Authorities in the U.S., U.K. and the Netherlands on Tuesday took down popular online attack-for-hire service WebStresser.org and arrested its alleged administrators. Investigators say that prior to the takedown, the service had more than 136,000 registered users and was responsible for launching somewhere between four and six million attacks over the past three years.
The action, dubbed “Operation Power Off,” targeted WebStresser.org (previously Webstresser.co), one of the most active services for launching point-and-click distributed denial-of-service (DDoS) attacks. WebStresser was one of many so-called “booter” or “stresser” services — virtual hired muscle that anyone can rent to knock nearly any website or Internet user offline.
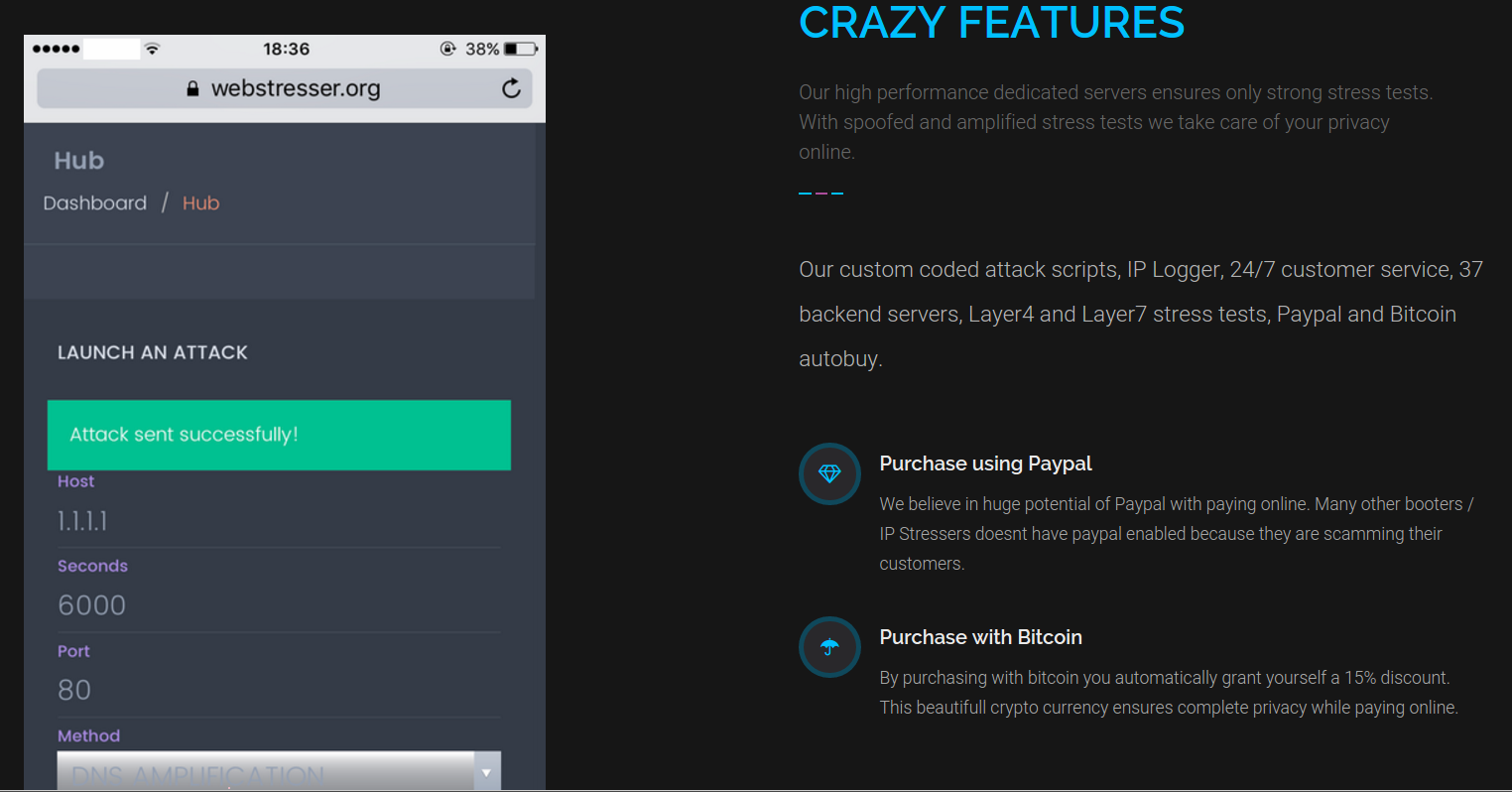
Webstresser.org (formerly Webstresser.co), as it appeared in 2017.
