The FBI confirmed this week that a relatively new ransomware group known as DarkSide is responsible for an attack that caused Colonial Pipeline to shut down 5,550 miles of pipe, stranding countless barrels of gasoline, diesel and jet fuel on the Gulf Coast. Here’s a closer look at the DarkSide cybercrime gang, as seen through their negotiations with a recent U.S. victim that earns $15 billion in annual revenue.

Colonial Pipeline has shut down 5,500 miles of fuel pipe in response to a ransomware incident. Image: colpipe.com
New York City-based cyber intelligence firm Flashpoint said its analysts assess with a moderate-strong degree of confidence that the attack was not intended to damage national infrastructure and was simply associated with a target which had the finances to support a large payment.
“This would be consistent with DarkSide’s earlier activities, which included several ‘big game hunting’ attacks, whereby attackers target an organization that likely possesses the financial means to pay the ransom demanded by the attackers,” Flashpoint observed.
In response to public attention to the Colonial Pipeline attack, the DarkSide group sought to play down fears about widespread infrastructure attacks going forward.
“We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives [sic],” reads an update to the DarkSide Leaks blog. “Our goal is to make money, and not creating problems for society. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
First surfacing on Russian language hacking forums in August 2020, DarkSide is a ransomware-as-a-service platform that vetted cybercriminals can use to infect companies with ransomware and carry out negotiations and payments with victims. DarkSide says it targets only big companies, and forbids affiliates from dropping ransomware on organizations in several industries, including healthcare, funeral services, education, public sector and non-profits.
Like other ransomware platforms, DarkSide adheres to the current badguy best practice of double extortion, which involves demanding separate sums for both a digital key needed to unlock any files and servers, and a separate ransom in exchange for a promise to destroy any data stolen from the victim.
At its launch, DarkSide sought to woo affiliates from competing ransomware programs by advertising a victim data leak site that gets “stable visits and media coverage,” as well as the ability to publish victim data by stages. Under the “Why choose us?” heading of the ransomware program thread, the admin answers:
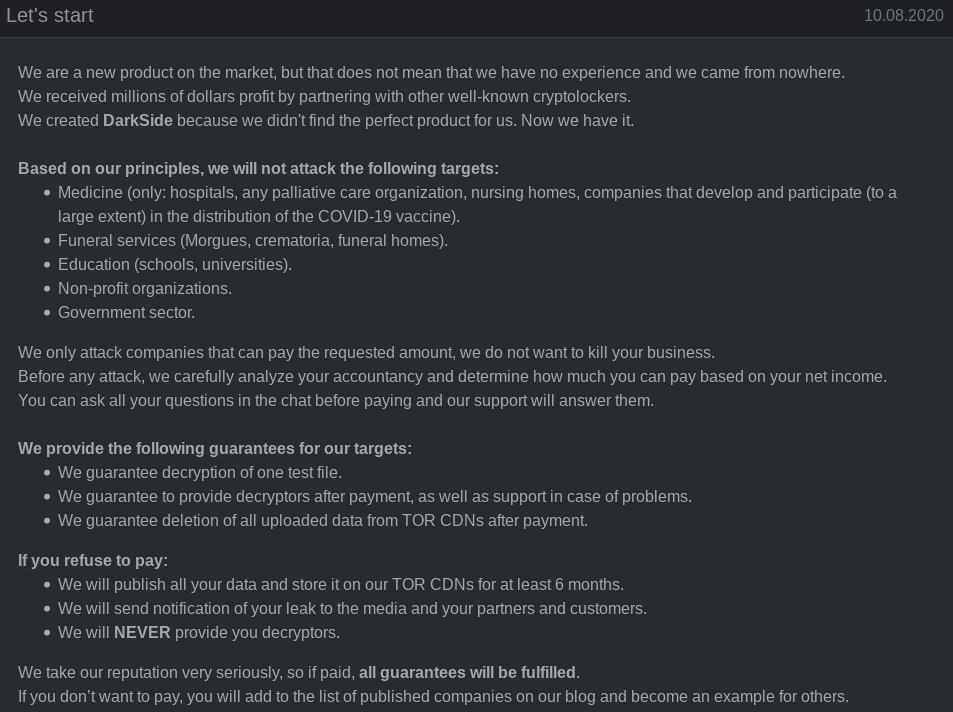
An advertisement for the DarkSide ransomware group.
