A large number of banks, credit unions and other financial institutions just pushed customers onto new e-banking platforms that asked them to reset their account passwords by entering a username plus some other static identifier — such as the first six digits of their Social Security number (SSN), or a mix of partial SSN, date of birth and surname. Here’s a closer look at what may be going on (spoiler: small, regional banks and credit unions have grown far too reliant on the whims of just a few major online banking platform providers).

You might think it odd that any self-respecting financial institution would seek to authenticate customers via static data like partial SSN for passwords, and you’d be completely justified for thinking that, too. Nobody has any business using these static identifiers for authentication because they are for sale on most Americans quite cheaply in the cybercrime underground. The Equifax breach might have “refreshed” some of those data stores for identity thieves, but most U.S. adults have had their static details (DOB/SSN/MMN, address, previous address, etc) on sale for years now.
On Feb. 16, KrebsOnSecurity reader Brent Hoeft shared a copy of an email he’d just received from his financial institution Associated Bank, which at $30+ billion in assets happens to be Wisconsin’s largest by asset size.
The notice advised:
“Please read and save this information (including the password below) to prepare for your online and mobile banking upgrade.
Our refreshed online and mobile banking experience is officially launching on Monday, February 26, 2018.
We’re excited to share it with you, and want you to be aware of some important details about the transition.
TEMPORARY PASSWORD
Use this temporary password the first time you sign in after the upgrade. Your temporary password is the first four letters of your last name plus the last four digits of your Social Security Number.
XXXX#### [redacted by me but included in the email]
Note: your password is all lowercase without spaces.
Once the upgrade is complete, you will need your temporary password to begin the re-enrollment process.
• Beginning Monday, February 26, you will need to sign in using your existing user ID and the temporary password included above in this email. Please note that you are only required to reenroll in online or mobile banking but can access both using the same user ID and password.
• Once you sign in, you will be prompted to create a new password and establish other security features. Your user ID will remain the same.”
Hoeft said Associated Bank seems to treat the customer username as a secret, something to be protected along with the password.
“I contacted Associated’s customer service via email and received a far less satisfying explanation that the user name is required for re-activation and, that since [the username] was not provided in the email, the process they are using is in fact secure,” Hoeft said.
After speaking with Hoeft, I tweeted about whether to name and shame the bank before it was too late, or perhaps to try and talk some sense into them privately. Most readers advised that calling attention to the problem before the transition could cause more harm than good, and that at least until after Feb. 26 contacting some of the banks privately was the best idea (which is what I did).
Associated Bank wouldn’t say who their new consumer online banking platform provider was, but they did say it was one of the big ones. I took that to mean either FIS, Fiserv or Jack Henry, which collectively control approximately 70 percent of the market for bank core processors (according to FedFIS.com, Fiserv is by far the largest).
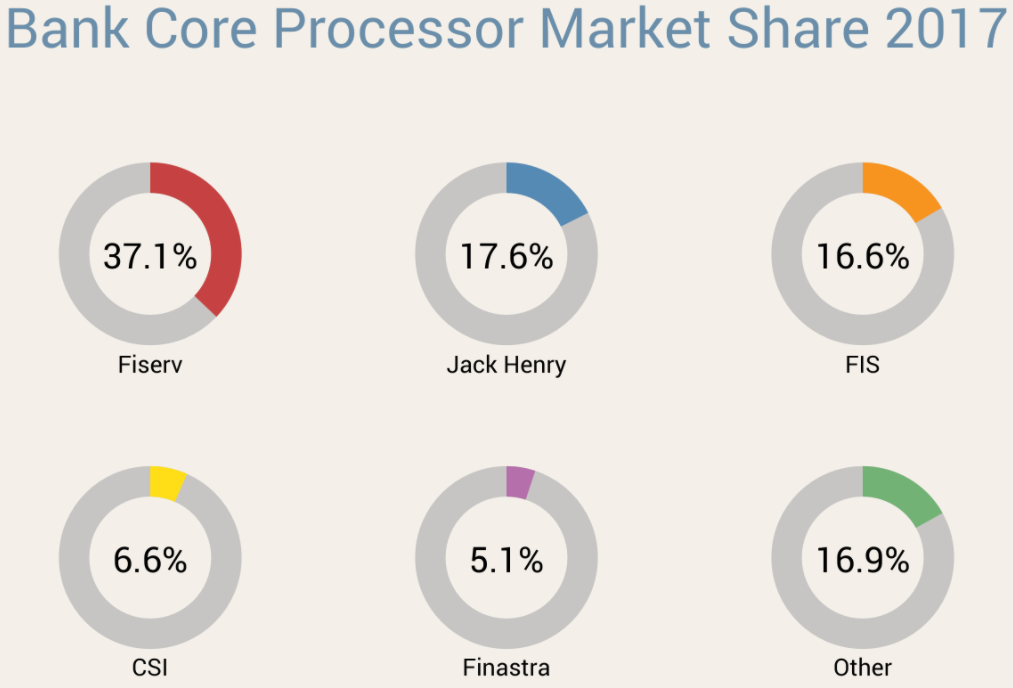
Image: Fedfis.com
The bank’s chief information security officer Joe Smits said Associated’s new consumer online banking platform provider required that new and existing customers log in with a username and a temporary password — which was described as choice among secondary, static data elements about customers — such as the first six digits of the customer’s SSN or date of birth.