“The damage of these attacks is substantial,” reads a statement from the Dutch National Police in a Reddit thread about the takedown. “Victims are out of business for a period of time, and spend money on mitigation and on (other) security measures.”
In a separate statement released this morning, Europol — the law enforcement agency of the European Union — said “further measures were taken against the top users of this marketplace in the Netherlands, Italy, Spain, Croatia, the United Kingdom, Australia, Canada and Hong Kong.” The servers powering WebStresser were located in Germany, the Netherlands and the United States, according to Europol.
The U.K.’s National Crime Agency said WebStresser could be rented for as little as $14.99, and that the service allowed people with little or no technical knowledge to launch crippling DDoS attacks around the world.
Neither the Dutch nor U.K. authorities would say who was arrested in connection with this takedown. But according to information obtained by KrebsOnSecurity, the administrator of WebStresser allegedly was a 19-year-old from Prokuplje, Serbia named Jovan Mirkovic.
Mirkovic, who went by the hacker nickname “m1rk,” also used the alias “Mirkovik Babs” on Facebook where for years he openly discussed his role in programming and ultimately running WebStresser. The last post on Mirkovic’s Facebook page, dated April 3 (the day before the takedown), shows the young hacker sipping what appears to be liquor while bathing. Below that image are dozens of comments left in the past few hours, most of them simply, “RIP.”
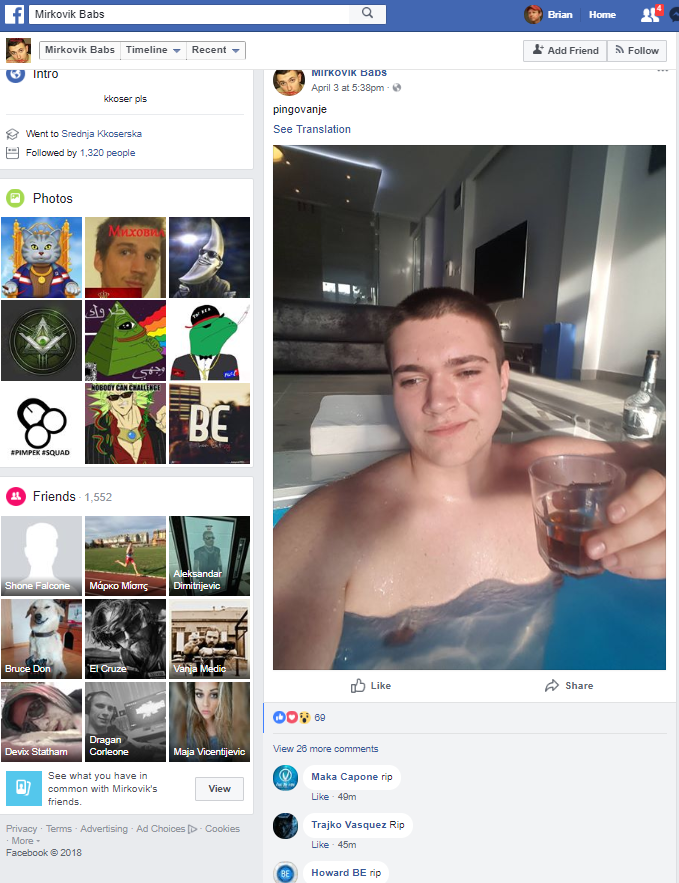
A story in the Serbia daily news site Blic.rs notes that two men from Serbia were arrested in conjunction with the WebStresser takedown; they are named only as “MJ” (Jovan Mirkovik) and D.V., aged 19 from Ruma.
Mirkovik’s fake Facebook page (Mirkovik Babs) includes countless mentions of another Webstresser administrator named “Kris” and includes a photograph of a tattoo that Kris got in 2015. That same tattoo is shown on the Facebook profile of a Kristian Razum from Zapresic, Croatia. According to the press releases published today, one of the administrators arrested was from Croatia.