“High trust level of our targets. They pay us and know that they’re going to receive decryption tools. They also know that we download data. A lot of data. That’s why the percent of our victims who pay the ransom is so high and it takes so little time to negotiate.”
In late March, DarkSide introduced a “call service” innovation that was integrated into the affiliate’s management panel, which enabled the affiliates to arrange calls pressuring victims into paying ransoms directly from the management panel.
In mid-April the ransomware program announced new capability for affiliates to launch distributed denial-of-service (DDoS) attacks against targets whenever added pressure is needed during ransom negotiations.
DarkSide also has advertised a willingness to sell information about upcoming victims before their stolen information is published on the DarkSide victim shaming blog, so that enterprising investment scammers can short the company’s stock in advance of the news.
“Now our team and partners encrypt many companies that are trading on NASDAQ and other stock exchanges,” DarkSide explains. “If the company refuses to pay, we are ready to provide information before the publication, so that it would be possible to earn in the reduction price of shares. Write to us in ‘Contact Us’ and we will provide you with detailed information.”
DarkSide also started recruiting new affiliates again last month — mainly seeking network penetration testers who can help turn a single compromised computer into a full-on data breach and ransomware incident.
“We have grown significantly in terms of the client base and in comparison to other projects (judging by the analysis of publicly available information), so we are ready to grow our team and a number of our affiliates in two fields,” DarkSide explained. The advertisement continued:
“Network penetration testing. We’re looking for one person or a team. We’ll adapt you to the work environment and provide work. High profit cuts, ability to target networks that you can’t handle on your own. New experience and stable income. When you use our product and the ransom is paid, we guarantee fair distribution of the funds. A panel for monitoring results for your target. We only accept networks where you intend to run our payload.”
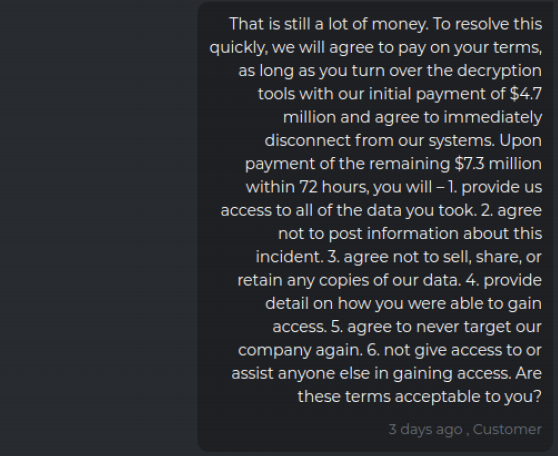
DarkSide has shown itself to be fairly ruthless with victim companies that have deep pockets, but they can be reasoned with. Cybersecurity intelligence firm Intel 471 observed a negotiation between the DarkSide crew and a $15 billion U.S. victim company that was hit with a $30 million ransom demand in January 2021, and in this incident the victim’s efforts at negotiating a lower payment ultimately reduce the ransom demand by almost two-thirds.
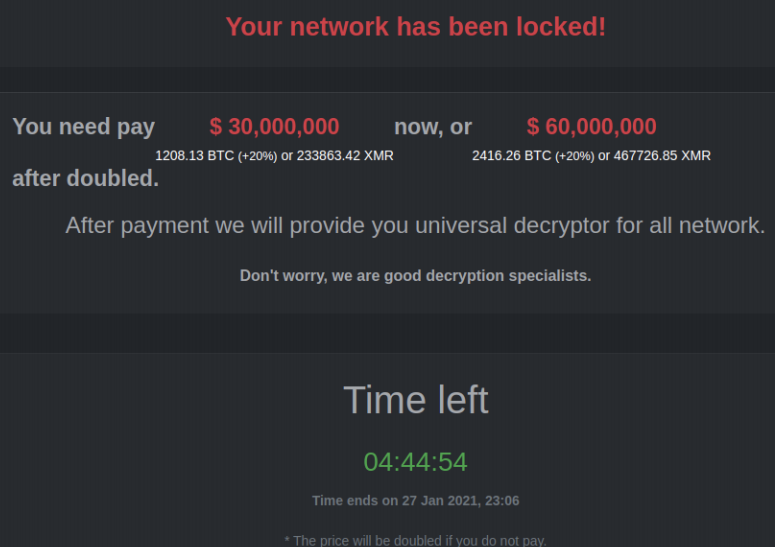
The DarkSide ransomware note.
