with a list of email addresses and passwords from a breached site, attackers will then automate login attempts using those same credentials at hundreds of other sites.
Password re-use becomes orders of magnitude more dangerous when website developers engage in this unsafe practice. Indeed, a January 2020 post on the Data Viper blog suggests credential stuffing is exactly how the group he plans to discuss in his upcoming talk perpetrated their website compromises.
In that post, Troia wrote that the hacker group, known variously as “Gnostic Players” and “Shiny Hunters,” plundered countless website databases using roughly the same method: Targeting developers using credential stuffing attacks to log into their GitHub accounts.
“While there, they would pillage the code repositories, looking for AWS keys and similar credentials that were checked into code repositories,” Troia wrote.
Troia said the intrusion into his service wasn’t the result of the credential re-use, but instead because his developer accidentally left his credentials exposed in documents explaining how customers can use Data Viper’s application programming interface.
“I will say the irony of how they got in is absolutely amazing,” Troia said. “But all of this stuff they claim to be selling is [databases] they were already selling. All of this is from Gnostic players. None of it came from me. It’s all for show to try and discredit my report and my talk.”
Troia said he didn’t know how many of the databases Gnostic Players claimed to have obtained from his site were legitimate hacks or even public yet.
“As for public reporting on the databases, a lot of that will be in my report Wednesday,” he said. “All of my ‘reporting’ goes to the FBI.”
SMOKE AND MIRRORS
The e-zine produced by the Data Viper hackers claimed that Troia used many nicknames on various cybercrime forums, including the moniker “Exabyte” on OGUsers, a forum that’s been closely associated with account takeovers.
In a conversation with KrebsOnSecurity, Troia acknowledged that this Exabyte attribution was correct, noting that he was happy about the exposure because it further solidified his suspicions about who was responsible for hacking his site.
This is interesting because some of the hacked databases the intruders claimed to have acquired after compromising Data Viper correspond to discoveries credited to Troia in which companies inadvertently exposed tens of millions of user details by leaving them publicly accessible online at cloud services like Amazon’s EC2.
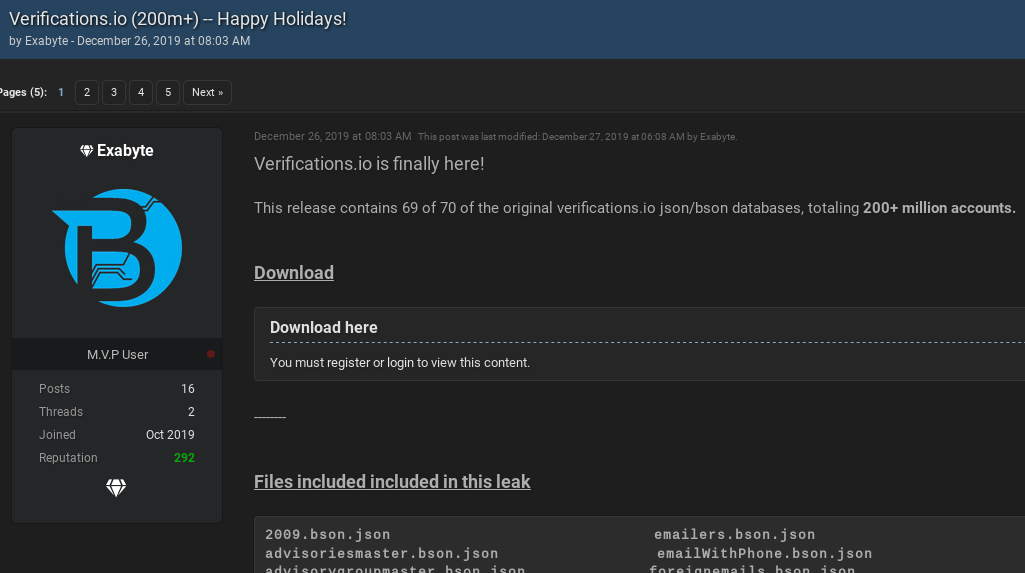
For example, in March 2019, Troia said he’d co-discovered a publicly accessible database containing 150 gigabytes of plaintext marketing data — including 763 million unique email addresses. The data had been exposed online by Verifications.io, an email validation firm.
On Oct 12, 2019, a new user named Exabyte registered on RaidForums — a site dedicated to sharing hacked databases and tools to perpetrate credential stuffing attacks. That Exabyte account was registered less than two weeks after Troia created his Exabyte identity on OGUsers. The Exabyte on RaidForums posted on Dec. 26, 2019 that he was providing the community with something of a belated Christmas present: 200 million accounts leaked from Verifications.io.
“Verifications.io is finally here!” Exabyte enthused. “This release contains 69 of 70 of the original verifications.io databases, totaling 200+ million accounts.”