Smits added that the bank originally started emailing customers the instructions for figuring out their temporary passwords, but then decided US mail would be a safer option and sent the rest out that way. He said only about 15 percent of Associated Bank customers (~50,000) received instructions about their temporary passwords through email.
I followed up with Hoeft to find out how his online banking upgrade went at Associated Bank. He told me that upon visiting the site, it asked for his username and the temporary password (the first four letters of his last name and the last four digits of his SSN).
“After entering that I was told to re-enter my temporary password and then create a new password,” Hoeft said. “I then was asked to select 5 security questions and provide answers. Next I was asked for a verification phone number. Upon entering that I received a text message with a 4 digit verification code. After entering the code it asked me to finish my profile information including name, email and daytime phone. After that it took me right into my online banking account.”
Hoeft said it seems like the “verification” step that was supposed to create an extra security check didn’t really add any security at all.
“If someone were able to get in with the temporary password, they would be able to create a new password, fill out all the security code information, and then provide their phone number to receive the verification code,” Hoeft said. “Armed with the verification code they then would be able to get right into my online banking account.”
OTHER BANKS
A simple search online revealed Associated Bank wasn’t alone: Multiple institutions were moving to a new online banking platform all on the same day: Feb. 26, 2018.
My Credit Union also moved to a new online banking service in February, posting a notice stating that all customers will need to log in with their current username and the last four of their SSN as a temporary password.
Customers Bank, a $10 billion bank with nearly two dozen branches between Boston and Philadelphia, also told customers that starting Feb. 26 they would need to use a temporary password — the last six digits of their Social Security number — to re-enroll in online banking. Here’s part of their advice, which was published in a PDF on the bank’s site:
• You may notice a new co-branded logo for Customers Bank and BankMobile (Division Customers Bank).
• Your existing user name for Online Banking will remain the same within the new system; however, it must be entered as all lowercase letters.
• The first time you log into the new Online Banking system, your temporary password is the last 6-digits of your social security number. Your temporary
password will expire on Friday, April 20, 2018. Please be sure to log in prior to that date.
• Online Banking includes multi-factor authentication which will need to be reestablished as part of the initial sign in to the system.
• Your username and password credentials for Online Banking will be the same for Mobile Banking. Note: Before accessing the new Mobile Banking services,
you must first login to our enhanced Online Banking system to change your password.
• You will also need to enroll your mobile device, either through Online Banking by visiting the Mobile Banking Center option, or directly on the device through the
app. Both options will require additional authentication.
Columbia Bank, which has 140 branches in Washington, Oregon and Idaho, also switched gears on Feb. 26, but used a more sensible approach: Sending customers a new user ID, organization ID and temporary password in two separate mailings.
ANALYSIS
My tweet about whether to name Associated Bank attracted the attention of at least two banking industry security regulators, each of whom spoke with KrebsOnSecurity on condition of not being identified by name or regulatory agency.
Both said their agencies would be using the above examples in briefings with member institutions as instructional on how not to do online banking securely. Both also said small to mid-sized banks are massively beholden to their platform providers, and many banks simply accept the defaults instead of pushing for stronger alternatives.
