Last year’s breach at Target Corp. flooded underground markets with millions of stolen credit and debit cards. In the days surrounding the breach disclosure, the cards carried unusually high price tags — in large part because few banks had gotten around to canceling any of them yet. Today, two months after the breach, the number of unsold stolen cards that haven’t been cancelled by issuing banks is rapidly shrinking, forcing the miscreants behind this historic heist to unload huge volumes of cards onto underground markets and at cut-rate prices.
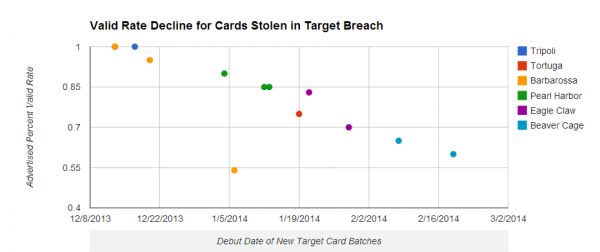
Cards stolen in the Target breach have become much cheaper as more of them come back declined or cancelled by issuing banks.
Earlier today, the underground card shop Rescator[dot]so moved at least 2.8 million cards stolen from U.S.-based shoppers during the Target breach. This chunk of cards, dubbed “Beaver Cage” by Rescator, was the latest of dozens of batches of cards stolen from Target that have gone on sale at the shop since early December.
The Beaver Cage batch of cards have fallen in price by as much as 70 percent compared to those in “Tortuga,” a huge chunk of several million cards stolen from Target that sold for between $26.60 and $44.80 apiece in the days leading up to Dec. 19 — the day that Target acknowledged a breach. Today, those same cards are now retailing for prices ranging from $8 to $28. The oldest batches of cards stolen in the Target breach –i.e., the first batches of stolen cards sold –are at the top of legend in the graphic above; the “newer,” albeit less fresh, batches are at the bottom.
The core reason for the price drop appears to be the falling “valid rate” associated with each batch. Cards in the Tortuga base were advertised as “100 percent valid,” meaning that customers who bought ten cards from the store could expect all 10 to work when they went to use them at retailers to purchase high-priced electronics, gift cards and other items that can be quickly resold for cash.
This latest batch of Beaver Cage cards, however, carries only a 60 percent valid rate, meaning that on average customers can expect at least 4 out of every 10 cards they buy to come back declined or canceled by the issuing bank.
The most previous batch of Beaver Cage cards — pushed out by Rescator on Feb. 6 — included nearly 4 million cards stolen from Target and carried a 65 percent valid rate. Prior to Beaver Cage, the Target cards were code-named “Eagle Claw.” On Jan. 29, Rescator debuted 4 million cards bearing the Eagle Claw name and a 70 percent valid rate. The first two batches of Eagle Claw-branded cards — a chunk of 2 million cards — were released on Jan. 21 with a reported 83 percent valid rate.
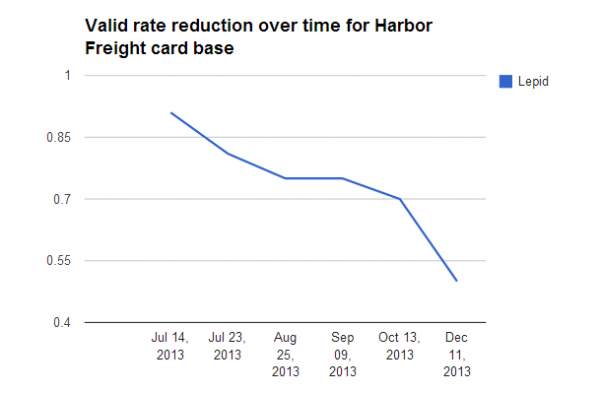
HARBOR FREIGHT
The same pattern can be observed in another major breach from 2013. Relying on much the same method I used to validate the Target breach, I approached several financial institutions to determine if other batches of cards sold by Rescator’s various shops could be traced to specific breaches in 2013.
