Tag Archives: sans internet storm center
Microsoft Patch Tuesday, May 2023 Edition
Microsoft Patch Tuesday, February 2023 Edition
Microsoft is sending the world a whole bunch of love today, in the form of patches to plug dozens of security holes in its Windows operating systems and other software. This year’s special Valentine’s Day Patch Tuesday includes fixes for a whopping three different “zero-day” vulnerabilities that are already being used in active attacks.
Patch Tuesday, November 2022 Election Edition
Let’s face it: Having “2022 election” in the headline above is probably the only reason anyone might read this story today. Still, while most of us here in the United States are anxiously awaiting the results of how well we’ve patched our Democracy, it seems fitting that Microsoft Corp. today released gobs of security patches for its ubiquitous Windows operating systems. November’s patch batch includes fixes for a whopping six zero-day security vulnerabilities that miscreants and malware are already exploiting in the wild.
Microsoft Patch Tuesday, August 2022 Edition
Microsoft today released updates to fix a record 141 security vulnerabilities in its Windows operating systems and related software. Once again, Microsoft is patching a zero-day vulnerability in the Microsoft Support Diagnostics Tool (MSDT), a service built into Windows. Redmond also addressed multiple flaws in Exchange Server — including one that was disclosed publicly prior to today — and it is urging organizations that use Exchange for email to update as soon as possible and to enable additional protections.
Microsoft Patch Tuesday, December 2021 Edition
Microsoft, Adobe, and Google all issued security updates to their products today. The Microsoft patches include six previously disclosed security flaws, and one that that is already being actively exploited. But this month’s Patch Tuesday is being overshadowed by the “Log4Shell” 0-day exploit in a popular Java library that web server administrators are now racing to find and patch amid widespread exploitation of the flaw.