“I have a lot of communications directly with the chief information security officers, chief security officers, and chief information officers in many institutions,” one regulator said. “Many of them have massively dumbed down their password requirements. A lot of smaller institutions often don’t understand the risk involved in online banking, which is why they try to outsource the whole thing to someone else. But they can’t outsource accountability.”
One of the regulators I spoke with suggested that all of the banks they’d seen transitioning to a new online banking platform on Feb. 26 were customers of Fiserv — the nation’s largest online banking platform provider.
Fiserv did not respond to specific questions for this story, saying only in a written statement that: “Fiserv regularly partners with financial institutions to provide capabilities that help mitigate and manage risk, enhance the customer experience, and allow banks to remain competitive. A variety of methodologies are used by institutions to enroll and authenticate new users onto online banking platforms, and password authentication is one of multiple layers of security used to protect customers.”
Both banking industry regulators I spoke with said a basic problem is that many smaller institutions unfortunately still treat usernames as secret codes. I have railed against this practice for years, but far too many banks treat customer usernames as part of their security, even though most customers pick something very close to the first part of their email address (before the “@” sign). I’ve even skewered some of the airline industry giants for doing the same (United does this with its super-secret frequent flyer account number).
“I think this will be an opportunity for us to coach them on that,” one banking regulator said. “This process has to involve random password generation and that needs to be standard operating procedure. If you can shortcut security just by supplying static data like SSN, it’s all screwed. Some of these organizations have had such poor control structure for so long they don’t even understand how bad it is.”
The other regulator said another challenge is how long banks should wait before disabling accounts if consumers don’t log in to the new online banking system.
“What they’re going to do is set up all these users on this brand new system and give them default passwords,” the regulator said. “Some individuals will log into their bank account every day, others once a month and sometimes quite randomly. So, how are they going to control that window of opportunity? At some point, maybe after a couple of weeks, they need to just disable those other accounts and have people start from scratch.”
The first regulator said it appears many banks (and their platform providers) are singularly focused on making these transitions as seamless and painless as possible for the financial institution and its customers.
“I think they’re looking at making it easier for their customers and lessening the fallout as they get fewer angry and frustrated calls,” the regulator said. “That’s their incentive more than anything else.”
WHAT CAN YOU DO?
While it may appear that banks are more afraid of calls from their customers than of fallout from identity thieves and hackers, remember that you the consumer can shop with your wallet, and should move your funds to another bank if you’re unhappy with the security practices of your current institution.
Also, don’t re-use passwords. In fact, wherever possible don’t use passwords at all. Instead, choose passphrases over passwords (remember, length is key). Unfortunately, passphrases may not be possible because some banks have chosen to truncate passwords after a certain number of characters, and to disallow special symbols.
If you’re the kind of person who likes to use the same password across multiple sites, then a password manager is definitely for you. That’s because password managers pick strong, long and secure passwords for you and the only thing you have to remember is a single master password.
Please consider any two-step or two-factor authentication options your financial institution may offer, and be sure to take full advantage of that when it’s available. Also, ask your bank to require a unique verbal password before discussing any of your account details over the phone; this prevents someone from calling in to your bank and convincing a customer service rep that he’s you just because he can regurgitate your static personal details.
Finally, take steps to prevent your security from being backdoored by your mobile provider: Check out last week’s tips on blocking mobile number port-out scams, which thieves sometimes use in cashing out hacked bank accounts.




What banks allow 2FA that isn’t by SMS? I love using Google Authenticator, but unfortunately my bank doesn’t allow that as an option.
Bank of America. You can get a creditcard sized card that creates numbers. Doesn’t even need to be online.
The only bank that I know of in the US that uses Google authenticator (or its many equivalents) is Woodforest National Bank.
http://www.woodforest.com/Home/WFNB/New-Security-Features.aspx
There are several others that use RSA security key FOBs.
USAA lets you add a 2FA code through Symantec VIP access, which generates time based 2FA codes. You append the 6 digit code to the end of your password at login, as a opposed to a separate field after login.
There are third party projects out there to generate VIP access codes that generate a new QR code for you (for example, an open source python project), so you can store the 2A code in 1Password or Google Authenticator.
Wells Fargo has one.
https://www.wellsfargo.com/biz/online-banking/securid/
“Unfortunately, passphrases may not be possible because some banks have chosen to truncate passwords after a certain number of characters, and to disallow special symbols” – Nothing angers me like the maximum password length limit. I’ve stopped doing business with merchants that won’t allow my password to be over 20 characters. It is 2018, already. 12 character password limits are not acceptable!
