Identity theft protection firm LifeLock — a company that’s built a name for itself based on the promise of helping consumers protect their identities online — may have actually exposed customers to additional attacks from ID thieves and phishers. The company just fixed a vulnerability on its site that allowed anyone with a Web browser to index email addresses associated with millions of customer accounts, or to unsubscribe users from all communications from the company.
The upshot of this weakness is that cyber criminals could harvest the data and use it in targeted phishing campaigns that spoof LifeLock’s brand. Of course, phishers could spam the entire world looking for LifeLock customers without the aid of this flaw, but nevertheless the design of the company’s site suggests that whoever put it together lacked a basic understanding of Web site authentication and security.
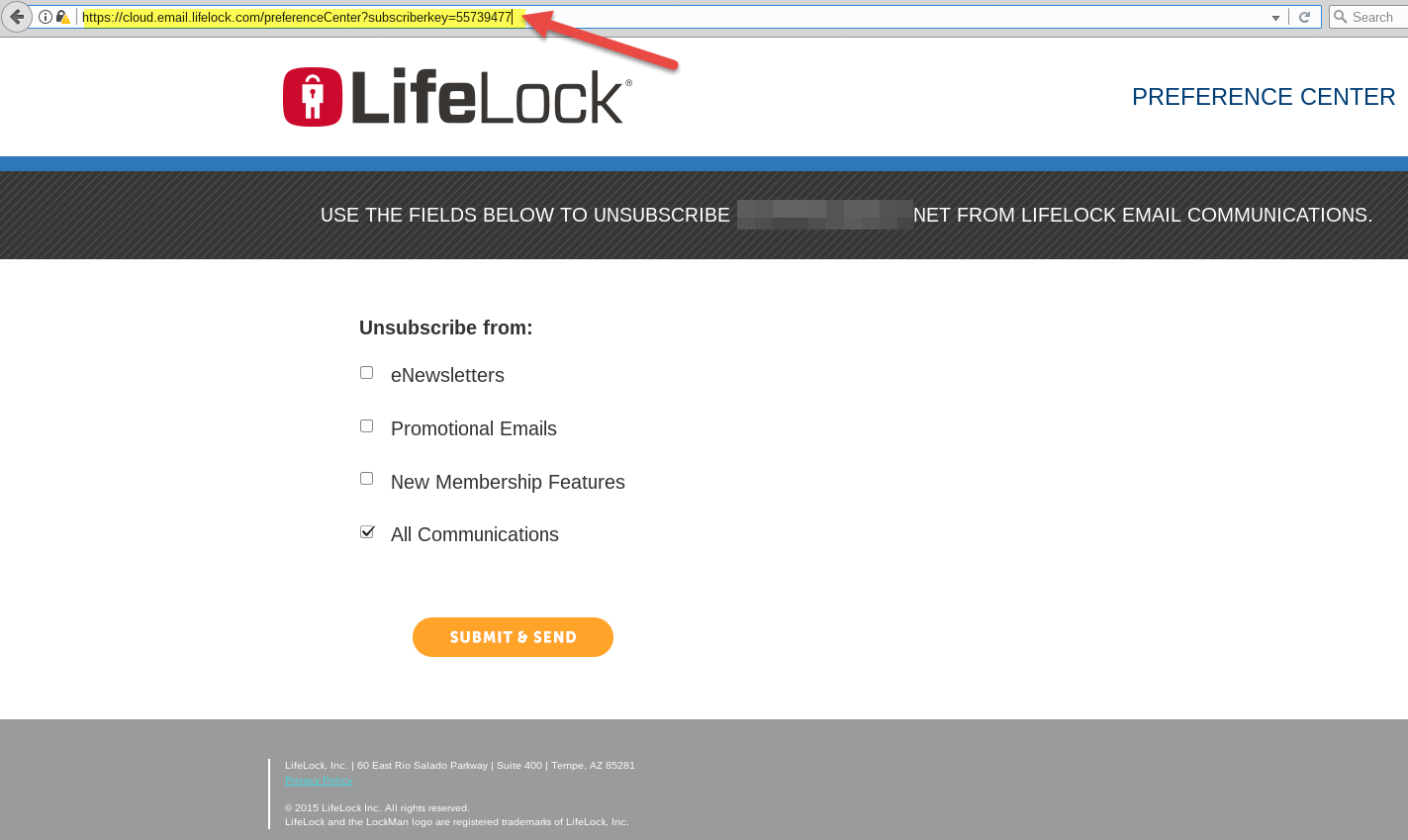
LifeLock’s Web site exposed customer email addresses by tying each customer account to a numeric “subscriberkey” that could be easily enumerated. Pictured above is customer number 55,739,477. Click to enlarge.
