With new security updates from vendors like Adobe, Apple and Java coming out on a near-monthly basis, keeping your Web browser patched against the latest threats can be an arduous, worrisome chore. But a new browser plug-in from security firm Qualys makes it quick and painless to identify and patch outdated browser components.
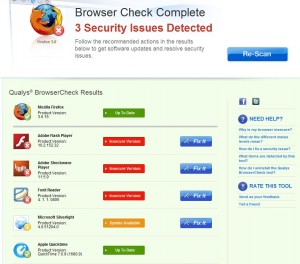 The Qualys BrowserCheck plug-in works across multiple browsers — including Internet Explorer, Firefox, Chrome and Opera, on multiple operating systems. Install the plug-in, restart the browser, click the blue “Scan Now” button, and the results should let you know if there are any security or stability updates available for your installed plug-ins (a list of the plug-ins and add-ons that this program can check is available here). Clicking the blue “Fix It” button next to each action item listed fetches the appropriate installer from the vendor’s site and prompts you to download and install it. Re-scan as needed until the browser plug-ins are up to date.
The Qualys BrowserCheck plug-in works across multiple browsers — including Internet Explorer, Firefox, Chrome and Opera, on multiple operating systems. Install the plug-in, restart the browser, click the blue “Scan Now” button, and the results should let you know if there are any security or stability updates available for your installed plug-ins (a list of the plug-ins and add-ons that this program can check is available here). Clicking the blue “Fix It” button next to each action item listed fetches the appropriate installer from the vendor’s site and prompts you to download and install it. Re-scan as needed until the browser plug-ins are up to date.
Secunia has long had a very similar capability built into its free Personal Software Inspector program, but I realize not everyone wants to install a new program + Windows service to stay abreast of the latest patches (Secunia also offers a Web-based scan, but it requires Java, a plug-in that I have urged users to ditch if possible). The nice thing about Qualys’ plug-in approach is that it works not only on Windows, but also on Mac and Linux machines. On Windows 64-bit systems, only the 32-bit version of Internet Explorer is supported, and the plug-in thankfully nudges IE6 and IE7 users to upgrade to at least IE8.
Having the latest browser updates in one, easy-to-manage page is nice, but remember that the installers you download may by default come with additional programs bundled by the various plug-in makers. For example, when I updated Adobe’s Shockwave player on my test machine, the option to install Registry Mechanic was pre-checked. The same thing happened when I went to update my Foxit Reader plug-in, which wanted to set Ask.com as my default search provider, set ask.com as my home page, and have the Foxit toolbar added.



Call me crazy… but does it make sense to install an add-on to increase the security of your browser, when installing an add-on inherently increases the attack surface?
Saw this one coming. I think like everything in security, there are trade-offs. Yes, adding another plug-in necessarily increases the attack surface of the browser. I haven’t peeked at the code that runs the browser check functionality, but I would wager that it is far less complicated and code-heavy than, say, Adobe Reader or QuickTime.
Also, my gut tells me this plug-in is likely to be more useful to the casual user who doesn’t think in terms of “attack surface.” 😉
True true…
I suspect you’ve covered Secunia’s PSI then? And maybe openvas (with ovaldi)?
I’ve written and mentioned PSI on many occasions in this blog. The last review of it was in September:
http://krebsonsecurity.com/2010/09/revisiting-secunias-personal-software-inspector/
Firefox has something like this at http://www.mozilla.com/en-US/plugincheck/, though I believe it’s only checking Firefox add-ons.
Thanks for the reminder, Tom. It goes beyond Mozilla/Firefox. I wrote about Mozilla’s checker here:
http://krebsonsecurity.com/2010/05/mozilla-plugin-check-now-does-windows-sort-of/
Brian, the plugin check webpage is supposed to be cross-browser. The recommended minimal browser versions according to the webpage itself are Firefox 3.6, Opera 10.5, Safari 4, Chrome 4, or IE 8. They admit however that support for Internet Explorer is limited.
