For several months I’ve been poking at a decent-sized spam botnet that appears to be used mainly for promoting adult dating sites. Having hit a wall in my research, I decided it might be good to publish what I’ve unearthed so far to see if this dovetails with any other research out there.
In late October 2016, an anonymous source shared with KrebsOnSecurity.com a list of nearly 100 URLs that — when loaded into a Firefox browser — each displayed what appeared to be a crude but otherwise effective text-based panel designed to report in real time how many “bots” were reporting in for duty.
Here’s a set of archived screenshots of those counters illustrating how these various botnet controllers keep a running tab of how many “activebots” — hacked servers set up to relay spam — are sitting idly by and waiting for instructions.
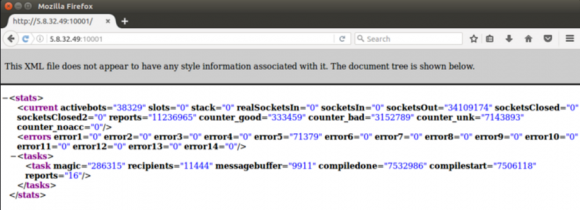
One of the more than 100 panels linked to the same porn spamming operation. In October 2016, these 100 panels reported a total of 1.2 million active bots operating simultaneously.
At the time, it was unclear to me how this apparent botnet was being used, and since then the total number of bots reporting in each day has shrunk considerably. During the week the above-linked screen shots were taken, this botnet had more than 1.2 million zombie machines or servers reporting each day (that screen shot archive includes roughly half of the panels found). These days, the total number of servers reporting in to this spam network fluctuates between 50,000 and 100,000.
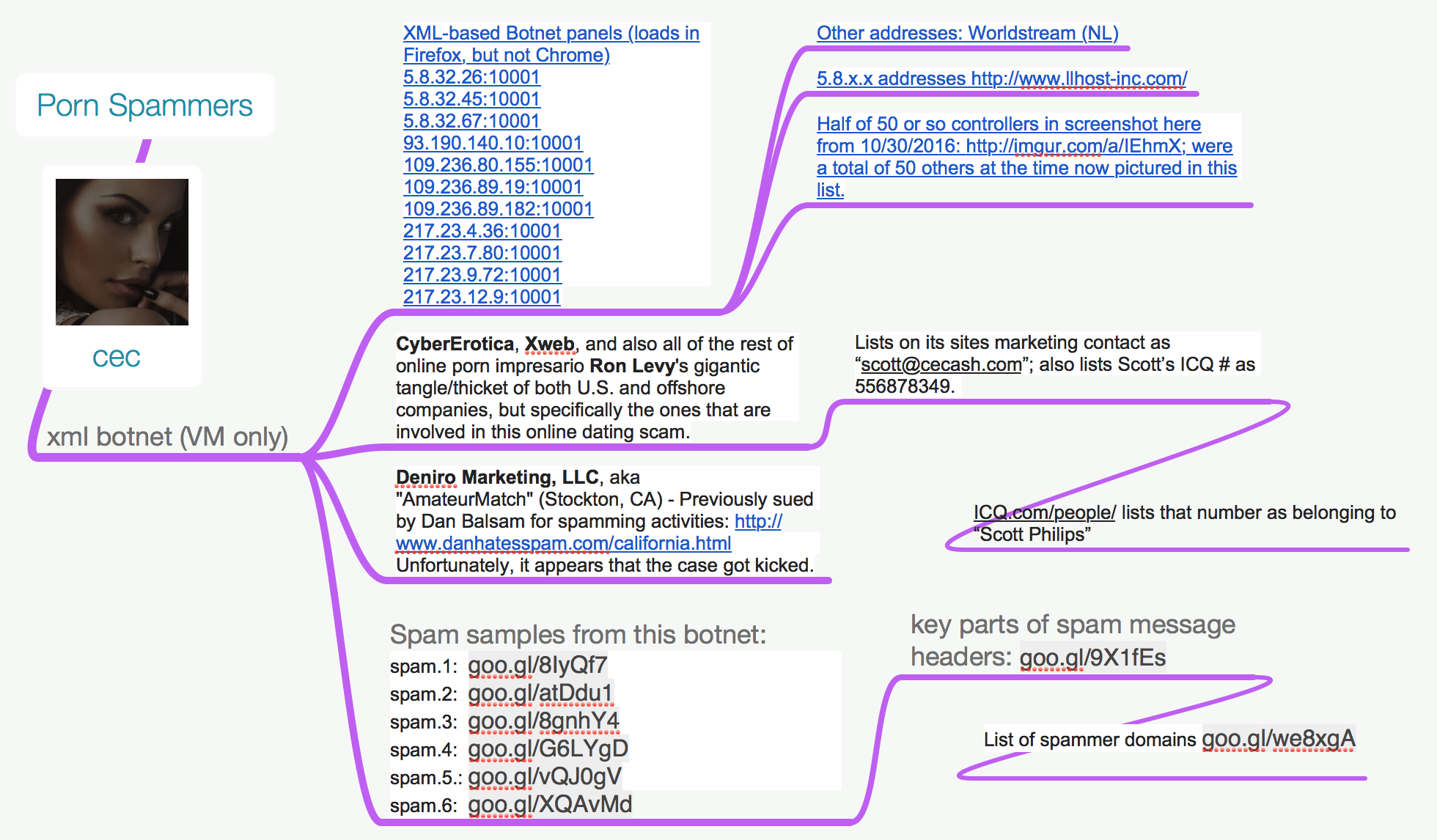
Thanks to a tip from an anti-spam activist who asked not to be named, I was able to see that the botnet appears to be busy promoting a seemingly endless network of adult dating Web sites connected to just two companies: CyberErotica, and Deniro Marketing LLC (a.k.a. AmateurMatch).