Pictured above is a redacted screen shot of one such record (click the image to enlarge). Notice how the format of the link in the browser address bar ends with the text “subscriberkey=” followed by a number. Each number corresponds to a customer record, and the records appear to be sequential. Translation: It would be trivial to write a simple script that pulls down the email address of every LifeLock subscriber.
Security firm Symantec, which acquired LifeLock in November 2016 for $2.3 billion, took LifeLock.com offline shortly after being contacted by KrebsOnSecurity. According to LifeLock’s marketing literature as of January 2017, the company has more than 4.5 million customer accounts.
KrebsOnSecurity was alerted to the glaring flaw by Nathan Reese, a 42-year-old freelance security researcher based in Atlanta who is also a former LifeLock subscriber. Reese said he discovered the data leak after receiving an email to the address he had previously used at LifeLock, and that the message offered him a discount for renewing his membership.
Clicking the “unsubscribe” link at the bottom of the email brought up a page showing his subscriber key. From there, Reese said, he wrote a proof-of-concept script that began sequencing numbers and pulling down email addresses. Reese said he stopped the script after it enumerated approximately 70 emails because he didn’t want to set off alarm bells at LifeLock.
“If I were a bad guy, I would definitely target your customers with a phishing attack because I know two things about them,” Reese said. “That they’re a LifeLock customer and that I have those customers’ email addresses. That’s a pretty sharp spear for my spear phishing right there. Plus, I definitely think the target market of LifeLock is someone who is easily spooked by the specter of cybercrime.”
LifeLock’s Web site is currently offline.
Misconfigurations like the one described above are some of the most common ways that companies leak customer data, but they’re also among the most preventable. Earlier this year, KrebsOnSecurity broke a story about a similar flaw at Panerabread.com, which exposed tens of millions of customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card.
Update, 7:40 p.m.: Corrected the number of LifeLock subscribers based on a 2017 estimate by Symantec.
Update, July 26, 7:32 a.m.: Symantec issued the following statement in response to this article:
This issue was not a vulnerability in the LifeLock member portal. The issue has been fixed and was limited to potential exposure of email addresses on a marketing page, managed by a third party, intended to allow recipients to unsubscribe from marketing emails. Based on our investigation, aside from the 70 email address accesses reported by the researcher, we have no indication at this time of any further suspicious activity on the marketing opt-out page.




Tried contacting Lifelock to delete or disable my account. I was told I purchased it through Norton and I had to call them as the Manage Account feature has been temporarily disabled. Hmmm… I called Norton and went through the 20 questions to verify my identity again and they said they could only stop the auto-renewal and I had to call Lifelock to totally deactivated/disable my account. I called Lifelock and they said I had to talk to their legal department and again place on hold only to be told….wait for it…..I had to call Norton. WTF??? I am furious. On top of it, 3 of the 4 reps I spoke to could not understand me and I know my English is very clear. The one guy I could not understand at all. Now holding for Lifelock to get a manager on the phone but already told me that person will tell me to call Norton. I asked they stay on the line WITH Norton to stop the back and forth but they said they could not do that. What a scam.
Just a heads up to people working with competing ID theft protection companies who have been spamming the comments here with ads for your services: I have been marking your comments as spam and will continue to do so. Please do not pollute the comments here with marketing for your products, thank you.
It was just a matter of time before they found a ‘chink’ in the armor at LifeLock. I’m surprised they haven’t been hacked yet. In todays world most website have either been hacked or alredy hacked and not detected YET.
Hi Brian,
The domain is for a preference centre where it looks like the email service provider is Salesforce.
I am weary of all these “protection” services. A few years ago I signed up for a competitor’s account (TrustedID) for a year, paid for another entity responsible for security breach.
After one year of using this service, I decided I would NOT renew with them, as I saw little benefit for the $120 annual fee, or whatever it was. Upon review of a later credit card statement, I discovered TrustedID had auto-renewed my account, using card numbers I had loaded in my account for them to monitor, and without permission! And not only that, they overbilled my account twice, compounding the problem.
I called to complain and cancel my account, and found the custom er support rep resistant to my request to cancel, forcing me to get louder and angrier. They did agree to cancel and refund, but only after verifying I had not logged on to use the account since the billing occurred.
These monitoring companies are not to be trusted in my opinion, any more than the bad guys attempting usurp your identity.
Dear Rickster, and ANYONE ELSE WHO WANTS TO BE A VICTIM, Identity Theft Protection isn’t a JOKE, many people are not interested and not protected are facing the wall of disgust because of a “Broken Legal System “ and are dancing to a different tune and aren’t silent about getting locked up for crimes against them that they “supposedly “ had done!!! Fact is, anyone can make unwarranted accusations and have you arrested for anything negative and you have to prove that you’re not guilty!! Thus having to pay for your legal fees…, and if you’re being extradited that’s a whole other issue, means that attorney you have may not be in jurisdiction! Well, I’m going to go out on the limb and even say that one could have to spend thousands to restore ones reputation legally if ever some evilness appears out of nowhere. I got the cure All, and We Are Legal<<<<<<<<<<<<<<<<<<<<<<<>>>>>>>>>>>>>>>>>>>>>>>>>>>>!!!