Sure enough, it didn’t take long to identify the midsummer 2013 breach at Harbor Freight Tools as the source of at least two major batches (they are called “bases” in the card shops, not batches) of cards sold by Rescator’s shops last year. Beginning in late June 2013, Rescator began selling a base called “Lepid,” moving new batches of Lepid cards onto the market almost every week in chunks of 100,000 cards at at time.
Just as with the Target breach, the Lepid cards initially were advertised as 100 percent valid, and came with a hefty price tag. But by mid-July 2013, the valid rates had begun to dip down to 95 percent, most likely because by that time banks had begun seeing the fraud and canceling cards. A month later, the valid rates were below 75 percent, and by the time the Target breach was disclosed in December, fewer than half of the cards were still active.
In late July, Harbor Freight disclosed a breach of its payment card system that lasted for seven weeks between May 6 and June 30, 2013. The company has not said how many customer cards were stolen, but from the volume of Lepid cards pushed onto Rescator’s shop as well as those from other bases tied to cards all used at Harbor Freight during the breach time frame (including bases “Laurentius” and “Sidonius”), it’s likely to have been several million.
The data from both Target and Harbor Freight Tools raise several questions. For starters, why did the valid rate decline so much faster with the Target cards than with those stolen from Harbor Freight? After all, it took nearly six months for the valid rates on cards stolen from Harbor Freight to reach 50 percent, while we’re already fast approaching that rate with the Target cards just two months after that breach was disclosed. I’m guessing the obvious answer is most likely the correct one: That the Target breach simply received a great deal more attention, both from the media and from card-issuing banks nationwide.
Does this mean the Target and Harbor Freight breaches are connected? I have no idea, although I strongly suspect that Rescator and his merry band of thieves played a key role in both breaches — beyond merely offloading stolen cards. In several instances, Rescator himself referred to Lepid as “our” base, indicating the batch was from a firsthand source.
The analysis of some of the malware used in the Target breach suggests that Rescator may have been directly involved in that attack. I don’t have any such clues from the Harbor Freight breach; the company has not responded to requests for comment, and Mandiant — the forensics firm which was called in to investigate the Harbor Freight breach — declined to comment.
Finally, a number of folks with whom I’ve shared this research wondered why any cards that were suspected as stolen in the breach at Target would not already have been canceled by issuing banks. It’s not clear how accurate Rescator’s valid rates are — certainly Rescator has a vested interest in fudging the numbers.
But assuming the percentages are relatively accurate, many factors could explain why some banks haven’t simply canceled and reissued all cards potentially impacted in the breach. One source I spoke with earlier this year from a fairly larger card issuer said his institution still had not reissued at least 40 percent of their cards affected by the Target breach. The source said those cards generally fell into two categories: Cards that had only recently been reissued prior to the Target breach discovery, and those that were expected to naturally reach their expiration dates in the next month or so.
I should note that the above analysis ignores several million non-US cards stolen from Target shoppers and sold under the international “Barbarossa” label (the outlier in orange from the first graphic above), which at one time fetched prices in excess of $120 per card.



![Rescator[dot]so card shop announcing the availability of new bases of Target cards.](https://krebsonsecurity.com/wp-content/uploads/2014/02/rescatorvalid-600x639.png)

Is there any way to know how many of the cards in total have been sold?
Sort of proves out once again that time is money, in this case proportionally inverse as the “asset” depreciates.
How low does the valid rate have to go before the bad guys no longer bother trying to sell them?
I think all of the United States media blitz about the Target Breach real took the wind out of their sails (or sales !)
I would still like to know who the “other six” retailers were from the holiday period. There have been mentions of a half dozen mystery department stores other than Target and Nordstrom.
I get they don’t want the publicity Target got, but they should be legally required to come clean to their customers.