I am also weary of installing additional plug-ins into the browser, even if they come from from security companies. These plug-ins are commonly being driven by marketing departments with the goal “it must be dead easy to use” while security testing is neglected. What they are doing is mostly covered by the plugincheck website, only exception being the version of the browser itself – other than for Internet Explorer a webpage could check that without the need of any plugins.
why even use the internet at all if your that paranoid
Go to ninite.com to download software and see if you get the junk added on that adobe and others want to sneak in on you.
Also worth mentioning is Google’s secbrowsing.appspot.com (built-in in Chrome).
A list of supported plugins would be nice; if it’s limited to the usual five or six then it’s not much better than Google’s and Mozilla’s services, except perhaps for IE support.
Most of the questions in the comments so far were answered in the story, including this one.
“(a list of the plug-ins and add-ons that this program can check is available here).”
https://community.qualys.com/docs/DOC-1542#s2
Whoops! Missed the link, sorry for the redundant question.
Anyway, the list seems nice, but not really that comprehensive (it’s missing Office, Unity, to name just a couple from the top of my head). I wonder if they will expand the support, perhaps a “submit my list to server” feature would have been useful.
The ToC for installing this plug-in is here
https://browsercheck.qualys.com/sua.php
i have writtin this in javascript for all websites at my blog. it checks the version of the plugin and the current version. its a simple bar at the top. you can test it here: http://www.startseite.nfkl.de/
sry. its in german. 🙂
Ach du Lieber Himmel! ]:)
Brian –
Secunia is great, especially if you use the OSI option (sends you an email advisory) which doesn’t require installation of the Secunia PSI program. But for me, best of all is filehippo.com which at about 8am EST every morning publishes that day’s updates to everything – browsers, plugins, anti-malware, audio-video programs and more. I’ve made it a habit to check their website every morning right after I check on the weather. It’s a snap, and they link directly to the udate sites that you are relevant to what you use.
I use the FileHippo Updater too. I run it first thing every morning. It only takes a few seconds.
As was pointed out on a recent thread, if you don’t want to a beta tester be sure to set it to hide beta versions.
Ugh! Problem with Secunia’s OSI is it requires Java! No thanks. Java has been on my software blacklist for years. We use it extensively at work and it’s just a major PITA all around. Unless you absolutely have a need for it, junk it! To install it just to run Secunia’s OSI = FAIL! It just raises your system’s attack surface to0 much to justify any benefits. You’re better off with Secunia PSI! 🙂
So xAdmin;
Are you saying you need java for more that graphing on the OSI version? I’ve run PSI without java many times. I can do without the graphs.
Just saying that OSI requires Java and that if you’re going to install Java JUST for OSI, it’s not worth it, use PSI instead as it does NOT require Java. Now if you need Java (for something else) and thus already have it on your system, then so be it.
Personally, I made the decision a while ago that nothing is worth the risk of having Java installed (it never gets installed from a clean install of the OS). The few times I’ve come across something that wants Java, a quick search found an alternative that didn’t.
Secunia OSI System Requirements:
http://secunia.com/vulnerability_scanning/online/system_requirements/
It is ironic that a security minded company like Secunia would require such!
Thanks for the link and writeup, definitely something that has useful functionality. However, at least in Chrome, the permissions it requests are a bit extreme. It requests access to “all data on your computer and the websites you visit.” Not something that’s easily justified.
Varjohaltia –
I haven’t had that experience of filehippo asking me anything. You may be referring to what happens when you install almost any extension for Chrome at the Chrome extension site. That aside, there’s no reason to worry about updating Chrome; if you have it installed, it updates itself automatically, so you can just ignore any update notice for Chrome from filehippo or Secunia or anyone else. Chrome also automatically updates Adobe Flash player, so you can also ignore advisories about that if Chrome is the only browser you use. This gets a bit complicated because not only do you have to install different versions of Flash for IE on the one hand, and for Firefox, Opera, etc. on the other, but Chrome’s automatic update often installs a version of Flash that is newer (has a higher number) than anything shown on the Adobe update site. I’ve been tracking this oddity for a while and it doesn’t seem to be anything to get worried about. Like a lot of small annoyances on the web, it’ll get sorted out in due course.
