Panerabread.com, the Web site for the American chain of bakery-cafe fast casual restaurants by the same name, leaked millions of customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card number — for at least eight months before it was yanked offline earlier today, KrebsOnSecurity has learned.
The data available in plain text from Panera’s site appeared to include records for any customer who has signed up for an account to order food online via panerabread.com. The St. Louis-based company, which has more than 2,100 retail locations in the United States and Canada, allows customers to order food online for pickup in stores or for delivery.
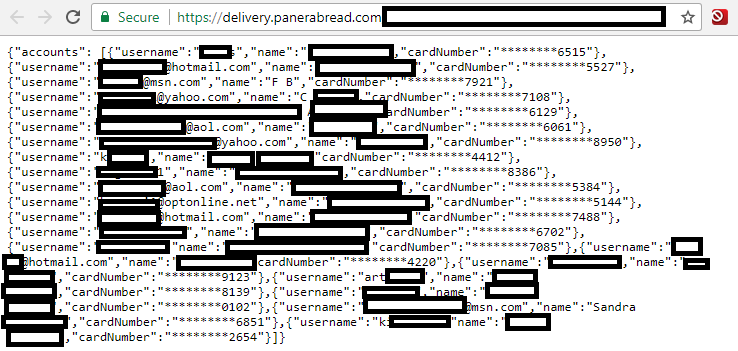
Redacted records from Panera’s site, which let anyone search by a variety of customer attributes, including phone number, email address, physical address or loyalty account number. In this example, the phone number was a main line at an office building where many different employees apparently registered to order food online.
KrebsOnSecurity learned about the breach earlier today after being contacted by security researcher Dylan Houlihan, who said he initially notified Panera about customer data leaking from its Web site back on August 2, 2017.
A long message thread that Houlihan shared between himself and Panera indicates that Mike Gustavison, Panera’s director of information security, initially dismissed Houlihan’s report as a likely scam. A week later, however, those messages suggest that the company had validated Houlihan’s findings and was working on a fix.
“Thank you for the information we are working on a resolution,” Gustavison wrote.
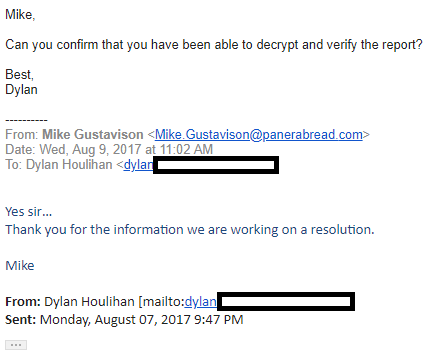
Panera was alerted about the data leakage in early August 2017, and said it was fixing the problem then.
Fast forward to early this afternoon — exactly eight months to the day after Houlihan first reported the problem — and data shared by Houlihan indicated the site was still leaking customer records in plain text. Worse still, the records could be indexed and crawled by automated tools with very little effort.
For example, some of the customer records include unique identifiers that increment by one for each new record, making it potentially simple for someone to scrape all available customer accounts. The format of the database also lets anyone search for customers via a variety of data points, including by phone number.
“Panera Bread uses sequential integers for account IDs, which means that if your goal is to gather as much information as you can instead about someone, you can simply increment through the accounts and collect as much as you’d like, up to and including the entire database,” Houlihan said.
Asked whether he saw any indication that Panera ever addressed the issue he reported in August 2017 until today, Houlihan said no.
“No, the flaw never disappeared,” he said. “I checked on it every month or so because I was pissed.”
Shortly after KrebsOnSecurity spoke briefly with Panera’s chief information officer John Meister by phone today, the company briefly took the Web site offline. As of this publication, the site is back online but the data referenced above no longer appears to be reachable.

Panera took its site down today after being notified by KrebsOnSecurity.
Another data point exposed in these records included the customer’s Panera loyalty card number, which could potentially be abused by scammers to spend prepaid accounts or to otherwise siphon value from Panera customer loyalty accounts.
It is not clear yet exactly how many Panera customer records may have been exposed by the company’s leaky Web site, but incremental customer numbers indexed by the site suggest that number may be higher than seven million. It’s also unclear whether any Panera customer account passwords may have been impacted.
In a written statement, Panera said it had fixed the problem within less than two hours of being notified by KrebsOnSecurity. But Panera did not explain why it appears to have taken the company eight months to fix the issue after initially acknowledging it privately with Houlihan.