Mia, you bring up an interesting point. Do we have a right to know? We’re not responsible for fraudulent activity so the providers and merchants can keep things on the down low, I suppose. But what about the inconvenience caused by having one’s card disabled or identity stolen? It seems we really should have a right to know because we are adversely affected. It’s up to the legislators, and they’ve been very slow to act. It was only a few years ago that they banned some of the most obnoxious practices. (Remember constantly changing due dates?)
Krebs imagine how many years it will take you to make that soft of money .
2.8 millions cards sold ,lets say 28 $ ( average price per card ) and it all comes to 56 000 000 dead American Presidents and counting .Not bad for a 17 years old kid .Huh ?
Zippy, how did you do that math? Guess it wasn’t from your English teacher. No, just trying to figure it out that’s all. As for the other I think retailers, yes they will have to disclose. However, don’t think the stock market, etc. could handle that kind of news all @ once. Ultimately, the end of this story might be that the lack of legislation or lack of laws that were violated, might not exist. Spinning wheels doin good stuff, yet ultimately what happens in the end?
20-30 % off for Bulk orders .
@zippy… are you one of the hackers? Sounds a bit like you are patting yourself on the back? How did you know the hacker was 17?
He’s referring to an erroneous report that came out in January and named a 17-year-old Russian kid as responsible for creating and selling the point-of-sale malware used in the Target breach. That malware was actually originally created by a 24-year-old kid from Russia, who ultimately acknowledged creating it.
Observations of the valuation of these cards:
I would be cautious with the assumption of using the validity of the card as the card valuation metric. It’s obviously a big one, and short term it’s clearly the largest factor, but there are other valuations of that data.
1) cancelled card holders may become more complacent
I can see a residual value to cancelled cards. Knowing which doors were most recently ‘locked’ gives the bad guys an edge due to human nature. We feel safer right after we lock our door. Someone who just got a new card will feel safer, and after initial safety checks may be less diligent than someone who knows the door is unlocked.
2) the ‘big data’ of old data.
Another perspective is that data that combines a hacked ‘new’ card that with the cancelled card data is what ‘big data’ is all about; taking disparate data, finding new relationships of that data, and then exploiting those relationships. A merchant that asks if you want to link your store rewards card with your credit card is a very similar example of this. Thus the value of a cancelled card and a replaced card could be larger than either alone.
3) exit strategy
That being said, downward pressure on the hacker’s valuation would certainly include ‘carry cost’ (in this case, basically the risk profile of holding thes cards). My guess is that they are like the dog that finally catches the car – they may be looking at their quickest exit strategy yet don’t want to just abandon the ship just yet. Folks who watched “margin call” will see the similarity to when the firm decides to sell (“I must pay” quote). This may explain why the curve is sharper than harbor freight.
4) traunch pricing model
It it clear that they have arranged the card information like MBS traunches. Similar to the Paulson/GS Timerwolf and others, they have put some effort into grouping. They obviously would like to maximize their ‘return’. The sophistication of arranging these traunches tells us quite a bit in itself (Conway’s law). That analysis is best not discussed.
5) avoid predictable game theory countermeasures
I advise ‘whitehats’ against playing according to game theory. In other words we should not make a predictable public analysis, nor a predictable response to the ‘blackhats’ moves. A particular action should be perplexing (art of war) to the ‘blackhats’. They should not know whether to hold the assets long term, or sell short. The buyers should not know whether it’s a ‘good deal’, or a GS special ‘$hitty deal’ of Timberwolf. When we consider not letting the enemy know where to attack, or where they should defend, we as ‘whitehats’, gain an advantage. If we think of it in those terms, it’s understandable that the bank’s actions are perplexing. While I’m not generally in favor of bankers, in this case their actions seem appropriate. It would disrupt the market for these cards more with uncertainty.
The bottom line is there are more considerations than card validity for establishing the value of these cards. The residual value, fear, greed, and uncertainty are just a few of the additional factors.