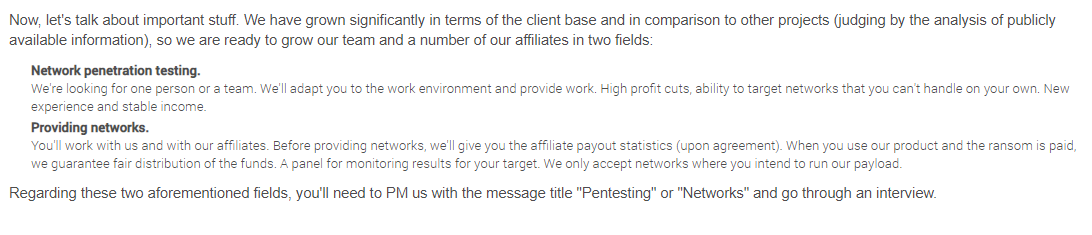
The first exchange between DarkSide and the victim involved the usual back-and-forth establishing of trust, wherein the victim asks for assurances that stolen data will be deleted after payment.
When the victim counter-offered to pay just $2.25 million, DarkSide responded with a lengthy, derisive reply, ultimately agreeing to lower the ransom demand to $28.7 million.
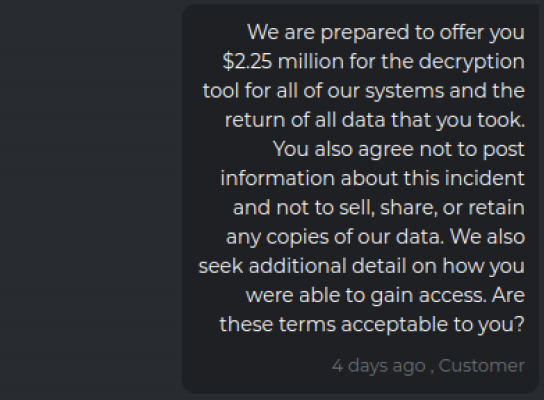
“The timer it [sic] ticking and in in next 8 hours your price tag will go up to $60 million,” the crooks replied. “So, you this are your options first take our generous offer and pay to us $28,750 million US or invest some monies in quantum computing to expedite a decryption process.”
Image: Intel 471.
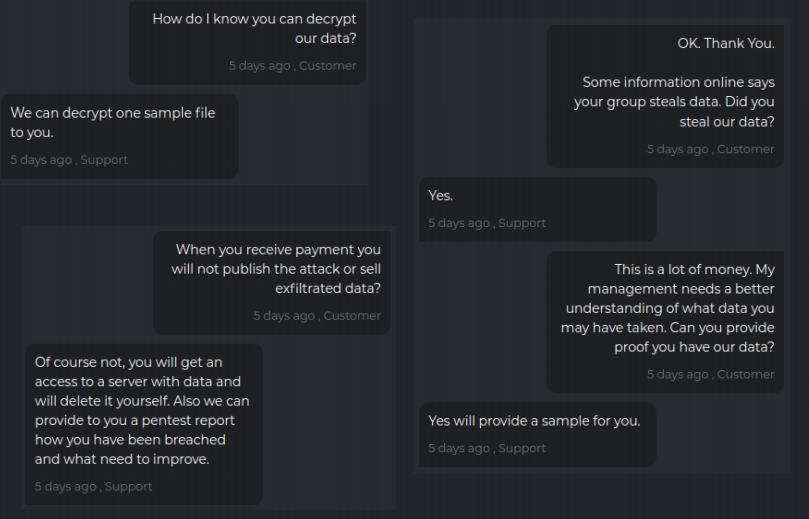
The victim complains that negotiations haven’t moved the price much, but DarkSide countered that the company can easily afford the payout. “I don’t think so,” they wrote. “You aren’t poor and aren’t children if you f*cked up you have to meet the consequences.”