“Panera takes data security very seriously and this issue is resolved,” the statement reads. “Following reports today of a potential problem on our website, we suspended the functionality to repair the issue. Our investigation is continuing, but there is no evidence of payment card information nor a large number of records being accessed or retrieved.”
Update, 8:40 p.m. ET: Almost minutes after this story was published, Panera gave a statement to Fox News downplaying the severity of this breach, stating that only 10,000 customer records were exposed. Almost in an instant, multiple sources — especially @holdsecurity — pointed out that Panera had basically “fixed” the problem by requiring people to log in to a valid user account at panerabread.com in order to view the exposed customer records (as opposed to letting just anyone with the right link access the records).
Subsequent links shared by Hold Security indicate that this data breach may be far larger than the 7 million customer records initially reported as exposed in this story. The vulnerabilities also appear to have extended to Panera’s commercial division which serves countless catering companies. At last count, the number of customer records exposed in this breach appears to exceed 37 million. Thank you to Panera for pointing out the shortcomings of our research. As of this update, the entire Web site panerabread.com is offline.
For anyone interested in my response to Panera’s apparent end-run around my reporting, see my tweets.




Great reporting, Brian. I don’t know if you’ve seen Mike Gustavison’s presentation about web security at Edge 2015, but in retrospect he doesn’t seem to have been following many of his recommendations:
https://www.youtube.com/watch?v=scdh2gx0XoQ
LinkedIn shows Mike Gustavison worked at Equifax right before Panera Bread. holy sh1t..hahaha
I know right … downplaying actual breach, etc … hmmmm … coincidence? Maybe … but if it smells like a fart … twice … it probably is 😛
This is OUT-RA-GEUOS.
What’s the problem with the Fox Business News article? It cited the Panera claim of thousands but also cited your response that it was millions.
Maybe when news organizations get conflicting claims, instead of publishing both of them, they should take the time to figure out which claim is true, and report what the truth is, and who was trying to mislead people.
it is fake news. if you read another sentence or two you see the statement parroted by the site was contradicted by the facts.
Disappointing reaction by a security practitioner….
It wasn’t just online ordering! Chase contacted me a few weeks ago and notified me that my Amazon Card had a debit pending for a Panera Bread Bakery in California. I live in Michigan and I never bought Panera online.
This is WAY bigger.
That’s just fraud spending that happens to be at Panera – it doesn’t mean anything, it’s just that whoever got your card details was hungry (and dumb – ordering food on stolen card details is a bush-league mistake that I’ve literally had fraudsters arrested over).
Like always data can be stolen without repercussions.
Don’t worry it’s secure.
Does this also affect the Panera app used for ordering?
I’m wondering this as well….
It affected mine. Someone falsely ordered $81 of items draining my gift cards in the app.
The breach was part of the Panera global API called “Foundation” as evidenced by the Pastebin info shown in article. ALL Panera digital apps share this common API, thus all digital apps were impacted.
I wonder if employee’s data was also exposed, because as a former employee, I know they did all their training, employee enrollment, scheduling and payroll online – how do I know this information (social security number, direct deposit info, etc. ) wasn’t exposed or compromised as well?
Most companies (of a certain size) do new hires, benefit enrollment and payroll online. We’re ALL at risk.
Ironically, Mike Gustavison, their IT “professional” originally worked at Equifax!
https://www.linkedin.com/in/mike-gustavison-b020426
Oh, come one. This is just bad confirmation bias at work.
If half of all companies get hacked each year, as is commonly reported, then practically every person who works in Security more than a couple years has worked somewhere that had a breach. That usually leads to valuable experience.
It’s like saying an individual firefighter must be bad because he worked at a fire station that had a building burn down on their watch. Well, not while he worked there, but a couple years later.
There is no defense for ignoring a glaring hole like this for 8 months after it’s been pointed out, so let’s stick to that topic.
I agree that personal attacks on people generally accomplish nothing. On the other hand, I think it’s fair to point out that he worked for Equifax in his previous job because Equifax’s actions prior to its breach exhibited a complete lack of regard for their duty to secure consumer data.
On top of it, their public response after the breach showed a contempt for the public, and a complete lack of accountability.
Seems to me both of these attitudes were on full display by the people running Panera, and Mr. Gustavison played key security roles in both companies. So in my view it’s completely fair to mention it.
Maybe MikeG is worthy of his own entry on the attrition org charlatans page?
