The previous two posts on this blog have featured stories about banks buying back credit and debit card accounts stolen in the Target hack and that ended up for sale on rescator[dot]la, a popular underground store. Today’s post looks a bit closer at open-source information on a possible real-life identity for the proprietor of that online fraud shop.
Rescator[dot]la is run by a miscreant who uses the nickname Rescator, and who is a top member of the Russian and English language crime forum Lampeduza[dot]la. He operates multiple online stores that sell stolen card data, including rescator[dot]la, kaddafi[dot]hk, octavian[dot]su and cheapdumps[dot]org. Rescator also maintains a presence on several other carding forums, most notably cpro[dot]su and vor[dot]cc.
![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator’s email flood service at the bottom; this will become important as you read on.
![Rescator, a.k.a. "Hel" a.k.a. "Helkern" the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.](https://krebsonsecurity.com/wp-content/uploads/2013/12/vor-1edited-600x414.png)
Rescator, a.k.a. “Hel” a.k.a. “Helkern” the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.
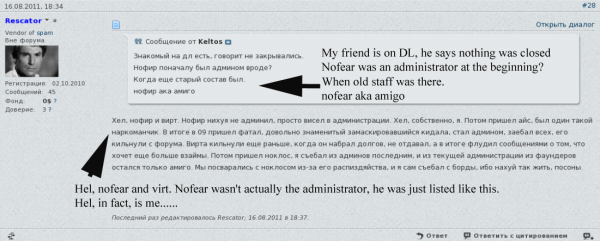
The only darklife member who matched that nickname was “Helkern,” one of darklife’s three founders. Darklife administrators were all young men who fancied themselves skilled hackers, and at one point the group hacked into the venerable and closely-guarded Russian hacking forum cih[dot]ms after guessing the password of an administrator there.
![Darklife admin "Helkern" brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.](https://krebsonsecurity.com/wp-content/uploads/2013/12/cihhacked-600x470.png)
Darklife admin “Helkern” brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.
And a self-portrait of Helkern:
So if Helkern is Rescator, who is Helkern? If we check at some of the other Russian forums that Helkern was active in at the time that Darklife was online in 2008, we can see he was a fairly frequent contributor to the now-defunct Grabberz[dot]com; in this cached post, Helkern can be seen pasting an exploit he developed for a remote SQL injection vulnerability. In it, he claims ownership of the ICQ instant messenger address 261333.
In this introductions page from a Russian language gaming forum, a user named Helkern also was active in 2008 and claimed that same ICQ address. Helkern said his email address was root@helkern.net.ua, his Skype address was helkern_skype, and that he lived in Odessa, the third-largest city in Ukraine. Helkern — going by his shortened username “Hel,” also was a VIP member of xaker[dot]name. In this cached post we can see him again claiming the 261333 ICQ address, and pointing out to other members that his real nickname is Helkern.
A historic WHOIS lookup ordered from domaintools.com shows that helkern.net.ua was first registered in 2008 to an Andrey Hodirevski from Illichivsk, a city in the Odessa province of southwestern Ukraine.
I located a relatively recent Livejournal profile (ikaikki.livejournal.com/profile) for an Andrew Hodirevski from Odessa, Ukraine that includes several profile pictures which are remarkably similar to the photos of Helkern leaked by the cih[dot]ms guys. That profile (“ikaikki“) says Hodirevski’s email address is ikaikki@livejournal.com, that his Jabber instant message address is ikaikki@neko.im, and that his Twitter account is “purplexcite” (that Twitter has since been deleted). In almost a dozen posts on LiveJournal, Hodirevski talks about his interest in Java programming, and even includes a few pictures of himself attending an instructional class on Java.
The same anime profile image for Andrew’s LiveJournal page is also on the LinkedIn profile for an Andrew Hodirevski from Ukraine, and the two pages share the aforementioned Twitter profile (purplexcite). Andrew’s LinkedIn page also says he is the administrator and Web developer at a hosting company in Ukraine called ghost.ua.
That site is no longer online, but a cached copy of it at archive.org shows that the business is located in Odessa at this address, and the phone number +38 (048) 799-53-13. Ghost.ua lists several pricing plans for its servers, naming them after different despotic leaders, including Fidel Castro and Muammar Gaddafi (it is spelled “Kaddafi” on Ghost.ua). Recall as I mentioned at the top of this post that one of the clones of the card shop at Rescator[dot]la is kaddafi[dot]hk.
