In a Twitter discussion last week on ransomware attacks, KrebsOnSecurity noted that virtually all ransomware strains have a built-in failsafe designed to cover the backsides of the malware purveyors: They simply will not install on a Microsoft Windows computer that already has one of many types of virtual keyboards installed — such as Russian or Ukrainian. So many readers had questions in response to the tweet that I thought it was worth a blog post exploring this one weird cyber defense trick.
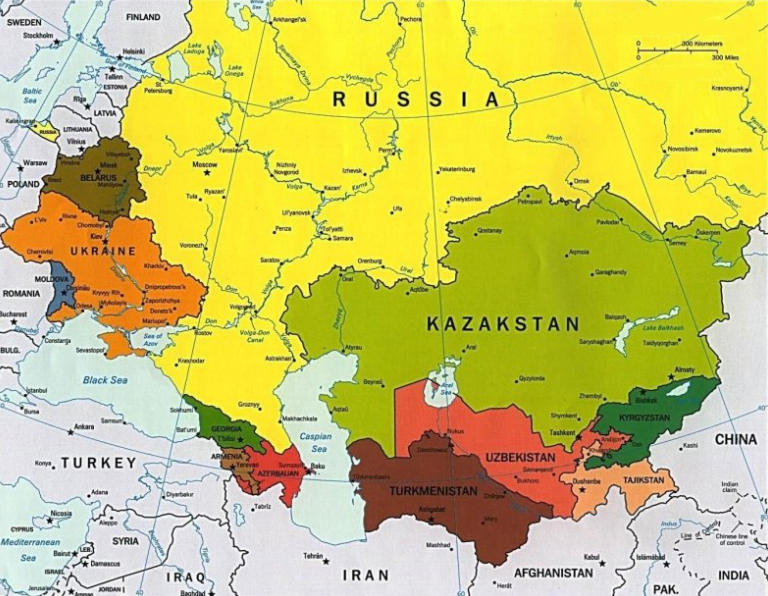
The Commonwealth of Independent States (CIS) more or less matches the exclusion list on an awful lot of malware coming out of Eastern Europe.
The Twitter thread came up in a discussion on the ransomware attack against Colonial Pipeline, which earlier this month shut down 5,500 miles of fuel pipe for nearly a week, causing fuel station supply shortages throughout the country and driving up prices. The FBI said the attack was the work of DarkSide, a new-ish ransomware-as-a-service offering that says it targets only large corporations.
DarkSide and other Russian-language affiliate moneymaking programs have long barred their criminal associates from installing malicious software on computers in a host of Eastern European countries, including Ukraine and Russia. This prohibition dates back to the earliest days of organized cybercrime, and it is intended to minimize scrutiny and interference from local authorities.
In Russia, for example, authorities there generally will not initiate a cybercrime investigation against one of their own unless a company or individual within the country’s borders files an official complaint as a victim. Ensuring that no affiliates can produce victims in their own countries is the easiest way for these criminals to stay off the radar of domestic law enforcement agencies.
Possibly feeling the heat from being referenced in President Biden’s Executive Order on cybersecurity this past week, the DarkSide group sought to distance itself from their attack against Colonial Pipeline. In a message posted to its victim shaming blog, DarkSide tried to say it was “apolitical” and that it didn’t wish to participate in geopolitics.
“Our goal is to make money, and not creating problems for society,” the DarkSide criminals wrote last week. “From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
But here’s the thing: Digital extortion gangs like DarkSide take great care to make their entire platforms geopolitical, because their malware is engineered to work only in certain parts of the world.