My bank (PNC) is the same way, plus SMS based 2FA (which they just launched last year)
Since paswords are typically hashed or used as an input for some math algorith anything over 20 characters is useless anyway, as ths swill exceed that internal algorithm.
Also remember length is needed to defeat brute force craking. Anything above 16 is already huge OK for that.
Above that you need to worry about randomness and patterns to prevent more modern types of cracking. And then passphrases are often LESS secure than actual random passwords. Why? Because passphrases contain by definition patterns, else you wouldn’t be using them instead of a good 16 character true random number.
So forget phassphrases, but use a true random – hence computer generated, and hard to remember – password. Write it down on a paper in your wallet until it is memorized after a few uses.
If the software feeds a long string of text to a legitimate hash algotithm, then longer passwords DO improve randomness. There’s lots of redundancy even in “random” text strings. The hash algorithm retains that randomness unless the string is longer than the hash output. More likely, the software saves a weak hash of the password, or a less-secure truncated part of a strong hash.
Let me clarify that, because it could be read to imply that a hashing algorithm will ignore input after a certain length. It won’t; if you hash a doorstopper novel, then hash the exact same text changing the final period to a question mark, the two hashes will be utterly different (except that they are the same length, which they would be for any input).
So from a hashing perspective, there is no reason to limit password length. From a cracking-resistance perspective, longer is always better. Length limits are always abitrary. I won’t say they serve no purpose, but those purposes are always matters of practicality, not security.
For what it’s worth, TrueCrypt used to cluck its tongue at me if I used a password *shorter* than twenty characters. As far as I know there was no maximum.
16 at least – disturbing when first 1 (or 3) have to be numbers – they should all be 20+ and anything yo want to type
Your long password is just a speed bump. If someone wants your account, they’ll get it by password reset.
Resets are the weak link, not password length.
I don’t see the problem with treating usernames as secret codes. I’ve always treated it as a second password. My banking username is not even close to my email address or another guessable name. And it’s long too.
The problem is if the username is generated by the bank (because they just want “easy”) . The username should be checked for strength, like any password should be.
Speaking of bank passwords, I really hate that my bank (Chase) disallows the special character that I like to use in all of my passwords. The reason I was given for the special character ban was the difficulty in typing it on a cell phone. I happen to know how to type special characters on a cell phone, but because many customers don’t know how to type them the bank disallows a lot of special characters.
The password theme is the same as the article: security takes a back seat to reducing customer service calls.
I’ll add that the special character ban is due to Apple products. A lot of Apple product special charters require “press and hold” behavior, which banks do not want to support:
“Entering character accents on your iPad/iPhone using the on-screen keyboard is easy: just press and hold any key to select an accent”
iPhone special characters:
-Ensure that the Num Lock key has been pressed, to activate the numeric key section of the keyboard.
-Press the Alt key, and hold it down.
-While the Alt key is pressed, type the sequence of number (on the numeric keypad) of the Alt code from the Alt code table.
-Release the Alt key, and the character will appear.
To insert special characters and symbols on your iPhone or iPad:
-Tap the letter, number, or symbol that contains the alternative you want to access.
-Wait for the popup selector to appear.
-Slide up and onto the special character or symbol you want to insert.
-Let go.
I agree, apple makes using a keyboard a horrible experience. Make a mistake typing? oh you can’t move between characters anymore (they took away the keys), you have to backspace/delete and start all over. They won’t even make the old/standard keyboard an option, or allow it on their Isuckstore. Apple sucks.
Usernames are poor secret codes because they are widely re-used across sites, tend to be short, don’t typically have special characters and have been hacked and distributed online in numerous security breaches. It’s great that you treat yours as a second password, but most people don’t.
Why do we not hold the largest providers of banking and financial software accountable for forcing insecurity on their clients? It’s like trying to convince your grandmother that she needs to turn on security settings for her brand new, top of the line wifi router, but the company providing the router makes it nearly impossible to do so.
As a member of the banking and security community, the products provided by “the Big 4” are TERRIBLY insecure. They require their clients to use old, unsupported versions of IE as a front-end for their GUIs, years-old versions of Java (yeah), and prevent specific security patches from being installed across networks just for their antiquated systems to function properly.