This page at it-portfolio.net lists an Andrey Hodirevski from Odessa with the same anime profile image, the “purplexcite” Twitter profile, and a Skype address by the same name. It says his professional skills include programming in Java, CakePHP and MySQL, among others. This Google groups discussion about CakePHP includes a message from an Andrey Hodirevski who uses the email address andrew@purpled.biz.
Purpled.biz is no longer online, but a cached copy of it from archive.org shows it was once Andrew’s personal site. Here we learned that Andrew’s current goals (as of 2010) were to get married to his girlfriend, buy the $20,000 Toyota Solara pictured below, move to Helsinki, and to achieve world domination. In order to accomplish the latter goal, Andrew jokes that he “will probably have to rob all the banks in the world.”
 After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
To bring this full circle, one of the many services that Rescator sells these days is a popular email flooding service at rescator[dot]me. Turns out, Yours Truly has already been the direct target of an attack launched through Rescator’s service; I wrote about it in this July 2012 story, Cyberheist Smokescreen: Email, Phone, SMS Floods.
I have no idea if Rescator/Helkern/Andrew was involved in hacking Target, but it’s a good bet that he at least knows who was. I sought comment from various contact addresses listed above for this individual, and received a reply from someone at kaddafi[dot]me who said he knew Andrew and would relay my questions to him. Ultimately, he came back to me not with answers, but with a bribe not to run my story.(1:48:35 PM) krebs//: hi
(1:48:44 PM) krebs//: brian krebs here
(1:49:05 PM) krebs//: trying to reach rescator
(1:49:11 PM) krebs//: aka andrey
(1:51:12 PM) krebs//: don’t believe it’s really krebs?
(1:51:15 PM) krebs//: http://krebsonsecurity.com/wp-content/uploads/2013/12/kaddaficon.png
(1:53:32 PM) krebs//: 🙂
(1:53:53 PM) krebs//: tyt?
(2:00:14 PM) kaddafi.me: Hello Brian 🙂
(2:00:24 PM) kaddafi.me has not been authenticated yet. You should authenticate this buddy.
(2:00:24 PM) Unverified conversation with kaddafi.me/Muammar started. Your client is not logging this conversation.
(2:00:30 PM) kaddafi.me: ooo you’ve got OTR
(2:00:37 PM) kaddafi.me: Afraid of NSA? )
(2:01:38 PM) kaddafi.me: Why do you want to talk to Andrew?
(2:03:46 PM) krebs//: i am more afraid of others
[Image] (2:03:56 PM) The privacy status of the current conversation is now: Private
(2:04:11 PM) kaddafi.me: Yeah well you should after someone sent you drugs from silkroad.
(2:04:24 PM) krebs//: 🙂
(2:04:59 PM) krebs//: you’re right of course, it’s andrew 🙂
(2:05:17 PM) kaddafi.me: What’s all the commotion about Rescator anyways?
(2:05:20 PM) krebs//: well i have a story about him going up tomorrow
(2:05:23 PM) kaddafi.me: Did you even notice other shops are selling same shit?
(2:05:32 PM) krebs//: sure
(2:05:46 PM) krebs//: but I’m not looking at other shops right now
(2:06:05 PM) kaddafi.me: Well you should )
(2:06:10 PM) krebs//: in time 🙂
Kaddafi promised a response by 10 p.m. ET yesterday. This morning, not seeing a response, I pinged this individual again, and received the following response:
(10:08:46 AM) kaddafi.me: Hi.
(10:09:19 AM) kaddafi.me: You better contact me from another jabber that’s not associated with your name, I’ve got an offer for you.
(10:11:12 AM) krebs//: why from a different jabber?
(10:11:33 AM) kaddafi.me: Because I’ve got an offer for you. So you don’t think I’m trying to play games and fool around with logs after you read my offer.
(10:11:52 AM) krebs//: what kind of offer?
(10:12:27 AM) $10.000 not to post your article
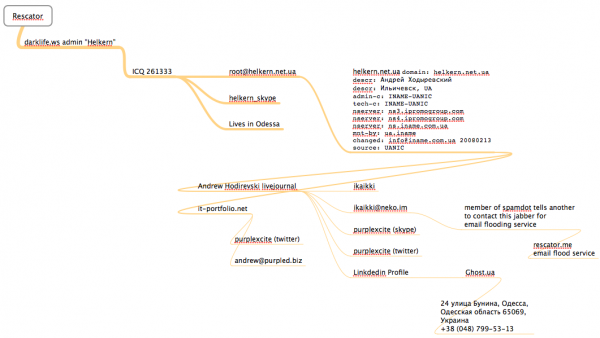
Obviously, I did not take him up on his offer, assuming he was not just messing with me. Here is a mind map I put together (using MindNode Pro for Mac) that outlines how much of this information was derived and connected.