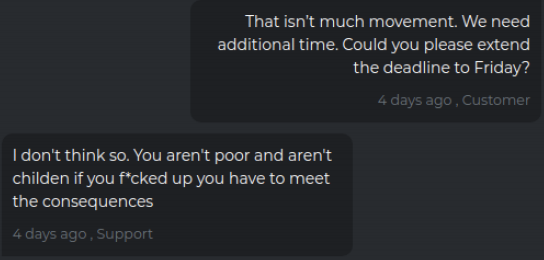
The victim firm replies a day later saying they’ve gotten authority to pay $4.75 million, and their tormentors agree to lower the demand significantly to $12 million.
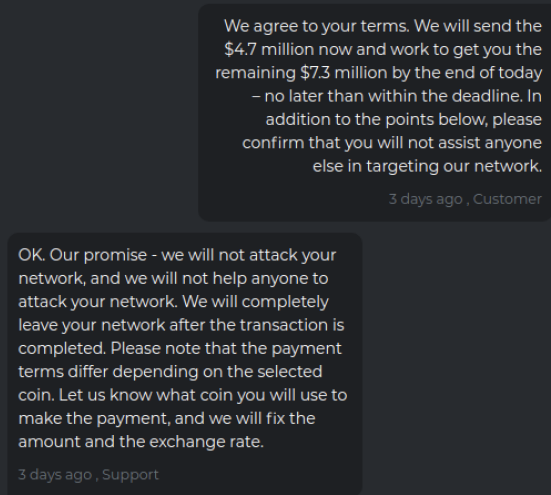
The victim replies that this is still a huge amount, and it tries to secure additional assurances from the ransomware group if it agrees to pay the $12 million, such as an agreement not to target the company ever again, or give anyone access to its stolen data. The victim also tried to get the attackers to hand over a decryption key before paying the full ransom demand.
The crime gang responded that its own rules prohibit it from giving away a decryption key before full payment is made, but they agree to the rest of the terms.
The victim firm agrees to pay an $11 million ransom, and their extortionists concur and promise not to attack or help anyone else attack the company’s network going forward.
Flashpoint assesses that at least some of the criminals behind DarkSide hail from another ransomware outfit called “REvil,” a.k.a. “Sodinokibi” (although Flashpoint rates this finding at only “moderate” confidence). REvil is widely considered to be the newer name for GandCrab, a ransomware-as-a-service offering that closed up shop in 2019 after bragging that it had extorted more than $2 billion.
Experts say ransomware attacks will continue to grow in sophistication, frequency and cost unless something is done to disrupt the ability of crooks to get paid for such crimes. According to a report late last year from Coveware, the average ransomware payment in the third quarter of 2020 was $233,817, up 31 percent from the second quarter of last year. Security firm Emsisoft found that almost 2,400 U.S.-based governments, healthcare facilities and schools were victims of ransomware in 2020.
Last month, a group of tech industry heavyweights lent their imprimatur to a task force that delivered an 81-page report to the Biden administration on ways to stymie the ransomware industry. Among many other recommendations, the report urged the White House to make finding, frustrating and apprehending ransomware crooks a priority within the U.S. intelligence community, and to designate the current scourge of digital extortion as a national security threat.
Further reading: Intel 471’s take on the Colonial Pipeline attack.





While thieves like this are always on the radar, I think when they go too far such as this one, they probably are in trouble down the road since quite a few people are now putting a bulls eye on them. You still have to be able to get them and often their location makes it tough (e.g., Russia).
And much of this is preventable but companies hire incompetent security folks or ignore their recommendations.
Even the US government often fails at basic security. During a job application they wanted my personal information emailed to them unsecurely. They wanted the old “print PDF, fill out info, scan it, and email it back to the person”. Argh.
we need to find the crime group and persecute the, including use of seal team
These guys made a big mistake when they attacked critical infrastructure, and they clearly know it. If they’re smart, and it sounds like they are, they’ll scatter and lay low for a good long time. If they succumb to greed they’re sunk.
This reminded me of Dixie Group, which was apparently a victim as well of this same group back in mid-April, if their Hall of Shame is to be believed.