In May 2018, Troia was featured in Wired.com and many other publications after discovering that sales intelligence firm Apollo left 125 million email addresses and nine billion data points publicly exposed in a cloud service. As I reported in 2018, prior to that disclosure Troia had sought my help in identifying the source of the exposed data, which he’d initially and incorrectly concluded was exposed by LinkedIn.com. Rather, Apollo had scraped and collated the data from many different sites, including LinkedIn.
Then in August 2018, someone using the nickname “Soundcard” posted a sales thread to the now-defunct Kickass dark web forum offering the personal information of 212 million LinkedIn users in exchange for two bitcoin (then the equivalent of ~$12,000 USD). Incredibly, Troia had previously told me that he was the person behind that Soundcard identity on the Kickass forum.
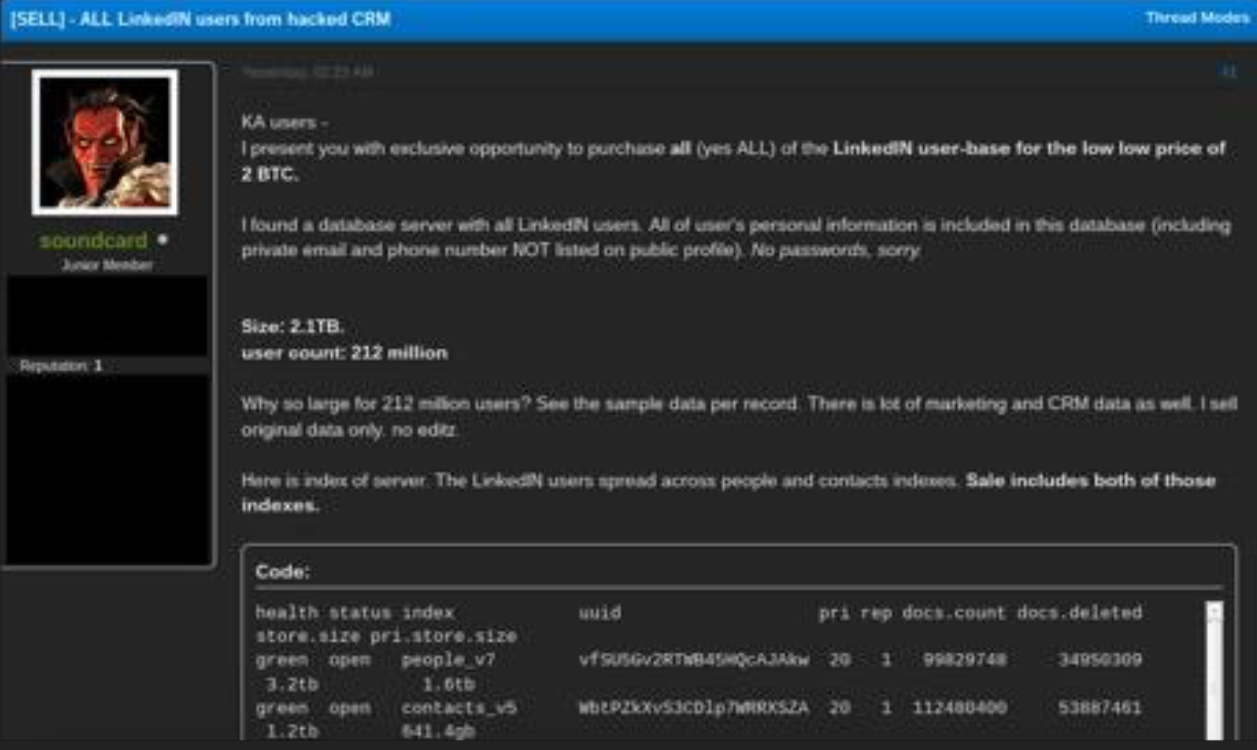
Soundcard, a.k.a. Troia, offering to sell what he claimed was all of LinkedIn’s user data, on the Dark Web forum Kickass.
Asked about the Exabyte posts on RaidForums, Troia said he wasn’t the only one who had access to the Verifications.io data, and that the full scope of what’s been going on would become clearer soon.
“More than one person can have the same name ‘Exabyte,” Troia said. “So much from both sides you are seeing is smoke and mirrors.”
Smoke and mirrors, indeed. It’s entirely possible this incident is an elaborate and cynical PR stunt by Troia to somehow spring a trap on the bad guys. Troia recently published a book on threat hunting, and on page 360 (PDF) he describes how he previously staged a hack against his own site and then bragged about the fake intrusion on cybercrime forums in a bid to gather information about specific cybercriminals who took the bait — the same people, by the way, he claims are behind the attack on his site.









 On June 16, authorities in Michigan arrested 29-year-old Justin Sean Johnson in connection with a 43-count indictment on charges of conspiracy, wire fraud and aggravated identity theft.
On June 16, authorities in Michigan arrested 29-year-old Justin Sean Johnson in connection with a 43-count indictment on charges of conspiracy, wire fraud and aggravated identity theft.