I’m reading this report while physically sitting in a Panera Bread restaurant, having just used their app to order my food. It’s unfortunate it happened, but to go 8 months and not do anything is inexcusable. They lost a customer today.
Sooner or later something like this happens, this kind of problem has happened to me, and i just stopped using my credit card, i lost my faith in online shopping.
As of 5 Apr the Panera website still won’t let me change my old password. Just sits and spins…
PANERABLEED!!!
Good to see someone updated Wikipedia with the news Brian reported. JAB a private holding company acquired PNRA for $315 share, (expensive food just my opinion): “On April 2, 2018, the security website KrebsOnSecurity reported that the Panera Bread website had leaked between 7 million and 37 million customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card number — for at least eight months before the site was taken offline.[26][27]”
Companies need to take internet security and CyberSecurity seriously. Thus far, the only ones that I see really taking it seriously is government contractors and not all of them are doing the security properly. You will be at risk no matter where you operate if it is in the internet world. unless you use a VPN and that doesn’t even protect you from everything.
The world should take note of GDPR and have similar regulations. Imagine the fines Panera would have to pay if they had these rules in place? Everyone would have been notified within 72 hours – not 8 months later.
https://www.eugdpr.org/
https://en.wikipedia.org/wiki/General_Data_Protection_Regulation
As for Mike Gustavison – please change careers outside of security. First Equifax and now Panera Bread… what’s next?
Who can u trust anymore?
I don’t hold a CISSP or other ISC2 cert but if I did I would seriously consider reporting Mr Gustavison for a violation of the ISC2 code of ethics.
“Code of Ethics Canons:
Protect society, the common good, necessary public trust and confidence, and the infrastructure.
Act honorably, honestly, justly, responsibly, and legally.
Provide diligent and competent service to principles.
Advance and protect the profession.”
My panera gift card which was registered in my panera app was used to make an $81 purchase today in a different state.
I too stored my gift cards and when I go to log on they now have no record of my account!!! I filed a claim with customer relations and they too state that no account exists. I’m smelling a class action suit!
Doesn’t surprise me. I work for a webhosting company that caters to soccer moms and one of the things we teach them is about using tagged email addresses which was used in Panera’s case. We noticed late last year those tagged email addresses getting spam. We reported it to Panera Bread and they refused to even discuss the matter as they kept pointing at their privacy policy saying nothing.
I’m glad Panera says they take security seriously. Maybe next time when someone reports something, they’ll pay attention.
Sorry, no. They won’t. Not until, like the many before them, they are threatened with loss of revenue by people not buying from them (and the shareholders get pissed off), their business is threatened with regulation, or on the super duper rare chance that someone from the company actually serves jail time.
I tried logging into my account (of course like an idiot I stored gift cards on my account!) – they have NO RECORD of my account anymore! I gave them all my information and they claim that I’ve never had an account that they can find! I’m VERY upset and not sure what recourse I can take???
!due dilligence + !due care * prudent man = jail time, fines, and bare minimum CI(S)O is fired!
Hmm, so they don’t pay their own workers enough to afford eating there, nor do they pay for necessary IT/security. Where is their money/profits going?
I’ve tried to reset my password numerous times without success. Opened a case with Panera support, it took them two days to send me a bad URL that does not work. So you leak our data and then we can’t sign in to protect it? Then you take two days to respond??? This is ludicrous! For those that want to reset your password go here: https://delivery.panerabread.com/
No company has a clean security track record, solid systems with 100% patching rates, and 0% open vulnerabilities. Most companies get breached and can’t even figure out what happened. I’ve seen APT’s that existed for YEARS undetected.
Always funny to see the Angry Trolls come out and bad mouth people both collectively and individually after any security incident. I am not saying ignoring a problem like this for months is defensible, just commenting that hysteria and lack of perspective doesn’t help anything.
It isn’t the security grunts who set the budget, pay only lip-service to security, or steer corporate culture into short-sighted risk decisions… but the crowd has always been quick to blame the wrong people. Scapegoating is just human nature I guess.
Has anyone been able to pin down the start date of the breach?
The Internet of Things (IoT) and its various connections pose an enormous threat. An article earlier this week makes mention of hackers utilizing the thermometer of a fish tank to access a list of Las Vegas high rollers. Quite intriguing.
https://www.casino.org/news/hackers-stole-las-vegas-casino-high-roller-database-via-its-fish-tank