How is that ok in 2018? Or ever, for that matter. These are some of the biggest companies in the world. Why do we continue to let them get away with forcing insecurity on the folks that protect our money?
Bank executives are too easily wooed by flashy UIs that “engage” the customer. But at the end of the day, all online banking platforms do essentially the same thing and customers really don’t care what their digital banking looks like. Security becomes an afterthought. Brian’s exactly right – digital banking has become more about convenience and preventing phone calls, than securing customer info.
Absolutely agreed on all counts. But the big question is this: if small banks are heavily regulated (they are) and asked to do things that the larger banks much do to be “secure,” how is it that the large companies that provide software and services to these banks are allowed to force insecurity on their customers? It’s a double-whammy for these smaller banks that have no leverage.
The large core banking providers should be held to a higher standard and expected to INCREASE security for the customers, not DECREASE security.
Also – there is strength in numbers. Smaller financial institutions ought to band together and demand change.
I can answer part of that: regulators put pressure on smaller institutions, but they expect the institutions to put pressure on the vendors in turn. The vendors are so big that the smaller institutions don’t have the leverage to push for these things. Meanwhile, the executives at larger institutions that do have leverage are pushing for flashy features and making it smooth for the consumer (as Derockcreed mentions).
A password and other “security” is just a speed bump to a thief looking for money.
If someone really wants your money, they’ll get it by password reset or by convincing a bank employee to provide it, or by breaching the bank itself.
No amount of regulation or penalties can prevent all risk to using a bank. It’s what you accept to be part of the banking system.
If you don’t like it, use only cash and precious metals stashed under your pillow.
For many smaller banks they have absolutely no leverage on the large providers. Take it or leave it. I seriously doubt that if Associated Bank had determined their security was lacking that their vendor would accommodate them. And at $30+ billion in assets they aren’t that small of a bank.
Absolutely agreed on all counts. But the big question is this: if small banks are heavily regulated (they are) and asked to do things that the larger banks much do to be “secure,” how is it that the large companies that provide software and services to these banks are allowed to force insecurity on their customers? It’s a double-whammy for these smaller banks that have no leverage.
The large core banking providers should be held to a higher standard and expected to INCREASE security for the customers, not DECREASE security.
Also – there is strength in numbers. Smaller financial institutions ought to band together and demand change.
If the verification phone number provided by the customer in the new enrollment process is validated against the phone number in the database, that would provide some additional protection.
I agree 100%, just banks being lazy.
Just a quick grammar item.
Nobody has any business using these static identifiers for authentication because they for sale on most Americans quite easily and cheaply in the cybercrime underground.
Should be???
Nobody has any business using these static identifiers for authentication because there for sale on most Americans quite easily and cheaply in the cybercrime underground.
Not quite…
Nobody has any business using these static identifiers for authentication because they are for sale on most Americans quite easily and cheaply in the cybercrime underground.
…or…
Nobody has any business using these static identifiers for authentication because they’re for sale on most Americans quite easily and cheaply in the cybercrime underground.
Frank–I may be MIA here, but did you mean to say “they’re” for sale….etc.??
Brian, is there a dropped word or dropped line in the text? “Nobody has any business using these static identifiers for authentication because they (sic) for sale on most Americans quite easily and cheaply in the cybercrime underground.
Yep, several people mentioned it. Thanks. Fixed.
It would seem easy enough for the bank to pass a verification phone number as part of the conversion instead of allowing the user (or criminal) to pick an entirely new phone number. Along those same lines, if the user had selected some secret questions on the previous website those could have been used to verify the new account. But in the end, why not go all the way and keep the previous password?
Because the bank DOES NOT KNOW the user’s old password. The bank only knows the user’s old password HASH, because that’t the ONLY thing they are storing in their DB. (At least that’s how it SHOULD work!)
And since the new hash algorithm is probably DIFFERENT than the old one, a new password (or re-inputting of the old password) will be required in any case so that a NEW HASH can be calculated and stored.
A difference in hashing algorithm isn’t a big issue. Most libraries used to write the backends of websites like these have the option of specifying the password hashing algorithm in the string used to store the hash. The more likely issue is a complete lack of desire to migrate more than the minimum data needed from the old app. I agree if you are talking about website preferences data but passwords go in the same necessary to migrate data category as the account records do.