Well some of them are so arrogantly positive that their fraud detection will work, that they are not issuing new cards. One of mine informed me of this despite the fact that I did use the card at Target during the time window in question. So far I haven’t had an attempt made, but my issuer may be blocking them without telling me. This goes back to the “Whitehat” theory you allude to.
When Discover Card used Online Secure Credit Card Numbers, they would never tell me when attempts were made to abuse the number. The transactions simply got declined, and no notice was giving to me. Over time, I was able to tell it had an effect though, because some otherwise legitimate vendors started losing their usage privileges from the credit card issuing companies. I imagine most of this is because of the liability of besmirching an other wise honest merchant who only through poor practices lost the customers information. It is not hard to imagine a merchant suing a credit corporation or bank, for slander.
@Mia It’s Neiman Marcus not Nordstroms. Target, NM and Michaels so far. Agree that it’s interesting we haven’t yet seen anything on the others.
In two other hacks, LV Sands and UofMaryland offering credit monitoring for a year seems like an insult (note: I’m not sure of duration with LV Sands, but i’m fairly sure it’s not ‘forever’).
Do they think the SS numbers, peoples names, addresses etc. all change within that year? Or, as we all know is it’s just window dressing as they pass the cost of their data mining/hoarding onto grandma?
Seems to me credit monitoring for life is a minimum as the data breach doesn’t just disappear after a year.
The way that these folks think about these data breaches is unreal. They first mine the data, hoard it, then they lose it, and top it off by devaluing the people injured by insulting them afterwards.
Credit monitoring.. for a year.. wow! at least they could have sent them a pizza like they did for the toxic mess in NC. (I’m being snarky here).
A couple of questions.. why was that data being kept? Does UofM really need 16 year old data on students to include SS numbers online to conduct their “business”? Seems to me we have national disease of what I call “data hoarding”. They couldn’t protect the non-current students with offline storage? Did they ever, EVER, think about what harm that data does to people when they lose it? Doesn’t seem so, because they made the choice that their gain was worth grandma’s loss. argh.
It’s another case of some private entity unilaterally declaring the value for grandma’s data (as ‘one year of credit monitoring’).
And I must point out, it was 16 years.. not 4 years, not ‘current students’.. but 16.. or “as much data as they could scale up to”. I guess it’s good it happened at 16 years, rather than when the scale was larger.
I seem to spend most of my day completely baffled by the stupidity of very smart people.
argh.
It’s worth looking at the difference between hacking a home router, and hacking target, UofM, or LVSands. If someone hacks grandma because grandma didn’t protect her router, then it’s a non-scalable event. It effects grandma, and historically, that is easy for the banks, merchants, and society to cover.
When we scale up all of the grandmas into one basket it’s a different matter. For one thing, grandma didn’t have a say in her risk. For another, we have another party determining valuation of her data (it’s a moral hazard). We also make it something that the banks, merchants’ and society has a harder time covering. When everyone has insurance for the same event, when that event happens, nobody can cover the policy.
Yet the ‘big data’ insanity is determined to scale up. And why not.. they are just gambling with Grandma’s data. The perception is that grandma’s data is valuable in it’s own right.. that database is viewed as an asset based on monetizing it.
If we view ‘big data’ in terms of monetizing, there is little surprise the hackers do what they do; they can monetize it faster and better. So while Goldman sachs will front run grandma and steal her retirement .001 cent at a time over years, the hackers take a more direct route.
I suppose to grandma it really doesn’t matter if a hacker gets her or Goldman sachs (or LVSands profiling her so they can better ‘market’ to her). So great, grandma fixes her home router, she can sleep at night.. but she really isn’t any safer.
anyway, sorry for venting on your blog.. I just think the Very Smart People don’t get it. Or perhaps they do, and they were just hoping to rip off grandma before the hackers did.
re:”I seem to spend most of my day completely baffled by the stupidity of very smart people.”