Multiple sources are now pointing to other booter businesses that were reselling WebStresser’s service but which are no longer functional as a result of the takedown, including powerboot[dot]net, defcon[dot]pro, ampnode[dot]com, ripstresser[dot]com, fruitstresser[dot]com, topbooter[dot]com, freebooter[dot]co and rackstress[dot]pw.
Tuesday’s action against WebStresser is the latest such takedown to target both owners and customers of booter services. Many booter service operators apparently believe (or at least hide behind) a wordy “terms of service” agreement that all customers must acknowledge, under the assumption that somehow this absolves them of any sort of liability for how their customers use the service — regardless of how much hand-holding and technical support booter service administrators offer customers.
In October the FBI released an advisory warning that the use of booter services is punishable under the Computer Fraud and Abuse Act, and may result in arrest and criminal prosecution.
In 2016, authorities in Israel arrested two 18-year-old men accused of running vDOS, until then the most popular and powerful booter service on the market. Their arrests came within hours of a story at KrebsOnSecurity that named the men and detailed how their service had been hacked.
Many in the hacker community have criticized authorities for targeting booter service administrators and users and for not pursuing what they perceive as more serious cybercriminals, noting that the vast majority of both groups are young men under the age of 21. In its Reddit thread, the Dutch Police addressed this criticism head-on, saying Dutch authorities are working on a new legal intervention called “Hack_Right,” a diversion program intended for first-time cyber offenders.
“Prevention of re-offending by offering a combination of restorative justice, training, coaching and positive alternatives is the main aim of this project,” the Dutch Police wrote. “See page 24 of the 5th European Cyber Security Perspectives and stay tuned on our THTC twitter account #HackRight! AND we are working on a media campaign to prevent youngsters from starting to commit cyber crimes in the first place. Expect a launch soon.”
In the meantime, it’s likely we’ll sooner see the launch of yet more booter services. According to reviews and sales threads at stresserforums[dot]net — a marketplace for booter buyers and sellers — there are dozens of other booter services in operation, with new ones coming online almost every month.




“Many in the hacker community have criticized authorities for targeting booter service administrators and users and for not pursuing what they perceive as more serious cybercriminals…”
Because bricking Dyn was obviously the equivalent of saran wrap on your toilet seat.
Dyn’s DDoS wasn’t from a booter service. It was from a huge Mirai botnet of hacked routers.
If it’s got a NIC, it’s artillery for any fusillade you care to include it in.
But you are correct, yes.
Also, how many of the payments made to these services are on stolen card credentials acquired from more serious cybercriminals?
I sent “Mirkovik Babs” a friend request on Facebook. It may take him many years to reply LOL
European sentencing this guy will most likely get probation so I don’t understand your comment. This is not the US with crazy sentences
So, this was wrong 🙂
In American countrys they would make him work for FBI or CIA…
In poorly balcan countrys they would arrest, nice 🙂
This have nothing with hacking
No, in the US we put our criminals in prison. After they serve their sentence they may get hired, but they serve their sentence.
They are infamous for doing that in Russia though. Hell, they’ve even started doing it for criminals who harmed Russian citizens, which used to be the one line criminals couldn’t cross if they were going to get the white glove treatment.
They serve part of their sentence.
Frank Abignale Jr served less than 5 years before he started working as a consultant for the FBI
No…once charged the FBI is going to put you in prison. Typically for stupidly overblown charges that they can ignorantly brag about to the congressional budget critters.
The FBI instead recuits ‘pre-cons’. Meaning their favored enslavement tactic is to indefinitely hold charges over your head and make you work for a sliver over minimum COL (if that) until the statute of limitations runs out.
That said, I think most of them have a real intent to protect citizenry as opposed to the GRU.
He is free nice joke yeaaa so funny
Many in the hacker community seem to think DDoS is not a great crime. It’s no great crime if they only start a “little” fire. “We were just funning”
Never mind the huge resulting fire or the impact to the many fire fighting professionals.