Re: password length limitations: I cannot think of one valid technical reason to limit password or passphrase length, except one: they’re storing plaintext passwords somewhere. If they’re being hashed, then the result is always a known length on the backend, so there is zero reason to not allow me to use an entire paragraph if that suits me.
How about storage size and compute time trade-offs?
Your paragraph-long password has to be stored temporarily in browser memory and hashed using browser javascript.
Hash algorithm compute times also scale very non-linearly with password length, especially for the better-quality hashes.
Can you say SLOW? Would you (or anyone) be willing to wait several minutes every time you wanted to log in while the browser slogs through the hashing code?
You know that a desktop computer can hash a 32 character password in milliseconds right? Talking about how slow a long a password would be, in minutes, is absurd.
Could it be that the “top 4” here and Equifax are owned by the same holding company? Such a casual approach to security should be criminally liable.
I recently closed accounts at two very large US banks because I disagreed with their security and privacy practices. One failed to authenticate me, even when logging in from a different computer in a different country. Another failed to recognize my updated browser and prevented me from logging in from another country. It was also full of ads from “partner” companies. Both were full of third party trackers.
My current banks have zero or minimal trackers and do not share info with Google analytics or Facebook. They only advertise their own products (mortgages, savings, etc.) and have nice clean interfaces. One is a large national bank, but the others are small regional banks. They all offer 2FA via SMS, offer security alerts, and allow me to access my accounts anywhere, once authenticated.
In sum, I don’t think big banks are better or worse than small banks, but you need to evaluate each one on its own merits. If I had one of the banks mentioned in this article, I would have moved to another bank within a couple of months. However, it is not a good idea to close the account immediately, but instead wait a couple of months to properly migrate everything to your new bank.
I think it might be a good time to remind everyone that security questions make your account *less* secure. They open up extra backdoors to get into an account when the primary method has failed. The more ways into an account, the less secure it is.
@Alan
Even if you use nonsensical answers?
I agree,
What was your first car: Dog
Where did you grow up: Dog
and so on
No. Because then you’ve effectively just created 3 (or however many security questions your provider asks for) separate passwords. He’s just saying that if you use publically accessible info (What city do you live in?) then you’ve now created a pretty easy bypass into your account.
Santander UK heavily promote Trusteer Rapport (now IBM) on their internet home page. But this causes many users to be unable to close their PC due to a warning message in Chinese. The problem: https://answers.microsoft.com/en-us/insider/forum/insider_wintp-insider_perf/app-with-chinese-characters-preventing-my-computer/85528be7-80bf-4f83-93d3-2218be2bdcfe
The cause: https://www.urtech.ca/2016/01/solved-a-program-with-chinese-characters-app-is-preventing-you-from-signing-out/
Santander UK refuse to even look into this problem with an App that they are pushing hard.
Is there a way I can share this article with my CUs
Don;t forget about the non-core processing online banking providers. NCR’s Digital Insight is one of the biggest. They run the entire online banking application and simply have an authentication link back to the bank or credit union’s mainframe or core processing system. They probably have a few thousand smaller financial institutions as customers if not more.
Exactly, and a lot of times banks/CUs don’t use their core provider as their home banking provider. Do a little digging into these home banking providers for community banks and CUs and you’ll see that they all have this same kind of crazy policy for account migration. You can blame the banks and CUs for going along with it but it’s hard to fight when it has been a pretty much globally accepted solution by all HB providers. They’re not afraid of losing your business over it because you wont’ find a provider that does it a better way.
I just sent a link to your article to my local CU which just rolled out this same catastrophe of a website, using the same lastname/ssn6 temporary password mess. I hope they have a CIO/CISO/CTO to forward it to (as I requested they do), since there isn’t one listed on their website…
As an aside, USAA Federal Savings Bank uses the Symantec VIP Access app for two-factor. it’s not perfect, but it’s better than SMS.
I would suspect the previous commenters are correct about the phone number authenticating back to the core, and enrollment would fail if the numbers did not match.
Also, since NIST deprecated SMS 2FA, bank vendors are scrambling to fill the gap, since they were already down the path of SMS and away from challenge questions. You should see many issuing soft tokens through apps like RSA, Google, and others, in the near future.