![The email flood service at rescator[dot]me](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-me-news-600x360.png)

This is some fantastic piece of Journalism
Bravo! Fantastic piece of journalism and investigative reporting. Happy DIGG picked this up.
Your best article Brian !
continue I try doing same you with my blog but I have not your level !
if you need login from underground carding/hacking private forum tell me (cpro, vor, verified, infraud …), I have a lot
Well done, hopefully Target and other authorities will be able to act on such concrete information
If this guy isn’t on the run from Ukrane authorities, he ought to be. Nice job, Brian.
The word is that most of the former soviet countries have told these criminal groups they will not prosecute or cooperate with other countries as long as they don’t attack domestically and don’t attack nationals of their countries. In fact, there’s documented cases of these groups being hired by their countries intel units for state sponsored attacks. There’s a reson most of these attacks come from former soviet countries and why they’re never caught.
CJD, I have an idea, why don’t we filter out at the border these problematic IP addresses to those countries then?
To what avail? You can’t filter someone visiting a site in these countries, it’s too easy to use tor, VPN, or a proxy to get out, and just as easy to get in the same way, not to mention the money at stake is worth flying a hacker to the US or friendly country to perform the hack, and they don’t have to go that far. See Brian’s article on buying hacked accounts on corporate servers. If your in Russia it’s simple to buy access to a hacked server in say Germany and then execute your hack against US soil. Since in the case of the target hack they need to use the cards in store not online, it’s trival for someone to circumvent an ip block to a carding site, buy numbers and use them.
Not to mention the slippery slope of starting to censor the Internet. But when you consider even countries like china and Iran can’t fully block services that circumvent such blocks, it would be like a total ban on guns: only criminals will then have access. I can’t even fully block porn and anonymizing services in a network I fully control at work, much less do so at a national scale….
” To what avail? ”
To encourage cooperation of those countries with ‘thieves’ under their protection to clean up that purported ‘den of thieves’.
In the ‘old days’ the country would be blockaded – for playing host to pirates!
Are you aware of the early ‘colony’ states efforts in battling piracy on the high seas for instance?
‘He who does not remember history is bound to repeat it.”
– George Santyana
How would this encourage cooperation?
In the case of Target, the average citizen of those countries most likely aren’t going to visit a site that only has locations in the US and probably only ships within the US.
As for sites that operate internationally, I’m sure they wouldn’t want to block of an entire country of people.
And even if they did, the governments of those countries wouldn’t care because that would only help their own industries.
There’s a reason that some countries want to block Google, Facebook, Twitter, etc. and it’s not just about censorship, but rather their protectionist behavior helps their own versions of those services prosper and grow.
” How would this encourage cooperation? ”
The usual strong-arm tactics.
Or, you can roll over and just ‘take it’. You can repeat history any time you like, just don’t do it on my dime.
(Generally, the saber rattling beforehand gets them to seeing the light and cooperating on legit law enforcement matters such as this. )
Again, if you don’t know your history …
Not directly applicable, but mildly so, given your obvious American patriotism and isolationist leanings while talking about not repeating mistakes — how do you feel about The Bomb being dropped on Japan in WW2?
voksalna, have you forgotten: “The aggressor sets the rules” ? I think you have, and again, you are deficient in your study (or recall?) of history.
You and a lot of others are still stuck, thinking ‘in the box’ and not like a manager or higher level leader diplomat (or ‘general’ even.) Most of these solutions I propose are above your (and perhaps even my) ‘pay grade’.
I am both relieved and humbled by the fact that you seem to know so well what I know or do not know, what I do or do not do. You do not, so whether or not it is true, please do not assume, as it is insulting. I was hoping for a dialogue.
For instance there really is NO such thing as “repeating history”, nor can there be. Ignoring this is ignoring some of the basic tenets of military strategy and setting you up with assumptions that will lead to failure. The world is fluid, and time and technology and society, among other things, greatly change circumstances and thus affect potential outcomes.
Thank you. 🙂
I would also suggest the possibility that you, in fact, are the one thinking inside the box, only because you are inside the box you cannot see it.