Chrome doesn’t install for all users in x64 Vista, so I like to be reminded by File Hippo to go to the Administrator’s account and update Chrome from the browser. You are correct, that it is easier to do it from Chrome; but it doesn’t work automatically on standard accounts if you don’t have it installed that way, which I do not, and actually haven’t tried.
Chrome’s sandbox doesn’t blend well with the x64 kernel on standard accounts, so I see no reason to use it – FireFox 4 is so much more wonderfull in my opinion! Thanks for your post!
So, does this mean if you have Secunia PSI in operation you are covered on this? We have a few java-dependent accounting programs, so need that software.
I use Secunia PSI, but I also use File Hippo because it can sometimes offer the updates ahead of other sources. This article shows that there is more than one way to get information, and possibly update eariler than using other methods.
The earlier you can update an application the more likely you may mitigate a zero day vulnerability. The system isn’t perfect, but what is?
Secunia PSI has been very good to me on coverage, but can be three or four days behind other sources. Fortunately it does automatically update some programs even while you are using another account! This is a very good rivet in the armor one uses to build blended defenses.
I type a comment, send it, and it goes, but does not appear on the blog. This has happened in the past. I use NoScript with only KrebsOnSecurity allowed, all the other things are blocked. Could this be the cause? I’ve allowed everything to try to send this. If so, which other items are needed to comment?
The comment appears, so NoScript was the offender. But I’d still like to know which items are needed, and I will allow them but not the others.
I thought I would compare/contrast Qualys with Mozilla Plugin check.
Qualys identified my Flash, 10.2.132.26, was insecure while the Plugin check said I was up-to-date. I then ran Secunia PSI which confirmed my installed version was out-of-date and that is correct.
I was relying on the Plugin check to prompt me that I was at risk so I need to be more careful
Brian
I had a similar experience. I have been promoting the Mozilla tool for quite some time. But in my case, Mozilla Plugincheck indicated my Flash was up-to-date, and Qualys said I was slightly behind. Time to add the Qualys tool to the toolbox.
E
All went well with Firefox, Chrome and Opera but when run in IE8 it concluded I needed to upgrade . . . to IE7!
Well, -7 thumps down for my post…
I just ran the scan on Safari on my Mac, and interestingly enough it did not require anything to be installed. BrowserCheck found 6 plug-ins, letting me know that Flash and Silverlight were both out of date.
So why would BrowserCheck require a plug-in on Windows?
There’s two versions of the scan. One you run from the browser at the website, the other you download and run on your machine.
I wonder if Brian has noticed that LazyScripter has lifted this post in its entirety, without attribution.
I’ve tried to add it to Mozilla via the Add-ons menu option rather than downloading it from Qualys directly, but it’s not listed there. I’m wondering if will ever be rubber-stamped by Mozilla and added to their endorsed list. I know that Brian will never point us toward anything when there is even the remotest doubt it might be malicious, but being something recently appeared I will wait for a while for others to beta-test it. If someone from Qualys reads this post, perhaps can comment if there is any attempt in progress to certify it with Mozilla Foundation.
This is a russian online service wich checks your browser and plugins in it. It’s a free service from firm specialized in vulnerability scanning. Enjoy 🙂
http://www.surfpatrol.ru/report.aspx
дурачок в апреле!
Wow, awesome little plugin. Thanks to this I finally upgraded Chrome on my PC from version 7.x to 10.x. It had been giving me all the update prompts, but never actually actually updating so I had no idea I was behind. Had to delete chrome.exe and rename new_chrome.exe manually for it to finally happen.
Lesson of the day: Be more careful adding SecuniaPSI exceptions (which I had done for Chrome), that constant warning you’re getting may actually be more than just the google updater taking its time in removing old install locations as you had thought at the time.
It can also detect Zero-day (no available patch from vendor) issues! Currently it detected that Flash is vulnerable on my Android phone and Chrome browser on my PC.