As for the verbal passcode, a lot of banks and CUs will store those on their Core or CRM, outside of the online or mobile channel, so only their customer service people can access them. This low-tech option is widely available, you just know how to ask.
Length is not necessarily key, instead entropy is key.
I’m no expert but I think Steve Gibson has said length is more important.
If you do length correctly, you will have better entropy.
If you’re using passwords with a character set of 10 (only numbers), in order to achieve the same amount of entropy as a character set of 94 (all possible ASCII characters), you only have the double the password’s length. To say it another way, a password that is 16 characters long made up of only numbers provides the same level of difficultly-to-crack as an 8 character password made up of the possible 94 possible characters.
The most secure password policy would define a longer-length password.
I wish banks (and everywhere else) allowed you to use third party auth. Google, with 2FA, will do a far better job protecting your account than any bank can. Given that with control of a person’s email address, you can generally reset a user’s password, your email account is always the week point. Why have two chances to get hacked: bank credentials and google credentials instead of just one?
Most important part of this whole article:
“While it may appear that banks are more afraid of calls from their customers than of fallout from identity thieves and hackers, remember that you the consumer can shop with your wallet….”
Many organisations measure the losses from confused customers as higher than the losses of poor security practices, (fraud, customer churn etc.)
Yes, this is true. They measure the losses from confused customers as greater because the impact to the customer is more closely “Associated With” the bank. Where as losses from fraud may come weeks or months after the actual incident takes place. This is a clear case of an organization not really looking out for their customers.
You think their password policy is scary, you should read the fine print for sharing your user name and password to other 3rd party services like Mint or all the personal finance managers products for aggregating your accounts integrated with online banking. Once you provide your user name and password information you voliate your banking agreement and any fraud is now your responsibility.
This looks like the NCR banking app from digital insight. Bankers, and consumers, should be scared how your name and password are shared with miltiple 3rd party vendors that integrate with online banking apps.
My bank (a US subsidiary of a certain Ontario-based colonial-era institution) just switched online systems.
They did fine. They moved over my username and password. Hopefully they only had the hash and moved it, not the cleartext password.
They added 2FA, but unfortunately it uses the NIST-deprecated SMS method. Still better than nothing.
Now if they could only detect cloned debit cards being used almost simultaneously in multiple different cities, they would have saved a bundle of restitution money a few years ago when my card was skimmed at the Gulf fuel station near Fenway Park.
It seems to me whatever organisation has oversight on the banks is failing to enforce proper authentication methods. Banks won’t solve these issues unless their banking license is in jeopardy.
Almost every bank I know of in the Netherlands uses hardware tokens for digital transactions.
Sound to me a huge failure for the whole banking sector in the US.
There are 5 million people in Norway. There are over 325 million in the US. Ever accidentally leave one of those hardware tokens in your laundry?
Google authenticator or Duo or something along those lines is the answer.
Yubikeys! I’ve washed mine a number of times and it still works. Inexpensive too.
Given that there are probably a great deal of customers that still haven’t gone through the process to convert to their new home banking system, you have probably just helped set up a raid on this system.
You probably could’ve given them at least 30 days, as publicizing the name of this bank is also going to hurt the customers who had no say in this decision.
I have accounts in the US and Australia. One of my Australian banks (Westpac) issues separate RSA tokens to each user of a joint account. My US banks regard SMS 2FA as adequate. I wish they would support phone-based token generators like the Microsoft Authenticator, which I use for both corporate VPN access as well as AWS access.
if i am right, – usa and ca are the only countries where carders do transfers ,wires,dumps and etc-stuff.-?
as far i know uk is done long time ago.
so only usa left for carders to penerate?
All financial institutions need to add support for Yubikeys and U2F. It’s shameful that some banks are adding SMS/Text codes just now!
The service providers are regulated and the regulators have far more leverage to force them to offer secure products and practices than small to mid sized banks. Income from a $500 million bank is a rounding error for Fiserv and Jack Henry.
Changing service providers can easily cost more than 50% of a bank’s income for a year. It’s much cheaper to make a customer whole if there is a loss.
Not enough customers make their choices based on security practices for service providers and FIs to see changing as a rational decision.
My community bank, Flagship Bank, has a pretty good system set up to authenticate and work through Q2 Online Banking platform. Multiple authentication set ups.