“In the ‘old days’ the country would be blockaded – for playing host to pirates!
Are you aware of the early ‘colony’ states efforts in battling piracy on the high seas for instance? ”
And your point is?
Blocakdes were not effectrive then nor are they effective now.
There are several hundred piracy incidents every year all over the world.
The International Maritime Oreganization (IMO) even maintaines a website documenting the problem see IMO[dot]org
My point isn’t that countries sponsoring or harboring criminals shouldn’t face consequences, my point is, technically what you propose wouldn’t stop or even deter this activity, and would only serve to hurt legitimate business and Internet usage. It’s not as simple as just blocking a country’s ip addresses, as that is easily circumvented. The only way you could do so would be to have a US only Internet, with NO access to or from other nations, and that would only force criminals to come physically to the US, perform their hacks, and leave with the data.
I am curious, would you also prohibit phone calls? Emails? SMS? Communication at all? Are you in North Korea? You do realise the ease of connecting a modem (if you can find one) to another modem to bridge into the US net? Or just hopping from an unfriendly country without your “rules” to an country you consider “friendly” and without your “rules” (or again a modem, etc) to you? I am not sure you know how computers and technology works. It is okay, though, most people do not. 🙂
Blockade means blockade, voksalna.
It is meant to hurt until internal forces in the country hosting the pirates ‘take action’.
You and other still do not understand the dynamics that the figurative ‘blockade’ is meant to foster or inspire in the country hosting the pirate activity.
Are you coming closer to understanding yet? This internet traffic ‘blockade’ might only need to be proposed to be effective; even this thought you and a few others do not grasp. If just proposal of blockade is not enough, then one day of REAL internet blockade might be enough to to convince pirate host country to go after pirates.
Remember also: “No pain, no gain.” Life is NOT a risk-free adventure, but many internet geeks seem to think so.
End of communique.
With all due respect, I think you may be looking at this in a bit of an idealistic mindset. We aren’t talking about war crimes, or even imminent threats to national security, we are talking about a large number of small time criminals, and a small number of bigger organized crime “families” that are carrying out near victimless, economic crimes against US businesses / consumers. At the end of the day, the cost of even this huge Target hack / crime, is minimal for the US when you consider how credit fraud is written down, and who pays the bill. The total fraud will likely be realized by US consumers for only a few dollars in the way of higher fees and interest rates, spread out over months / years. When you consider the possible economic impacts against US businesses of “closing the electronic border” just to root out these guys, I think the financial impact would be FAR greater. Not to mention, I just dont believe you would see much of a return by closing the electronic border.
Since you are so keen on history, how has the economic blockade of Cuba over the years worked? Does Cuba even care there is a blockade in place? No, because other, less scrupulous countries will step in and be glad to sell to them.
In the case of Eastern European / Russian nations, you are talking about issues bigger than cybercrime. Our diplomatic relations are strained at best with these nations. Not only would cutting them off from “our” piece of the internet likely not be effective, but it likely would NOT compel them to hand these guys over. Rather it would further strain our relations with these nations, and could further complicate diplomatic relations when lives are on the line, such as when we need their support at the UN for action against nations where people are dying. (I’m no fan of the UN, but right now thats how the system works.)
I think you also have to consider that sanctions / blockades generally have little effect because they are rarely imposed against otherwise honest nations. These former Soviet nations dont think or work the way the US and other western nations do. They are riddled with corruption, from top to bottom. Crime is a way of life in many of these areas. There is little incentive for these nations to stop these activities, and even if technically you could close the electronic borders, they just wouldnt feel enough of an impact to start handing these guys over.
I dont disagree with your principle that there should be some sort of pressure by our leaders to stop harboring these guys, however I do disagree with a blockade being an effective tool, even if it was something that was technically realistic. You cant view these things in vacuum…..
CJD – you would most likely (and probably are) a good micro-manager. A man with big vision, not so much …
You will stew and brood all day, contemplating multiple options and what the “come-back” or ramifications are, and never commit to action … we call this “analysis paralysis” in the trade.
A man of action you are not; we need men the caliber of Steve Jobs who did not fret the small things, as I suspect you are prone to do … now, having said that, we also need detail-oriented ppl like yourself. But not as one setting policy or negotiating with foreign powers, however.
Having to face Putin you would probably melt and he would walk away with your gonads …
Does this make sense yet? No? Then it never will …
End of communique.