Recently i have been watching stuff like this and i have been amazed. I got into sst a while ago and when i bought my first subscription to a stresser i was excited. I wondered how far i could push it and always “flexed” on it. Now i look back on myself and realise how childish i was. I dont see a point in it. Its just asking for trouble. Kids tryna be somebody through the internet not realising the day they are caught they are forgotten. My message to anyone tryna get into this stuff, dont its a waste of time and stresser owners are just tryna make a buck off you. No stresser will hit 50Gbps or over.
+ note, take out the ringleaders and all stressers go down 🙂
powerboot (dot) net
defcon (dot) pro
ampnode (dot) com
And you will see a huge decrease in the market 🙂
Ampnode is not a service that sells ddos services they resell servers from host sailor that allow people to send spoofed data
This is simply not true. I’ll grant that most of these booter service aren’t super hard-hitting. But some of them, including the aforementioned vDOS, were capable of launching DDoS attacks in excess of 100 Gbps.
They were capable of it sure, but did they ever give that bandwidth to paying customers or did they only reserve the full bandwidth capabilities for their own targets?
Rip Mirkovik 🙁 plaky
I just laugh how these modern cyber criminals don’t know how to keep a low profile.
Gary, there’s a reason for this. As Krebs’ article points out, the majority of hackers who are caught are under 21. These are people who haven’t fully matured and their decision making process is impaired. We know that the region of the brain dealing with decision making isn’t fully developed under 25. A lot of youngers get caught up in cybercrime because of a combination of impaired decision making (an eighteen year old literally does not have the capability of making as wise decisions as a 25 year old due to brain development) and possibly mental health issues. For example: many young offenders may literally believe that a terms of service ensures they aren’t liable for their actions, and they lack the capability of understanding the consequences of their actions. This is why Europe’s “Hack_Right” program could be so successful in teaching restorative justice and positive alternatives to young people who get caught up in this mess.
On the other hand, serious cybercriminals are older and do a much better job at keeping a low profile. These people rarely get caught.
It’s a mind over matter thing in all truth.
@Krebs great reporting as always
I disagree. I knew the difference between Right and Wrong when I was 18, and I also knew there would be consequences for doing wrong. The modern generation is being raised to not respect authority or expect punishment for their bad actions. They may not be as fully developed and make all of the best decisions, but that doesn’t mean they should be given a pass or a slap on the wrist if they are under 25. Criminal actions are criminal actions no matter your age. (Yes, I have 2 young kids and they are learning that bad decisions have bad consequences and already know the difference between right and wrong.)
Mitch,
I think that makingsense was just explaining why young criminals engage in “dumb” behavior like bragging about criminal activity. I didn’t interpret the comment as an argument for a “pass” or “slap on the wrist,” but instead as an argument for a more rehabilitation-focused approach, like using the Hack_Right program. As a young adult, I ask that you please don’t lump us all in together as a bunch of disrespectful, anti-authority children with no sense of consequences. I, like you and your children, know the difference between right and wrong.
Think it has more to do with personality. Someone boastful will likely do less to cover their tracks, while someone humble may not care about any sort of glory
Some do try to keep a low profile as they age and their crimes get more serious. The typical problem they face is that they don’t have the psychopathy to completely separate their criminal life from their social life.
This means they often have operational security flaws, like continuing to use their childhood nickname and email address or a website they had registered in a more innocent part of their lives. Krebs has covered this topic, as he follows “breadcrumbs” to uncover the identities of young “miscreants.”
Thanks god for those breadcrumbs. This how you may prevent more abuse : you arrest them (in case your LEA) or you scare them .
‘”Dude, i am not the police and i was easily able to find your real ID. Imagine if i were a cop. You should really stop your mess.”
who is the defense criminal investigative service? NCIS’ big brother?
6 million uses? I guess the obvious question is: What for?
Revenge, simple obnoxiousness, corporate/government espionage, misdirection (ie: to hide another attack/infiltration) obviously make up some large portion – but 6 million?
Do you have a sense what the aim is of the vast majority of these attacks?
Thanks.
Yes, if you look at the people running these DDoS-for-hire services and their customers, most of the time they are targeting online gamers of one sort or another. In some cases, they simply want to hit back in the real world at another gamer, targeting that person’s known IP address. In more extreme cases, they hit the entire server, knocking it offline, or they target Web sites they’re angry at.