Is there a way to see or know what IP addresses these guys used or are using?
Tracert
Not a good place to be in (negotiating with criminals like this). I wonder what this company was that was in this back and forth with them and it does sound like they paid the ransom.
Intel 471. Ironically, a cybersecurity company
Intel 471 doesn’t pay ransoms nor negotiate them on their an org’s behalf. They were able to obtain a copy of the chat log the bad guys had with the victim org (or the victim’s representative).
It’s good to see that these guys have a published code of ethics. Very reassuring.
Wow , this was a real good read for a Patch Tuesday !
It’s quite disturbing how they approach victims like its a ethical business their operating, especially with the ‘code’ of rules they provide in their about us section. Eventually they will get caught if they continue with the greed and arrogance.
It’s critically important that they act professionally. If anyone pays and *doesn’t* get their data back, they would scream bloody murder and nobody would pay their ransom ever again. They took great pains building that professional reputation so these $billion+ companies have some confidence that if they pay the criminals won’t just screw them over anyway for the luls.
Similar deal with the “ethics”. Not to imply they don’t have any moral code at all, but hey, they’re criminals. Not attacking hospitals during a global pandemic is just good business– if they cost lives, that would wake a sleeping giant. Which is exactly what they did with this oil pipeline attack, no doubt to their great chagrin.
Sure they had to build up their reputation today but who’s to say that they don’t hold back copies of all the data for later use? Say after the rest of the scam team retires, or in the unlikely case that it becomes difficult to exploit new ransomware targets.
You’re not wrong– that is definitely a concern. But I expect these large companies are _primarily_ concerned with getting their data back so they can continue doing business.
Yeah I’m thinking they didn’t meant to “wake a sleeping giant” this early, but they did. Mess around with the oil industry in the U.S. and you’ll need to tread carefully. Probably why they are trying to downplay the implications.
Its quite comical how they approach victims like its a ethical business their operating, especially with the ‘code’ of rules they provide in their about us section. Eventually they will get caught if they continue with the greed and arrogance.
A few people endangering the lives of millions of people, the punishment should fit the crime.
When you have an IT infrastructure ripped for picking, due to software full of holes and limited budget for security personnel and solutions, someone will take advantage of the weaknesses. Targeting large entities with deep pockets has been a great business and the chances are, that it’ll continue.It’s an ex[pensive lesson and hopefully, entities will listen to Darkside for correcting their IT infrastructure, that should’ve been done on the first place.
Maybe the entities should force software companies to eliminate their buggy, questionable quality software and make them financially liable for the end result.
I am for a cruise missile attack on them, and I do not care in which country they may be located.
Trump would do it.
Biden* will likely offer pallets of cash.
Was their a cruise missile attack after SOLARWINDS i missed and that was directly at USG?
It could be argued that no response then led to this attack. BTW Brian these aren’t miscreants any more , they are terrorists and need to be dealt with as such. Ransoming hospital systems during COVID ,shutting down critical infrastructure endangers lives . Time to attack regardless of borders.
Trump would do Nothing against Russian criminals.
Trump is likely jealous and trying to figure out how he can get in on the ransomware action.
Oh god this is good!!!
Eddy boy …You are so juvenile…grow up.
Nah- I am not at all for Trump (ugh!) but I’ll sure launch 2 million cruise missles up their asses and in whatever country they may be from! See? We can ALL get along
They should of had their team train on OffSec courses, this is all preventable with the right training
I dont know Why the company is going With paying the hackers allllll of that money
Paying the ransom is vastly cheaper than the alternative. The loss of data alone could end a company.
Prevention is cheaper still. Far too many organizations are dicing with disaster.
Why are they making that chose to pay them alll of that money i dont get it at all
These are people who are obviously well beyond the reach of extradition clauses.
The question is if the top 10 of these criminals suddenly died every year, would it curb the problem?
Would anyone miss them?
“You can ask all your questions and our support will answer them”
Who are you? Where do you live? What time is convenient for the cops to pay a friendly visit?
Seriously, I hope the back and forth was a delaying tactic to run traceroute on steroids and triangulate all the destinations for the negotiation and the source of the responses.