Patch Tuesday, October 2021 Edition
Microsoft today issued updates to plug more than 70 security holes in its Windows operating systems and other software, including one vulnerability that is already being exploited in active attacks. This month’s Patch Tuesday also includes security fixes for the newly released Windows 11 operating system.
Microsoft Patch Tuesday, August 2021 Edition
Microsoft today released software updates to plug at least 44 security vulnerabilities in its Windows operating systems and related products. The software giant warned that attackers already are pouncing on one of the flaws, which ironically enough involves an easy-to-exploit bug in the software component responsible for patching Windows 10 PCs and Windows Server 2019 machines.
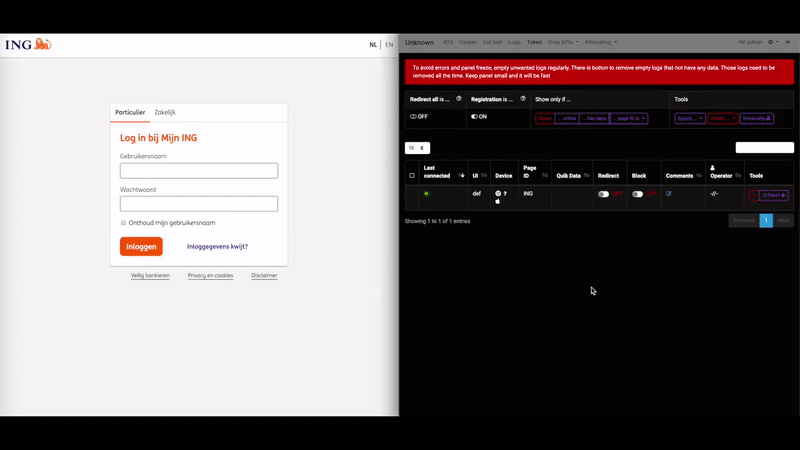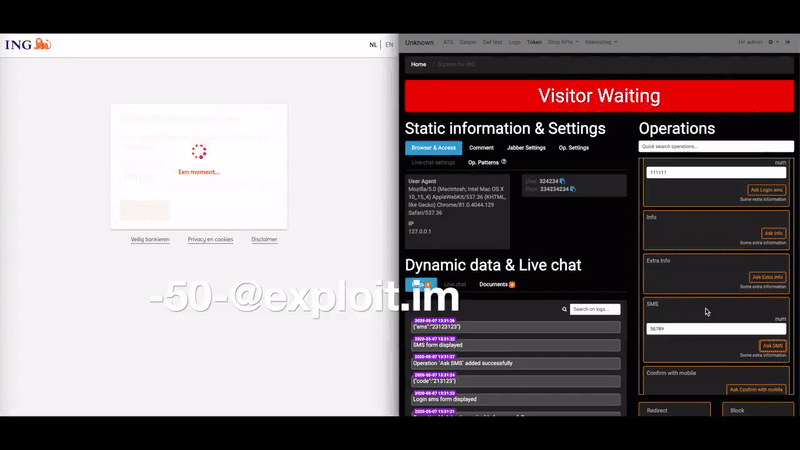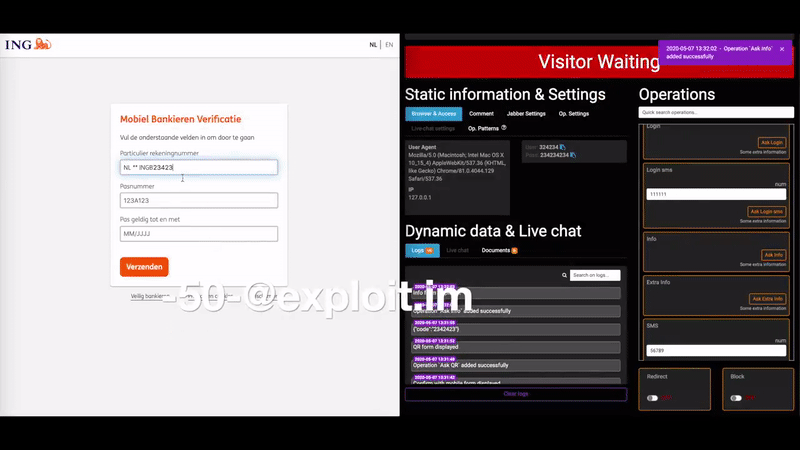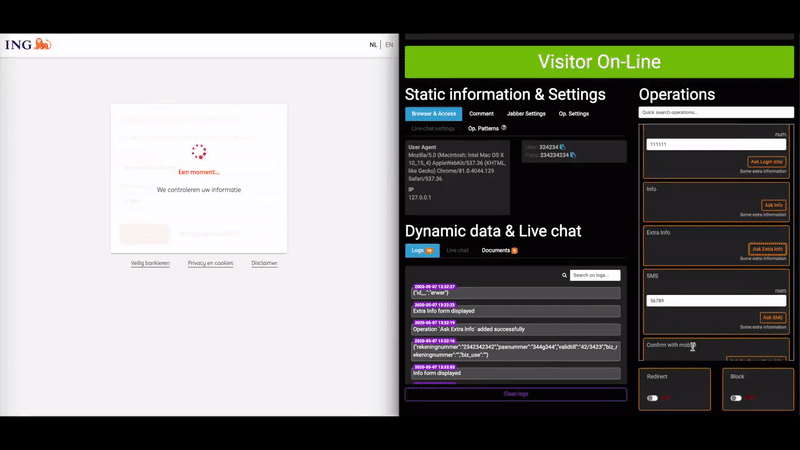
Arrest, Raids Tied to ‘U-Admin’ Phishing Kit
Cyber cops in Ukraine carried out an arrest and several raids last week in connection with the author of a U-Admin, a software package used to administer what’s being called “one of the world’s largest phishing services.” The operation was carried out in coordination with the FBI and authorities in Australia, which was particularly hard hit by phishing scams perpetrated by U-Admin customers.
Patch Tuesday Lowdown, April 2019 Edition
Microsoft today released fifteen software updates to fix more than 70 unique security vulnerabilities in various flavors of its Windows operating systems and supported software, including at least two zero-day bugs. These patches apply to Windows, Internet Explorer (IE) and Edge browsers, Office, Sharepoint and Exchange. Separately, Adobe has issued security updates for Acrobat/Reader and Flash Player.