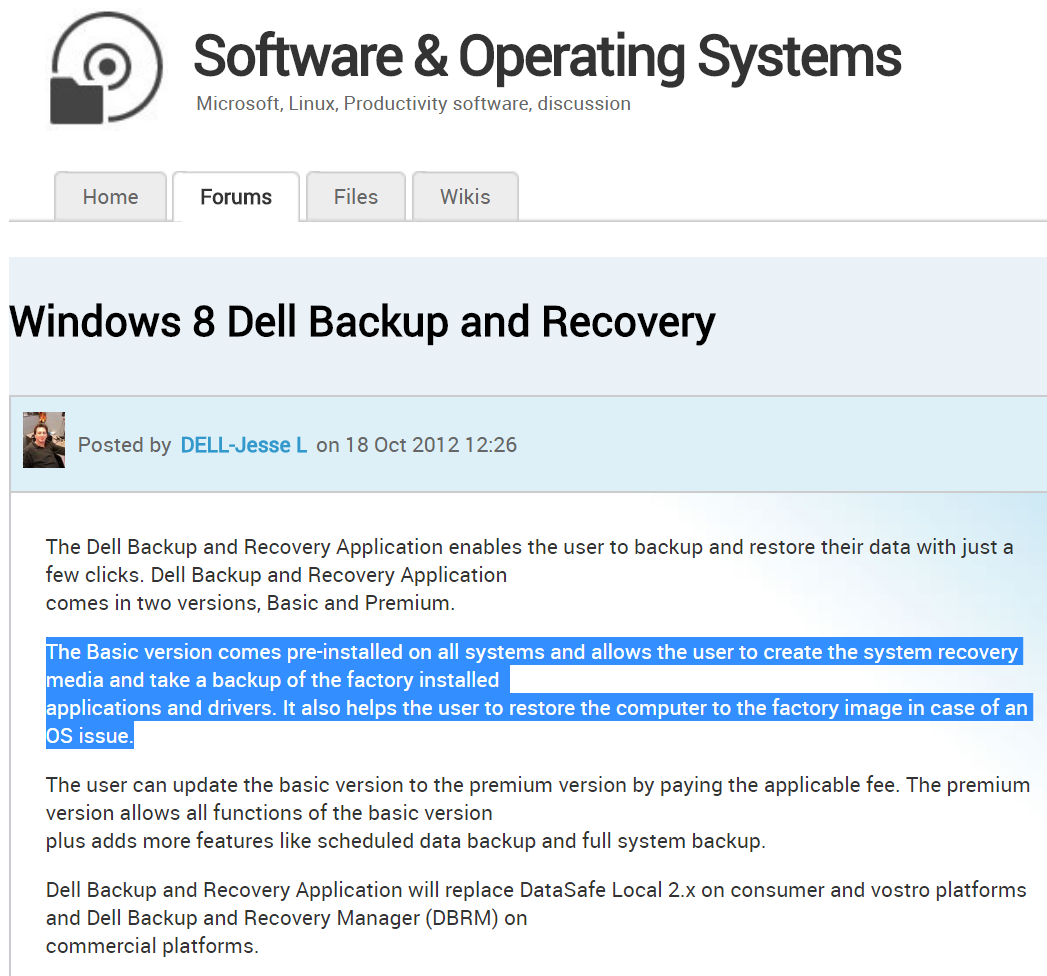
In May 2013 KrebsOnSecurity wrote about Ragebooter, a service that paying customers can use to launch powerful distributed denial-of-service (DDoS) attacks capable of knocking individuals and Web sites offline. The owner of Ragebooter subsequently was convicted in 2016 of possessing child pornography, but his business somehow lived on while he was in prison. Now just weeks after Poland made probation, a mobile version of the attack-for-hire service has gone up for sale on the Google Play store.
In the story Ragebooter: ‘Legit’ DDoS Service, or Fed Backdoor, I profiled then 19-year-old Justin D. Poland from Memphis — who admitted to installing code on his Ragebooter service that allowed FBI investigators to snoop on his customers.
Last February, Poland was convicted of one felony count of possession of child pornography, after investigators reportedly found 2,600 child pornography images on one of his computers. Before his trial was over, Poland skipped town but his bondsman later located him at his mother’s house. He was sentenced to two years in jail.
Poland did not respond to multiple requests for comment, but on his Facebook account Poland said the images belonged to his former roommate — David Starliper — who’d allegedly used Poland’s computer. Starliper also was convicted of possessing child pornography and sentenced to two years in prison.
In September 2017, Poland began posting on his Facebook account that he had made parole and was getting ready to be released from prison. On Oct. 6, the first version of the Android edition of Ragebooter was put on sale at Google’s Play Store.

The mobile version of Ragebooter.
Poland’s Facebook page says he is the owner of ragebooter[dot]com, ragebooter[dot]net, and another site called vmdeploy[net]. The advertisement for Ragebooter’s new mobile app on Google Play says the developer’s email address is contact@rageservices[dot]net. The registration details for rageservices[dot]net are hidden, but the Web site lists some useful contact details.
One of them is a phone number registered in Memphis — 901-219-3644 — that is tied to a Facebook account for an Alex Slovak in Memphis. The other domain Poland mentions on his Facebook page — vmdeploy[dot]net — was registered to an Alex Czech from Memphis. It seems likely that Alex has been running Ragebooter while Poland was in prison. Mr. Slovak/Czech did not respond to requests for comment, but it is clear from his Facebook page that he is friends with Poland’s family. Continue reading




 Most financial institutions will let customers add verbal passwords or personal identification numbers (PINs) that are separate from any other PIN or online banking password you might use, although few will advertise this.
Most financial institutions will let customers add verbal passwords or personal identification numbers (PINs) that are separate from any other PIN or online banking password you might use, although few will advertise this.
 Arbor Networks said it believes the size of the Reaper botnet currently fluctuates between 10,000 and 20,000 bots total. Arbor notes that this can change any time.
Arbor Networks said it believes the size of the Reaper botnet currently fluctuates between 10,000 and 20,000 bots total. Arbor notes that this can change any time.