“Te greatest trick the devil ever pulled was to convince the world he didn’t exist.” — The Usual Suspects (movie)
I don’t go for their ‘ethical’ criminals story.
Fascinating read behind the scenes. Thank you for posting. More information needs to be posted so the scope is better understood.
Time to protect companies’ attack surfaces!!
Exploiting RDPs became way too easy. Legacy vulnerability scanners are actually putting companies at risk by being ineffective
Part of the guarantee is to let the victim know how the malware got in, plus tips for improving security. Hopefully Krebs can update its report here.
The Death Penalty for Ransomware??? Just thinking!
Yeah, but why stop there.
The only way to improve society as a whole is weed the filth out of the gene pool.
They have capitalist ethics .. do nothing that will negatively affect their profits. If they attack the wrong entities, the reaction could be strong. Governments and white hackers alike would attack. If they stick to the “big bad companies”, who don’t even admit they have been attacked, they win.
They don’t win in the end. They can never speak of what they have done or somebody listening will tell authorities and their financial wellbeing will come to an abrupt and very painful end.
And even if they practice absolute 100% secure operational security, time is not on their side. Countries’ espionage agencies are starting to wise up to just how big the threat cybercrime is becoming. Good spycraft can and will infiltrate just about anything anywhere. Even stuff that is believed to be beyond reach and super secure. It takes time to build up espionage capability, but it will get there in the end.
These guys are a clear existential threat to civilisation. A decent plan, well executed is needed to snuff all of them out as much as possible, then keep on snuffing out the weeds that regrow. The target organisations also need to be fixed. (Management that has a clue, meaningful penalties for those who mess up…)
Rules of sovereignty don’t apply to those who ignore such rules and the states, etc. that protect, harbour and / or nurture them.
The munitions, special forces, doctrines etc. exist. Time to use them.
My take on this:
There is no clean backup. Hack was done long ago to make sure the company cycled through backups. No fix.
The CIA is negotiating with Darkside to pay the ransom and telling Colonial you’re going to pay it and thank us for getting your a** out of a sling.
Again no news like this but just an educated guess.
Darkside have experience with enterprise backup software. They know how to delete them and they start the deletion process before they encrypt.
Having come from a hospital environment where many systems that interface to instruments are still on Windows XP and generally unpatched by the vendor (they say their FDA approval won’t let them patch. FDA says bull.) Our only option was to isolate or air-gap them.
I’m willing to bet Colonial had ancient control systems probably XP and unpatched as it would mean taking the pipeline down and mgmt wouldn’t like that.
There is nothing wrong with the right copy of Windows XP
I go online with Windows XP-SP2 all the time
The real problem is that there are so few “Real” security experts out there
“THEY” cannot use Windows XP online
I have been malware free and have NEVER had a ransomware problem while doing online “MALWARE RESEARCH” for the past 7 years
My copy of XP has ZERO Microsoft security updates and runs in a Full Admin Account “ONLINE”
It has not had a single BSOD in more than 12 years
How, you might ask?
Easy……
I am a REAL Windows Security Expert
and you are not!
Virtual…
No, Not Virtual
Native Boot to XP!
Are you using genuine XP, or bootleg XP? I quit using it years ago. It is inferior. 10 Pro, tightened, standard user acct, Mozilla (tightened/tweaked) is waaaaayy better than any possible XP setup. I used to like my XP, but realized it was time to move on. I have never looked back. BTW, I am aware that you can run XP on an admin acct, and get away with it, cause the crooks don’t look at XP anymore. Are you not looking over your shoulder, wondering if your good fortune will run out? I am not a Windows security expert, but I WAS a guest caller to a local radio talk show over a decade ago, offering advice on security issues. As you might imagine, with XP, in those days, the main topic was viruses. A lot has changed since then. Good luck, friend, hope it flies straight and true for you.