That may be a mistake, assuming these people are smart. IMHO, they are greedy, corrupt and only minimally smart. The banks know enough to corrupt government and rig the game in their favor but is that really “smart” or simply the amoral behavior of miscreants? They hoard all the data they can get, whether it is valuable or not, because one day it may be. That’s not smart in my book.
I estimate that 90% of Americans are macro-economically illiterate (see MMT). So let me rephrase your statement to “I seem to spend most of my day completely baffled by the stupidity of people.”
@Lee Church
“offering credit monitoring for a year seems like an insult”
It’s worse than that. All they offer is monitoring. If you are a victim of identity theft, you will be forced to hire an attorney and write a large number of letters to creditors which the identity thief has unleashed on you. The process will take years. The credit monitoring services do not provide any assistance with that. Yes, they will probably give you a heads-up on every attempt to soak you, but you will clean-up the mess on your own. Not to mention the mess regarding the Social Security Administration, the IRS, and other government entities. No one ever mentions this.
“i’m fairly sure it’s not ‘forever’”
So far it has been forever for me, as the credit monitoring service keeps extending my free service each year it expires (the fact that I have not sent them any payment to extend their service may play a role). I was a victim of a hack. I immediately put a credit freeze on my accounts with the big three credit agencies so no one was able to take advantage of my situation. And my hack involved HIPAA data, so those of you who think HIPAA laws have teeth are deluding yourselves.
“Seems to me we have national disease of what I call ‘data hoarding'”
This is because we have no real laws to protect personal data. If we began to see CEOs being perp-walked, things would change. Greed kills.
It’s just a matter of time before everyone in the U.S. has his/her personal data stolen. My data was stolen from a Blue Cross / Blue Shield entity which kept application data on a non-secure website (this has nothing to do with Obamacare). Target looks like a class valedictorian compared to BC/BS.
To paraphrase an old joke — there are only two kinds of people: those who have had their identity stolen and those who will.
Note – the credit monitoring services all come with identity fraud restoration assistance — an agent will help guide a victim with the steps to take to file disputes and clear the fraudulent accounts from their credit files.
That said, I agree that one year is not long enough.
I would also argue that credit monitoring is not the ultimate and only tool to detect fraud.
But often the service provider is one of the three credit bureuas so credit monitoring can be offered cheaply to the retailer or university who experienced the breach and each of those entities wants to pick the lowest cost option…
I plan to pressure my representatives to protect everyone’s identity for free! There should be a law on that anyway. It is ridiculous that the victim has to pay, and pay forever for something of no fault on their own!!!
I’ve seen poor sots fight for their rights from arrest records the criminals used when they’d get busted for various assorted violations. They’d be fighting this for 10 years, then the crook would get out of jail and the whole process would start over again. WTF!!! Our stupid and worthless congressmen need to get off their butts and DO SOMETHING!
Am I the only one reading this that’s actually been in at least one store of all four chains mentioned?
Seems to me the credit cards from the demographic that goes to Target, Michaels, and especially NM would be good for a lot more money than those from Harbor Freight. HF sells lots of tools and hardware of medium to poor quality, and I’d bet cards stolen from there would on average yield significantly less return per card before hitting account limits or even being “flagged” for unusual activity by the provider.
I’d doubt if this accounts for all the differences, but…just a suggestion.
Dan,
Assuming a card used at Harbor Freight is worth less than one used at any other store is absurd.
If I bought some candy at the dollar store with my card that has, for example, a $10,000 limit would that not be worth more than the maxed out card someone used at NM?
You can’t simply judge the value of the card based on the store it’s used in.
In the micro sense of course you can’t tell a difference. But in the macro sense, I’d be quite surprised if the “value” of a large quantity of cards is completely unrelated to the demographic/economic/social group(s) served by the merchant they’ve been stolen from. For a number of reasons, I’d be quite happy if someone with hard data could prove me wrong.