DarkSide, like a great many other malware strains, has a hard-coded do-not-install list of countries which are the principal members of the Commonwealth of Independent States (CIS) — former Soviet satellites that mostly have favorable relations with the Kremlin. The full exclusion list in DarkSide (published by Cybereason) is below:
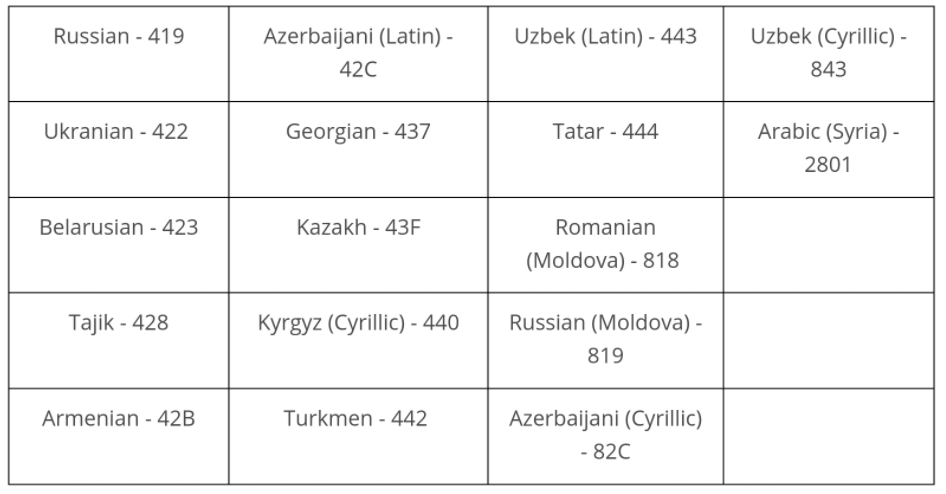
Image: Cybereason.
Simply put, countless malware strains will check for the presence of one of these languages on the system, and if they’re detected the malware will exit and fail to install.
[Side note. Many security experts have pointed to connections between the DarkSide and REvil (a.k.a. “Sodinokibi”) ransomware groups. REvil was previously known as GandCrab, and one of the many things GandCrab had in common with REvil was that both programs barred affiliates from infecting victims in Syria. As we can see from the chart above, Syria is also exempted from infections by DarkSide ransomware. And DarkSide itself proved their connection to REvil this past week when it announced it was closing up shop after its servers and bitcoin funds were seized.]
CAVEAT EMPTOR
Will installing one of these languages keep your Windows computer safe from all malware? Absolutely not. There is plenty of malware that doesn’t care where in the world you are. And there is no substitute for adopting a defense-in-depth posture, and avoiding risky behaviors online.
But is there really a downside to taking this simple, free, prophylactic approach? None that I can see, other than perhaps a sinking feeling of capitulation. The worst that could happen is that you accidentally toggle the language settings and all your menu options are in Russian.
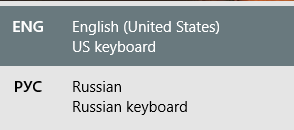
If this happens (and the first time it does the experience may be a bit jarring) hit the Windows key and the space bar at the same time; if you have more than one language installed you will see the ability to quickly toggle from one to the other. The little box that pops up when one hits that keyboard combo looks like this:
Cybercriminals are notoriously responsive to defenses which cut into their profitability, so why wouldn’t the bad guys just change things up and start ignoring the language check? Well, they certainly can and maybe even will do that (a recent version of DarkSide analyzed by Mandiant did not perform the system language check).
But doing so increases the risk to their personal safety and fortunes by some non-trivial amount, said Allison Nixon, chief research officer at New York City-based cyber investigations firm Unit221B.
Nixon said because of Russia’s unique legal culture, criminal hackers in that country employ these checks to ensure they are only attacking victims outside of the country.
“This is for their legal protection,” Nixon said. “Installing a Cyrillic keyboard, or changing a specific registry entry to say ‘RU’, and so forth, might be enough to convince malware that you are Russian and off limits. This can technically be used as a ‘vaccine’ against Russian malware.”
Nixon said if enough people do this in large numbers, it may in the short term protect some people, but more importantly in the long term it forces Russian hackers to make a choice: Risk losing legal protections, or risk losing income.
“Essentially, Russian hackers will end up facing the same difficulty that defenders in the West must face — the fact that it is very difficult to tell the difference between a domestic machine and a foreign machine masquerading as a domestic one,” she said.