Get both IDENTITY theft protection and legal insurance to totally restore dignity to a great name like yours.
Congrats, Michael. You just earned your ID theft protection service an automatic /dev/null assignment in future comments! Keep spamming my comments. You won’t see them here.
Loved your comment to Rickster. Sadly, no “like” button? 😉
Oops. Not “rickster” … but, “Michael”
I would agree. Auto-pay in all forms is evil. 20 years ago, trying to cancel AOL resulted in going through dozens of screens only to finally be told to call a 1-800 number. After waiting on hold for another hour to actually process the cancellation, they *still* charged my card. Getting rid of them required canceling the card.
I signed up for tabnet for web hosting, and they tried to auto renew my service even though I never asked for it and had no intention of renewing the service. It didn’t go through because the card expired and they actually tried to send a bill collector after me to recover their failed auto renewal.
More recently, when I used a credit card to pay for a music lesson with mymusicstaff.com, they automatically set it to auto pay with no notification and no option to turn it off. Canceling it also required a new credit card.
These days, I give my credit card to *no one*. If you don’t accept paypal or amazon, forget it. You don’t need my money.
And trustedid charging a card you didn’t authorize? That is straight up credit card fraud and probably violates any number of computer fraud and/or privacy laws.
This is a joke. I expect more from you Krebs. This is about as serious as a marketing email with the email addresses CC’d instead of BCC’d. Finding 70 email addresses with no other customer data does not constitute a breach in any way shape or form.
Kyle, I never said it was a breach. Are you a Lifelock employee or reseller? If you can’t see how this is a major screw-up by a company that ought to know better, I don’t know what else to say. Other than the proof-of-concept cited in the article could have easily enumerated all of the email addresses of the company’s customers. And anyone else who found the same (but never reported it) could have done the same.
There are numerous testimonies about this particular hacker. He has peculiar expertise in hacking and miraculously fixing credit reports and clearing debts. At first I felt it was too good to be true and looked like a scam because they are everywhere. I thought really long and hard because at that moment I was in a really serious credit mess , I was late on payments and collections and I had serious repossession issues and I needed a bigger house for my family. Then a colleague at work suggested I tried which I did. I hoped that testimonies about him were as genuine as the sounded and hell yes it was! He not only cleared the collections and payment issues that I had, he raised my score which helped me secure a loan which I used to buy a house for my family.now I have a credit score of 870 with no more repossession issues. You should contact him because he is 100% on delivery.
You forgot to include an email address where poor suckers can reach you, dumbass.
FICO of 870? Are they now grading on the curve?
Maybe they should change their name to – Life-Leak.. 😉
Brian, why don’t the FTC come down on these folks instead of slapping them on the hand? I have seen several articles over the years(negative I might add)about these practices.
Hi
Hi, Sandy.
I’m curious to know whether or not Mr. Reese notified Lifelock about the vulnerability BEFORE disclosing it to Krebs on Security? While Lifelock don’t seem to have a ‘vulnerability bounty’ system like many other companies they do have a mechanism for individuals to report technical security issues such as vulnerabilities (lifelock.com/security) and an email to send it to at security@lifelock.com.
I am just suspect and wonder if they ignored his heads up about the issue when he notified them -OR- whether Mr. Reese bypassed notifying them altogether and thought it better for his freelance security researcher career to just go public with the vulnerability- in which case he really didn’t do anyone a favor but himself and his career. (Ostensibly advertising the vulnerability to everyone UNTIL it was fixed by Lifelock.)
I assume had he reported it to them and had they listened to him he would never have gotten the actual public credit for discovering a very common web vulnerability. NOT to take away from the vulnerability itself, BUT if they ignored him- that makes them more culpable then if they had even an easily avoidable ‘whoops’ moment.
I love how most businesses talk about be the most secure and most reliable business in their field. Yet when it comes time to admit that they made a mistake, they blame it on a third party.
The reality is, whether or not the company has third party managing a portion of their website and/or business function, that company is still responsible for ALL vulnerabilities associated with them.
Additionally, this is a vulnerability in the fact that email addresses are associated with lifelock. The hacking community could use this information to send phishing or spear phish emails to known customers. The hacking community is extremely intelligent and they could potentially start a social engineering campaign against these email addresses.
Thanks for sharing this information and keep on sharing content to keep us safe.
I received a call from lifelock.Somebody was using my credit to furniture under my name and I received again this month of August 2018 .when I call the lifelock they are asking my date of birth and ssn. I don’t know if I can trust this person .after giving them my ssn. and date of birth .they can’t still look up my accts.
I was unaware of this until it appeared on a class action website.