In my story about vDOS, I noted that the administrator of that service commonly used his own very powerful DDoS service to target a gaming server that he and his gaming squad were playing on in a match against a rival team (sometimes these matches are also played for money). When it looked like they were about to lose a match, he would hit the server so hard it would fall over. The goal was to preserve the squad’s stellar win ratio, because he knew that an unfinished match would not count as a loss against the team’s record. This offers insight into the minds of the kids operating and using these services.
Funny How They Wont Come For Me After I Toke Usa.gov down If you want proof of the website down check my Instagram Story @Stupid.Haxor
And the whack-a-mole continues!! 🙁
As far as i see powerboot[dot]net and ampnode[dot]com
Are still up.
And more DDOS for hire webstressers.
I have alot of information about alot of Stresser owners.
Such as NullingOVH.
The owner of PowerBoot i have a real dox of him adress & name.
Yet he is still flexing.
Contact me for all the information would love to see him get arrested.
Although it certainly feels bad each time we read a press report that says that somebody or some company or institution has been DDoS’d to smithereens, and although it certainly feels good each time we read a press report like this one that tell us that one more of these scummy low-life little animals who didn’t get enough brest feeding as a child has been caught and spanked, all of this misses the point, I think.
The point, dear friends is that the fault lies not in this planet’s over-abundance of juvenile delinquents with keyboards, but rather it lies in a system, a society, and an Internet that allows the same said delusional children with keyboards to wreak havoc, at will, on arbitrary victims, planet-wide.
Who is really to blame then? If the fault is not in our stars, there where is it, exactly?
Anybody who knows the first thing about this problem knows the answer, and has known the answer for quite some time now. The answer is that each and every network that is connected to the Internet, and that fails to implement BCP 38 is responsible for this crap. Everyone knows this, and yet -none- of the (inaptly named) “backbones” or other peers ever disconnect and de-peer from any of the scummy anti-social networks that refuse to implment BCP 38. Why? Because the Internet is mostly about greed and nobody wants to leave any dollars on the table, e.g. by disconnecting from the few remaining low-life scumbag networks that still enable this kind of crap.
If a five year old manages to get a gun out of an unlocked case and then shoots his seven year old sister dead, who do we blame? The five year old or the parents who left the gun in an unlocked case? By the same logic it *must* be seen that the Powers That Be on the Internet are the ones actually to blame for all of this DDoS nonsense. Where are the grownups?
I’m as pleased as the next person, if not morseo, each time another one of these childish morons gets caught and put in the Graybar Hotel, but I think we need to stop celebrating just long enough to realize that none of these arrests actually do a damn thing to solve the underlying problem. As long as it is technically possible to perform DDoS attacks, they WILL keep on happening.
In a way, it is actually silly to even chase these infantile idiots down, because just like women, busses, and cosmological theories, there will be another one along in ten minutes. You can bet on it.
Sheesh! I do hope that this planet grows up someday. I’m not sure how much more of this insanity I can take, and I may find it necessary to go back home.
@Ron G
You’re are right stating that BCP 38 would be a major assisting technology to detract from DDOS attacks.
It won’t stop C&C PC’s that participate in DDOS attacks, if they are using their own IP address under control of botnet.
However, what I find puzzling is that one of the authors of BCP 38 works for Cisco, who have a major stake in backbone routing. How come they don’t implement it?
I disagree that this is a dollar driven argument. There is no law that states the ISP can’t charge for throwing away packets because they fail BCP38. Indeed, the ISP may determine that the packet still counts towards usage allowance but is not routed. So, in effect, the ISP is winning by not having to route the traffic onwards.
Blaming Cisco for an ISP not implementing BCP38 is about as stupid as blaming Ford for a driver running a red light. The fault lies with the ISP/Driver making the decision.
There have been many dicussions on line as to why BCP38 has not been widely implements, most due to the costs involved. The loss of revenue would be minor compared to the support costs incurred.
BCP38 defines ingress filtering. Routers could also do egress filtering. That would choke the DDoS and botnet C&C traffic by ensuring that the rogue packets never leave the local network.
+ note, take out the ringleaders and all stressers go down
serverstress (dot) net
And you will see a huge decrease in the market
I feel like you could have tried to find more info about him.