You will not stop malware with a “Genuine” copy of Windows XP
and…
You will not stop malware with a “Genuine” copy of Windows 10
The Genuine Advantage (or Genuine Monopoly Advantage) that Microsoft added to Windows XP “after” XP was already in distribution channels prevented you from stopping Microsoft running amok in your system
Likewise, Spyware Platform 10 prevents you from closing the backdoors or stopping Microsoft from entering your system and making unwanted changes
If you cannot stop Microsoft from hosing your system, then you cannot ever stop malware from hosing your system
I do not need to look over my shoulder and wonder if malware will someday wreck my XP box either
It is a Read Only Setup and I can simply reboot to a clean system after playing with malware all day
I enjoy the fact that I can choose to allow my web browser access to the Internet while denying everything else by default (including Microsoft components)
All main avenues of malware attack are denied by default
When I play with malware, it is because “I” chose to allow it, not Microsoft!
“YOU” do not have that choice because you have delegated your security to an Untrustworthy Corporation bent on Monopoly Control by Blackmail and Extortionary / one sided licensing “agreements”
Do you “REALLY” agree to those terms, or would you simply like to use your computer today?
You are deluding yourselves and you are not in control of “your” computers
Microsoft will not ever fix this mess and the majority of users will never have the knowledge needed to prevent them from click click clicking their way into a ransomware nightmare even on the most secure and updated system that Microsoft ever provides them
The OS cannot stop the malware problems alone
The user “CANNOT” be fixed!
and….
The Operating System Monopoly “WILL NOT” be fixed (willingly)
Touche! I agree with every point you have made! You seem to have a firm grasp on things. I am and have been aware of most of them. I guess, in the long run, that some of us are more comfortable trading away computer “liberty” for promised improvements. I am guilty of that. Hey, what about early versions of Windows 7? It was popular, but have been made aware that updates made it untrustworthy. I worked for a big corporation that still had 7 on it’s system, a few years ago. AND, I just happen to have a pristine 7 laptop on the shelf. Have not used it for couple 2 or 3 years.Any thoughts are welcome. In closing, it has been fun talking, I think that both of us have a lot in common. Thanks, and good wishes.
No, I don’t like Windows 7 either
You cannot block Microsoft’s access to your system if you wish to remain online
The real problems started with Genuine Monopoly Advantage “after” XP-SP1 was already released (without it)
Aftermarket firewalls also allowed you to block ALL Microsoft components from Internet access while you remained online with an aftermarket browser in XP
You cannot do that with Windows 7 / 8.1 or 10
If you block all Microsoft component Internet access in Windows 7 / 8.1 or 10, then you no longer have Internet access
You may (or may not) be able to stop unwanted Microsoft updates, but they still have access to your computer and all of your data
Heyyyy – just like my Novell server. Just can beat old tech.
“My copy of XP has ZERO Microsoft security updates”
Unless you wrote your own browser that is 100% secure and your own graphics subsystem to display images you are a sitting duck. Most likely relying on the fact that no one targets XP any these days.
Like I said
I am a REAL Windows Security Expert
and you are not!
Over 7 years studying malware online with Windows XP without a single problem is a far greater accomplishment than you will ever achieve with a fully updated copy of Spyware Platform 10
Try again!
The airline industry also relies on old OS “technology.” Scary.
It should be a felony with severe penalties and jail time to pay a ransom. If there are no payments, the ransomware will diminish. I also like cruise missiles. 🙂
Large outfits, with deep pockets (and BTW some considered too big to fail) put a few millions away in a bank account and are treating breaches as just traffic stops, or accidents. Lose tens of millions, or even hundreds of millions, of customers’ data, get a light slap on the hand, pay the fine, offer the victims ‘credit monitoring’, and go raise the product/service price towards making a new bank deposit for the next ‘accident’.
Nothing will change until the bar stays as low as it is for negligence and nonchalance in protecting data.
Will this bar get any higher in my life time? Not a chance!
These deep pockets not only have the ability to pay the hackers, and the ‘regulators’ but also have the ability to keep our Congress in their pockets.
So, I’m pessimistic about the future. In ways, both of our branches of Govt are themselves benefiting from this scrooge of ransomware. The deep pockets are putting money into their pockets, to do nothing and to keep the bar low!
DarkSide are a gang of modern-day pirates. The way society has traditionally dealt with piracy on the high seas for the last three centuries has been capital punishment. That could be an appropriate way to deal with cyber-extortionists today.
OOOOHHH, I’ll keelhaul ya, rabbit!…(Yosemite Sam)