KrebsOnSecurity asked Nixon’s colleague at Unit221B — founder Lance James — what he thought about the efficacy of another anti-malware approach suggested by Twitter followers who chimed in on last week’s discussion: Adding entries to the Windows registry that specify the system is running as a virtual machine (VM). In a bid to stymie analysis by antivirus and security firms, some malware authors have traditionally configured their malware to quit installing if it detects it is running in a virtual environment.
But James said this prohibition is no longer quite so common, particularly since so many organizations have transitioned to virtual environments for everyday use.
“Being a virtual machine doesn’t stop malware like it used to,” James said. “In fact, a lot of the ransomware we’re seeing now is running on VMs.”
But James says he loves the idea of everyone adding a language from the CIS country list so much he’s produced his own clickable two-line Windows batch script that adds a Russian language reference in the specific Windows registry keys that are checked by malware. The script effectively allows one’s Windows PC to look like it has a Russian keyboard installed without actually downloading the added script libraries from Microsoft.
To install a different keyboard language on a Windows 10 computer the old fashioned way, hit the Windows key and X at the same time, then select Settings, and then select “Time and Language.” Select Language, and then scroll down and you should see an option to install another character set. Pick one, and the language should be installed the next time you reboot. Again, if for some reason you need to toggle between languages, Windows+Spacebar is your friend.




How about this trick – don’t run your business on Windows software.
Cute… but currently not a practical solution.
Care to elaborate?
Because maybe and only maybe, there exists an awful lot of business software which is windows only?
This old chestnut. I defy anyone to name me some recognizable software that will only run on Windows these days. The only exception to this might be CAD/FEA software, but even AutoCAD has a Mac version these days. If it’s something business-specific, developed in-house, then it’s likely to be web-based, command-line, or Java, which can be compiled for different platforms. No, Windows continues to exist in big companies because their IT departments can do stupid things like prevent changing the desktop background and the screen lock timeout in the name of “security.”
If it’s recognizable software, it’s, by definition, probably big enough to be ported to most major platforms. It’s the unrecognizable software that makes this a big challenge. Most businesses have a lot of custom software, including legacy stuff. As more and more moves to the cloud, this may change, but most businesses still don’t find the expense of converting everything to cross plat to be feasible in a cost-effective way, at least short term.
It’s not like linux is un hackable. Lot’s of ransomware comes from successful fishing attempts. Windows is the popular target because it dominates the market, but if linux became standard there’s no reason hackers wouldn’t focus their efforts in that direction instead. As long as a user can execute software on their system, this possibility will remain. Especially when, just like with Windows, corporate installations of Linux on desktops would still have lots of systems without the most recent security updates.
Linux is more secure, but any appearance of near-invulnerability from end-user installed malware is due to lack of attention from hackers on a minority platform.
It’s less trivial to exploit l*x because it has a more time-tempered distributed eyeball QA system in place, is modular, has at least something of a security mindset sudo-baked-in, has less surface area in brand new untested whizbang “optional rollups” (+ telemetry as a feature) etc. Linus Torvalds isn’t making a quarter every time he sells your app usage history to advertisers, that’s not his motivation in keeping things secure. It’s a distributed largely volunteer effort securing it rather than a tacked-on afterthought QA round by a bloated massive corporate entity that views the exercise as a waste of resources at release date and expects you to wait for SP1 to realize you were firewall-naked the entire time.
There’s also a sizeable knowledge barrier to entry in using it which by default results in a more experienced and security conscious user base comparatively. So you’ve got all the world’s drones (not to say every user is per se, I am too) using Windows because it’s the easiest and most common, and they’ll be more likely to click on anything, go searching for video game hax or cracked (unverified) sw (or flash updates) in dimly lit places, don’t know how to use analytical tools or read man pages or why sudo is useful conceptually. That equates to a better chance to hit per swing regardless of the actual vuln count, which is also astronomical. https://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-32238/Microsoft-Windows-10.html – Set to vuln threshold of 8-9 and see how many pages of that there are. That’s a lot huh.