CJD, I have come to believe that _Jim is a “ringer” with an overly simplistic worldview and understanding of how “sanctions” actually affect people. I wish I had read his other reply and your reply to his reply/etc before I’d written my comment just before this one. You have demonstrated more of an understanding. I’d like to also mention that people seem to ignore that sanctions affect the “little guy” more than the big guy, and that in fact ostracising probably winds up as a large contributor to people finding terrorism “more acceptable”.
Nobody reacts well to ostracism. Countries with any self-respect certainly don’t appreciate being told or goaded into “what they should do”. I’d point at the whole South American plane being stopped because Snowden might be on board as a recent example of how bludgeoningly counterproductive “demands” can be.
We have maximally nested apparently.
You are a modern day Sherlock Holmes good sir. Great article.
Where is the actual proof that he was the one who hacked Target ?? So far his only crime was that he was selling them numbers in his shop .Possibly its a crime — Handling of stolen goods or something .
And here is some more good news for my fellow Americans Exclusive: Target hackers stole encrypted bank PINs – source
BOSTON/NEW YORK (Reuters) – The hackers who attacked Target Corp and compromised up to 40 million credit cards and debit cards also managed to steal encrypted personal identification numbers (PINs), according to a senior payments executive familiar with the situation.
http://www.reuters.com/article/2013/12/24/us-target-databreach-idUSBRE9BN0L220131224
Lets see if they can crack the encryption .And i have a funny filling that they can .
Reading comprehension not a strong suit of yours, is it? Krebs didn’t say anywhere in the article that this kid was responsible for hacking target. In fact, the story explicitly says he doesn’t know, but suspects that this guy probably knows who was responsible.
“I have no idea if Rescator/Helkern/Andrew was involved in hacking Target, but it’s a good bet that he at least knows who was.”
Great work Brian. I too find the username breadcrumb trail so useful when investigating. Keep up the good work and merry Christmas.
I say find them punks then off with their heads!
http://www.AnonIs.tk
Spamming that website again ?
fantastic reporting……i have a question that I don’t think I have seen answered.
If target knows 40 million cards (approx) were stolen, they know the numbers….why dont’ they just cancel all 40 million cards? i think i read somewhere here that it costs $3-4 per card to replace it. So target is out $150 million but done with the issue. Not sure why the don’t just do that…..anyone??
because it’s not up to Target to make that decision, for the most part. That decision falls to the banks that issued the cards. Sure, Target has its own cards, but the majority of cards affected are likely to be those issued by hundreds of banks across the country and around the world. Each of those banks needs to weigh the risks vs. costs.
I reported in a story on Friday about one bank in New England that said it would cost them $3-$5 per card to replace, but that it wasn’t such an easy decision this time of year because many people are doing last minute shopping and/or traveling, and mass canceling your customers’ cards in the middle of that can really piss people off right now.
Great work as always.
Now that the class action suits have begun against Target [http://money.cnn.com/2013/12/23/news/companies/target-credit-card-lawsuits/] there should be a pretty massive fire brewing under the collective asses of several international law enforcement agencies. I look forward to the impending string of arrests, should they take place.
I would also hope that this leads to some significant shifts in the security of card-based monetary systems.
SiL / IKS / concerned citizen
Amazing, if this doesn’t become a movie I’ll be amazed…..
Why not contact police to do a coordinated effort to accept the bribe paying for it with a bank account with $0 so the transaction will bounce but the money trail of the transaction can be traced to the culprit?
Awesome sleuthing!
Take the money and run .
Memo to Mr. Hodirevski:
Make that move to Helsinki soon. Don’t wait.
Can any Ukranian just up and move to Helsinki? I thought Finland was a hard country to get into.
The comment was an attempt at humor. Several cybercrooks from Russia and Ukraine have been caught in the US and Western Europe in contravention of all common sense. Heck, Brazil, Argentina, South Africa, or any place they can have fun comfortably without a law enforcement establishment that wants to arrest them would be better. Better yet for HIM to stay home. Hence my advice.
With open borders in the European Union, if he could reach one member state, he could probably make it to Finland. If anyone knows more, let us know please.
I am *finally* seeing discussion in our media about the chip-and-pin technology used in Europe, which would at least partially prevent these sorts of shenanigans.
Brian,
Thanks for continuing to alert us about the bad guys. Some of the information is too technical for me, so I’m glad there are folks like you who are ethical and take time to educate the rest of us.