A clue might come from comparing the number of “premium” or “prestige” cards in each group. For example, you’d have a very hard time convincing me that a big set of numbers with a significant percentage of AmEx cards, especially AmEx Golds if they can be distinguished by the number alone, would have the same “value” as a group with lots of Discover cards issued through Wal-mart.
In comparing the NM group to the HF group, I’d be astounded if there were all that many personal AmEx Gold numbers in the HF set.
Do you know why card sellers haven’t started offering blended bases yet? It seems like the obvious thing for them to do, knowing their shops are under surveillance, is to start mixing cards from a bunch of different sources. That way, it’s not such a trivial task for fraud prevention folks to buy a set and find the common retailer.
Is their inventory just too fragmented with not enough cooperation to create base blends, or is there some other value that isn’t obvious from, err, “single malt” bases?
“Harbor Freight breach; the company has not responded to requests for comment”
Target should see if the same malware and methods were used and then sue HF for not disclosing them to security professionals.
why don’t these banks and retailers in general have mirror images of their networks setup in a honey pot fashion to analyze and sinkhole these activities? duh. seems to me that makes more sense than always being in a reactive mode on the security end of payment card activities these criminals are engaging in on the interwebs. come on people, think. always putting out fires and never seeing it coming. think. think like the criminal. only, have the moral compass to thwart these derps!
Maybe you should start a company doing just that? It would make sense that places like Target who just don’t have time or resources to do proper in house security, should simply hire a contractor to do it for them. I would think this could be done cheaper than hiring internal security above what they already have.
Big data is all the rage these days, why not big security data?
Hello Brian. In the graphic “Tortuga” point is between 0.7 and 0.8, not 100% valid rate like your post says (” Cards in the Tortuga base were advertised as “100 percent valid,”)
Regards!
I think Google’s charts generator buried the first Tortuga data point in that graphic under the first orange dot for Barbarossa, since they were listed on the same date. I assure you that they were advertising Tortuga as 100 percent valid at that point.
Brian,
To get technical, the graph says “percentage value” so 1 would be 1%, not 100%, but the graphs are consistently done that way and the screen shots have valid rates of 65%.
How come these crooks have not been caught yet, especially since they are selling their spoils in public view? The way they have named their batches, their language, etc should offer lots of clues if someone has bothered to profile them. I’m willing to bet that they are reading this blog. Analysing who has read this blog from which parts of the world may help too.
Oh I’m sure the authorities are hot on the trail – but I predict it will be an exasperating process, and I’m sure they are thinking outside the box like many here on KOS are doing with their posts.
I just have a feeling these criminals are truly organized, and not the typical careless braggarts that usually make the pages here on KOS. I’m sure they are keeping a very low profile while they plan their next attack – and actually I bet we’ve not heard the results from many other already successful attacks, because retailers are so closed mouthed about it. If Brian hadn’t blown the whistle, we’d still be clueless as to what happened to our credit?!?!
Banks can’t just willy-nilly close cards. Guess what happens when you decide to close thousands or millions of cards all at once? That’s right, really pissed off clients who went to get grocery’s or buy gas and their card was declined.
Now you’ve not a flood of calls to your customer support. Guess what people hate even worse than card fraud or declined transactions? Right again, waiting on hold for hours.
Obviously banks can’t do this because they would probably take more loss from closed accounts than they would have if they just closed cards as fraud is detected on them and take a loss to make the clients account whole.
It seems to me that to do a large re-issue of cards you would have to wait for the client to get the new card and activate it before you can close the old card. That just make since. This way you’ll probably get most of the cards closed before they see any fraudulent transactions.
You know what doesn’t make any since to me. Target gets breached. Banks take all the loss. Walmart’s sales go up. Do you think Walmart or other big box retailers that see 10 transaction on a single card for 10 $100 gift cards in less than 2 minutes, then the same activity at another store 20 minutes away, are not aware that thous transactions are fraudulent? Guess what, they know its fraud but they don’t care because they are making money.