As affiliate marketing programs go, CyberErotica stretches way back — perhaps to the beginning. According to TechCrunch, CyberErotica is said to have launched the first online affiliate marketing firm in 1994.
In 2001, CyberErotica’s parent firm Voice Media settled a lawsuit with the U.S. Federal Trade Commission, which alleged that the adult affiliate program was misrepresenting its service as free while it dinged subscribers for monthly charges and made it difficult for them to cancel.
In 2010, Deniro Marketing found itself the subject of a class-action lawsuit that alleged the company employed spammers to promote an online dating service that was overrun with automated, fake profiles of young women. Those allegations ended in an undisclosed settlement after the judge in the case tossed out the spamming claim because the statute of limitations on those charges had expired.
What’s unusual (and somewhat lame) about this botnet is that — through a variety of botnet reporting panels that are still displaying data — we can get live, real-time updates about the size and status of this crime machine. No authentication or credentials needed. So much for operational security!
The “mind map” pictured below contains enough information for nearly anyone to duplicate this research, and includes the full Web address of the botnet reporting panels that are currently online and responding with live updates. I was unable to load these panels in a Google Chrome browser (perhaps the XML data on the page is missing some key components), but they loaded fine in Mozilla Firefox.
But a note of caution: I’d strongly encourage anyone interested in following my research to take care before visiting these panels, preferably doing so from a disposable “virtual” machine that runs something other than Microsoft Windows.
That’s because spammers are usually involved in the distribution of malicious software, and spammers who maintain vast networks of apparently compromised systems are almost always involved in creating or at least commissioning the creation of said malware. Worse, porn spammers are some of the lowest of the low, so it’s only prudent to behave as if any and all of their online assets are actively hostile or malicious.




 According to security firm
According to security firm 
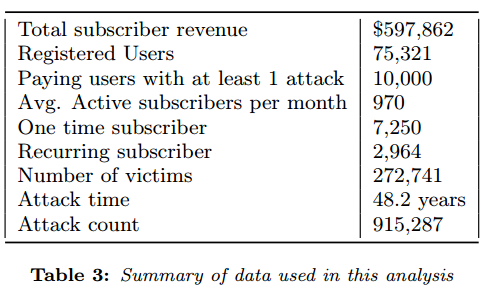 The NYU researchers found that vDOS had extremely low costs, and virtually all of its business was profit. Customers would pay up front for a subscription to the service, which was sold in booter packages priced from $5 to $300. The prices were based partly on the overall number of seconds that an attack may last (e.g., an hour would be 3,600 worth of attack seconds).
The NYU researchers found that vDOS had extremely low costs, and virtually all of its business was profit. Customers would pay up front for a subscription to the service, which was sold in booter packages priced from $5 to $300. The prices were based partly on the overall number of seconds that an attack may last (e.g., an hour would be 3,600 worth of attack seconds). Headquartered in San Francisco, OneLogin provides single sign-on and identity management for cloud-base applications. OneLogin counts among its customers some 2,000 companies in 44 countries, over 300 app vendors and more than 70 software-as-a-service providers.
Headquartered in San Francisco, OneLogin provides single sign-on and identity management for cloud-base applications. OneLogin counts among its customers some 2,000 companies in 44 countries, over 300 app vendors and more than 70 software-as-a-service providers.

 In April 2017 I received an anonymous tip from a reader who said he’d figured out that just by changing a single number in the Web address when accessing his recent medical claim at MolinaHealthcare.com he could then view any and all other patient claims.
In April 2017 I received an anonymous tip from a reader who said he’d figured out that just by changing a single number in the Web address when accessing his recent medical claim at MolinaHealthcare.com he could then view any and all other patient claims.