Great article…as a person in the Cybersecurity field this is superb reporting
“Odessa. Now there’s a city for you. Everyone’s a crook. Little crooks take from who they can. Nobodies stealing from nobodies. Then the middle man. How many nobodies does it take to feed him? Seven? Ten? The middle man is always hungry, always worried. Because from the middle it’s easier to fall down than to climb up. But the big crooks- the machers in Odessa… the big crook does nothing. Drink coirvois. Eat roast chicken, fish soup. Stroll with some cute little tsatske along Deribasovskya street. Everybody tips their hat. The big crook in Odessa-he’s somebody. I wake up sometimes and I think I’m still there twelve years old, my whole life ahead of me. But then I realize I’m in America. That world is gone. And you have to make the best of it.”
“He would be nothing in Odessa.”
~Boardwalk Empire
Wow Manny, I’d love to read more. Have you ever thought about writing a memoir or novel about Odessa? Your comment would make a great opening paragraph.
It’s a reference to a TV show on HBO: http://boardwalkempire.wikia.com/wiki/Manny_Horvitz
I don’t have cable / NetFlix, but if you do, you can probably watch it…
Personally, if I could, I’d watch http://theamericans.wikia.com/wiki/The_Americans_Wiki
(I haven’t seen The Rockford Files in ages…)
Damn! You destroyed these guys..
Awesome reporting Brian! You may be the only person in the media out there doing any real investigative reporting these days. I love the story and how you connect all the dots. Great work!
One wonders why our law enforcement can’t put together these puzzle pieces and get rid of these vermin.
You pretty much laid the ground work for how to not get caught!! 1, never use pictures, 2 never use the same name on any social web sites, or list exactly where your from. It is a good report, but I seriously doubt tracking down the others is going to be possible. This Andrew seemed more interested in glory, then keeping a low profile. Sadly you could offer them money to give up sources, but they probably could make 10,000 in a few months.
All these guys will leave some breadcrumbs from different forums etc. See that this went back to 2008. At some point the rubber meets the road and there is real person that has a job, has a facebook account, pays rent, etc.. Hindsight is 20/20 and looking back it seems obvious but being able to predict forward into the future any one of those steps that Brian outlines may seem inconsequential.
It’s easy to say he should use a different identity each time he registers somewhere. But he’s trying to monetize the information he’s stolen. He needs people to send him money. They’re going to want someone to vouch for him. That’s why he had to introduce himself when he joined the forum and why he had to create connections to his previous activities.
What these guys don’t take into account is that they can be swept up into other people’s private feuds when those people express displeasure with each other by sending dumps of entire forums to Brian. That’s how he got Spamdot[dot]biz.
They also don’t take into account the possibility that law enforcement can assume the identity of a crook who is out of circulation, as was done with Master Splyntr on Dark Market.
Agreed.
Just wanted to point out that Master Splynter (“Pavel” aka Keith Mularsky) was created from thin air with the aid of places like ROKSO. A better example would have been SA Mike Adams taking over Celtic’s online identity and thoroughly infiltrating carder.su to sell fake ID (this was in the news a couple of months ago under the name “Operation Open Market”).
VERY impressive investigative reportage – I was blown away!
Are these dumping sites even legal? (don’t laugh I really don’t know). How does one find these type of sites to begin with?
Anyway, good job and well done! You now have a new subscriber.
Amazing work! Not surprised though, as your follower I wouldn’t expect any less.
Would love to hear how you find all those underground markets and darkweb sites. Ever thought of offering seminars in the field?
good job, Brian! A+++
who’s next?
Seriously, great article! I hope next will be a legendary Tymblep – owner of uniccshop[dot]ru, i’ll be expecting to see hs photos and personal information in this great blog!
Thank you Brian!
I am not who you hink I am.
Not Andrew -are you Roger, by any chance?
Yea Andrew, nice try. Lol
You don’t get to see many good piece of journalist investigation these days, nice work. As for those crooks, capture them and beat them with a bamboo stick.
Yes, absolutely Raman, top class article and as you said it is hard to find similar articles nowadays, mostly some fluff content with rehashed do’s and dont’s
Sad thing is Brian’s articles are the ONLY ones that aren’t filled with false assumptions by “experts” and most other stories are filled with scare tactics and do nothing to educate or help the average consumer. Brian has knocked it out of the park IMO.
Awesome Job Brian !! Incredible what you are able to do by mining open source and forums. Law Enforcement should take notice.
Send in the drones (personal delivery for Andrey/Andrew).