Folks who are hyped on ‘big data’ should re-read the Warren Buffett Gotrocks story. Substitute “GotInfo” for the family name and it’s the same story.
Please refer to page 19 of the 2005 annual letter to shareholders)
http://www.berkshirehathaway.com/letters/2005ltr.pdf
There are uses for these data collections but most folks seem to have it backwards. There is silly notion that only the hyper helpers should have the data, not the gotrocks/gotInfo family trust (government).
I suspect that we will repeat the story of the x-ray machine. When first invented we put it everywhere, including shoe stores for aiding in size selection. We look back and say “that was stupid” now, but not many can look forward. Heck we can even see that the whole ‘big data’ craze is financial crisis 2.0 in the making. With shoe store x-rays we were limited in how much we could scale up. Even with CDOs and CMBSs, finance folks were limited in leverage. IT folks can be even better though, we can scale up way more, limited only by storage and processing power. yeah! For those that want a puzzle, think about the difference of pulling future earnings forward vs moving the future view forwards (predictive ‘big data’).
This isn’t going to end well.
Actually I think it will take a “big data” solution to solve a big part of the problem. Most retailers just want to be good at providing goods and services that people will buy, and not become the ‘Brinks Security Service’ of the world wide web. It will take a big company that can contract security and provide big data in a centralized repository with “junk yard dogs” guarding it like a hawk to be a truly future solution to these problems! The bigger the company the cheaper it would be to contract through them, and let them handle these problems.
Much of the analysis and implementation could be automated with a “Watson” type IBM artificial intelligence interface!! In fact if I were IBM, I’d be sending salesmen to Target, and every other big box retailer with this idea – it could be the biggest resurgence of Big Blue since the Hollerith 1890 tabulating machine! HA! 😀
It doesn’t negate the problems at the POS level, but if a big enough company took this on, they could provide the hardware as well and let the CIO of a big company like Target sleep at night.
Mensch, you wrote “It seems to me that to do a large re-issue of cards you would have to wait for the client to get the new card and activate it before you can close the old card.”
My provider sent a new card but kept the old one alive until I could activate the new one. The new card had a new CVV and an expiration pushed ahead a little bit, but same 16 digit number. IMO it was only partial protection, I was worried about the online use of my card with merchants that don’t require the CVV and allow multiple attempts to get the expiration date right. Anyway, just wanted to mention this because it is one way to update a card without any disabled period.
One of my banks did this for me as well. They got hit with about 5000 fraudulent charges in the 1st three weeks after the breach, and started a massive reissue campaign immediately afterward. Ironically I had just received my new card from them, but another followed with a different number and PIN. Now I’ve got another pin I have to memorize and get used to, but I am pretty impressed with how well their anti-fraud system works at it is – for many years it was better than ones issued by the big card companies.
I didn’t give Discover Card a chance to prove if their new anti-fraud detection could prevent the next breach, I simply closed the account. I had too many cards anyway, and was only keeping theirs for the Online Secure Account numbers system they had also dropped at the same time as the Target breach! Curiously bad timing! :/
Walmart et all has no idea that the same “card” is used at different stores in a too short time frame. The issuing bank would know and I’m pretty sure this raises an automatic fraud alert these days. That said, 10 years ago I had a debit card cloned and the fraudsters made a card and went to a mall in Australia to purchase about 6k of jewelry at two stores. A purchase pattern I never had. Further, this occurred a few hours after I had purchased gas with the same card in the US. By pure luck I had logged onto my account and saw the bogus authorizations and checking debit the same day the crooks made the charge. My debit card was still active and there was nothing from the bank about the charges. I called and shut it down and the bank put funds back in my checking but I believe the crooks got away with it. Credit monitoring is irrelevant to this sort of fraud and offering it is just a “feel good” customer pasification program.