I’ve done a little bit research and can confirm that this is his HF account: https://hackforums.net/member.php?action=profile&uid=2940090
These emails are also linked to him:
mirkkovic@gmail.com
j.mirkovic4@gmail.com
Perhaps. But I think you’ll find that this story provides 20x more information than any other piece about the takedown published so far. And I only started working on this at 10 a.m. today.
Kristian Razum hf account its a bezbo 🙂 GLHF
You’re the best, Brian Krebs.
And the whack-a-mole continues!!
i wonder what payment methods the guy accepted?
i guess it was monero? wich is highly crypted crypto currency.
since bitcoin is might not so safe for crooks and criminals,however i think bitcoin just stay as central reserve currency.
other question is , how the law enforcement knew it was the right guy behind ? since internet is private and im sure guy did use vpn proxies shosx and all kind of securtiy but still they catched him?
how the law enforcement going to proof that it was the guy who done all? even crooks and hackers use crypto currencies but its still not enough for their privacy?
my opinion is this, the guy simply made some mistakes i think one of his e-mails or facebook acc was related with the job he did.
becouse its impossible to proof only if he only himself made mistakes.
as we know nobody dont sit behind the computer with their passport hands.
and even your location dont proof anything,to proof your criminal involvement law enforcement must proof now that hes realted with the money from criminal activity.
and thats most hardest part coz guy have good lawels and money to make moves.
it will be interesting case to watch on.
Mainly PayPal from what I can tell, but also Bitcoin
https://web.archive.org/web/20180118144032/https://webstresser.org/
Brian Krebs is an absolute God. He’s the man we need at Edison.
photos of his facebook profile can explain this guy mindset.
its some kind of revolutionary dude.
Brian, how about a screenshot instead of linking to Facebook.
Thank you
Ask, and you shall receive:
https://krebsonsecurity.com/wp-content/uploads/2018/04/razumtat.png
https://krebsonsecurity.com/wp-content/uploads/2018/04/mirkovik-tat.png
Looks like http://www.nationalcrimeagency.gov.uk is taking revenge DDoS now (ERR_CONNECTION_RESET),
https://twitter.com/EVE_status?lang=en taking collateral damage
Earlier today, I got this when trying to visit:
I made no changes to my browser settings (cookie-related or otherwise) over the past 24 hours, during which time the broken redirect first appeared, then vanished again.
Please explain the earlier incorrect behavior of this site.
This is an issue that pops up from time to time when there is a lot of traffic coming to the server. As you experienced, it usually resolves itself momentarily after it first manifests. I can assure you it’s not a security issue, it’s more like a load balancing issue.
It also happens when readers submit the same comment 4-5 times a minute, which you have done just now. Your comment was published, and I responded. Please stop.
It appears that Jovan Mirkovic has been released by the Serbian police, apparently there is a pic on his father’s fb account Milan. He won’t even end up in jail.
Brian Krebs needs to be selected for the Chairperson of the FCC.
The guy has clearly some political or spiritual view point.
All this symbols where this young guy got ideas or inspiration to do ecacly what he does ? !!
Who was his mentor ‘?
Would you be a guest author for us please? @ https://riskemy.com/
http://www.nationalcrimeagency.gov.uk/ down
Downed by the undoxable gods, netstress.org
harmless Mystic#3806 is my discord
The fact that you use disccord makes me think you’re one of those brainless instagram skids
Back in the 90s as kids we used to DOS people offline all the time. It wasn’t even criminalized, wasn’t even in ISP TOS. “Funning,” being the main point, trolling friends, or just trying to frustrate and knock offline people who were being trolls or split riding or mass de-opping in channel takeovers on IRC. Nobody really gave a second thought to it being illegal, and it certainly wasn’t prosecuted.
Sucks that kids have to go to jail for it, but it’s another level of stupid to be selling services with which people can attack commerce.
I’m a novice, and I’m trying to understand the distinction between stresser services and DDoS attacks executed by botnets. Do all stresser services simply utilize servers, or do some rely on botnets to execute DDoS attacks? Another thing: are amplification attacks unique to stresser services, or can botnets do those as well? Lastly, am I correct to assume that DDoS attacks via botnet are a greater threat than these stresser services? Thanks in advance.