While this is the most common fraud and isn’t as damaging as ID theft where someone takes over your identity to open and run up lots of debt leaving you to deal with it. That’s where monitoring comes in. It is very valuable against this kind of ID theft.
Credit monitoring is a good way to protect against real ID theft, before the fact, not so much after the damage has been done. An unrecognized inquiry from a new creditor should immediately result in one putting a fraud alert credit freeze on the credit reporting companies as well contacting the inquiring creditor to shut down the account. Prevention works way better than repairing the damage later.
Even invalid cards can be valuable, especially if it was stolen along with your address and phone number. When my card was stolen a few years back in a breach, I had my card replaced after about $1000 in fraud charges. A few days after I received my new card, I started getting phone calls from an automated system cliaming to be my credit card company following up on my recent fraud report, and asking me to confirm my credit card number. I knew that my credit card company would never call me and ask for my number, but I just have to wonder how many people fall for that.
Just remember, your credit card company will never call you and ask for your credit card number.
There is something I don’t understand and I think wasn’t yet explained: Cards cloned using data from Target can only be used in card present transactions right ? If the validity is now around 50% how can a buyer of this data clone some cards and walk into a shop to “buy” some high-ticket items ? Isn’t he arousing any suspicion when one or more cards are declined ? Wouldn’t this be a great opportunity to apprehend some miscreants at least at this end of the fraud-chain ? After all, if a shop have security personnel (for example to deal with shoplifters) same personnel could also keep would-be fraudsters attempting to use stolen cards until police arrives. That unless the shop has zero incentive to do something about it because they do a sale and the fraud is eaten by the bank.
No, they just go into big box stores that let the customer check out at the register themselves. So, the customer swipes one card, it doesn’t work, they get another card out. Tons of people have multiple cards in their wallets and will pull out another if the first one doesn’t work. Granted, if this happens more than a few times at the same register, it might raise suspicions, but remember you’re likely dealing with a cashier who is making minimum wage, and they generally don’t get paid to care about this stuff.
Quick thought experiment.
You are an Upstanding Citizen with sterling credit that has never had even a slight hassle with any of your cards (I said it’s a thought experiment). You’re at a cashier in a Best Buy paying for a nice new laptop. For some unknown reason your credit card or cards are declined. What would you do?
Now ask yourself what you would do or feel if you were a spectator to the above or the harried and underpaid clerk behind the counter. Would you be automatically suspicious? Maybe. But just as likely sympathetic.
The above DOES happen to innocent people.
I sincerely doubt that all the people using clones of stolen cards are too stupid or ignorant to put on a plausible act.
Or you can just check them at ANY pay-phone or online checkers just before you go “Shopping”.
I know one bank that was aware of the Target breech that told customers to not worry about getting a new card because they were monitoring cards for fraudulent activity and they would catch the fraud quickly. The bank was told just a few weeks ago that they had over 10,000 accounts on just 3 carding forums. The bank is a smaller bank and finally just last week started re-issuing cards after the information was provided to them via screenshots from kadaffi’s website etc.
I think a lot of these banks are just really slow and don’t understand the extent of what these people buying the cards will go through or how long they will wait to cash in.
My card is with one of the biggest providers and I was a bit surprised by their apparent lack of concern when I called them. They assured me that I wouldn’t be responsible for fraudulent charges and suggested I set up alerts. I know it’s expensive for them to reissue such a massive number of cards. But later on someone there must have figured out just how many of their cards were on the market, because I received an unsolicited notification that I’d be receiving a new card due to the Target breach. (And then only the CVV was changed. I requested a totally new number right after that.)
Police: Monterrey couple went on spree in RGV using card numbers stolen in Target breach http://www.themonitor.com/news/local/article_99f78ff6-81d6-11e3-9406-001a4bcf6878.html
My card was valid for two months, I think, until the provider changed the CVV and then I requested an entirely new card number. I have no evidence of it, but my gut feeling is that I was in the majority (i.e., that most cards were valid in the initial month or two after the breach).