“It’s less trivial to exploit l*x because it has a more time-tempered distributed eyeball QA system in place, is modular, has at least something of a security mindset sudo-baked-in, has less surface area in brand new untested whizbang “optional rollups” (+ telemetry as a feature) etc. ”
The OpenSSL bug, Heartbleed, anyone? Two starving volunteers were in charge of that one.
Have a read of “This is the way they tell me the world ends.” A bug in an HP PRINTER DRIVER permitted the bad guys to view any document sent to it, for YEARS.
The brightest mind in the field estimated that any code over 3000 lines could harbor flaws that no one but the author could detect. The University of Minnesota got blackballed for deliberately inserting malware into Linux without warning to see if ‘the distributed eyeball QA system’ would catch it. It didn’t.
Rule 1: No physical security, no security
Rule 2: If you didn’t write and compile the code, no security
Rule 3: If you didn’t write the microcode for all the IC’s in the board, test all IC’s before they went on the board, after fabbing and secured the assembly plant, no security.
There was a video card whose driver permitted malware to be flashed to it. Full metal rebuild of machines STILL resulted in compromised machines. For fun, the Israelis work on ways to exfiltrate from air-gapped machines. You know how if the radio is off frequency in the right way, you can hear a change in pitch as the revs go up and down? You can do that with a hard drive and detect it, too. Fun, hey?
Yes, Linux is “hackable” but switching to Linux is going to put a much higher barrier in place than adding a Cyrillic keyboard to Windows.
Using Linux is horrifically laughable suggestion as it completely ignores the Biggest reason malware exists in the first place – to target lazy, incompetent people. Lazy, incompetent people won’t stop being lazy or incompetent simply because their OS has changed, despite your extremely naive assertion to the contrary. They will just create a demand for malware creators to target a broader range of OS’s. And everything it targettable. Everything.
Arrogance is the easiest to target and exploit of all. So seriously just stop please.
That’s to neglect the attack surface area in windows. A simple, easily-used OS doesn’t necessarily have to be completely ridiculously insecure featurebloat creepware like Windows is. It comes misconfigured out of the box and if you think it’s improving lately, that’s unintentionally hilarious. It definitely has room to improve in this domain.
Darkside software also actually encrypt Linux systems.
Even Autocad… and who’s still using Autocad? Even my last employer that still had machines with bubble memory and paper tape readers was using Autodesk Inventor for most mechanical design. Surprise, Inventor is Windows only. The major competition is Solidworks, which is also Windows only.
Um, the architecture world still uses Autocad, a lot. Not using solid works for that. Even if we start talking about using Revit, nope it won’t run on Linux either. Same with all of our design tools in the building systems design world to do cooling calcs, lighting calcs, air handler design tools from mfrs, coil programs, and on…. None of this will run on Linux or a Mac. I get it, I tinker with all systems, but in the business world, most devs just will not take the time (cost) to develop software for 3 different platforms to jump from 95% of users to 99%.
You can run Windows in a VM. Orders of magnitude better than bare metal.
If you have hard dependencies for insecure environments, why run them insecurely also?
Amiiiigaaaa
This is what I wanted to reply with also! Thank you for thinking so correctly of the least complicated a wonderfully engineered OS ever.
Define “recognizable.” I’m a court reporter. Software from the half-dozen companies that produce our choice of software packages runs only on Windows. Which is a relief, because it took forever to move from DOS.
Stenograph.com leases CaseCATalyst, arguably the best-known, most widely used software.
EclipseCAT.com leases Eclipse, a very close second, if not first by these days.
GSCLion.com leases StenoCAT.
Stenovations.com leases digitalCAT.
ProCAT.com leases Winner.
There may be at least one more that’s not coming to mind. A reporter pays their four to five thousand dollars for a lease plus seven to nine hundred dollars a year for support, and we get to run our software on Windows or not at all. This is cutting-edge, amazing software, definitely not legacy stuff.
Nor is it developed in-house. It is indeed business specific, but it’s definitely not Web- or Java-based. There are roughly 27,000 stenographic court reporters in the United States. Perhaps that’s a business opportunity you can mine by being first to market with ‘nix version.
The only reason Mac is not attacked nonstop is because no one uses it. Once upon a time I did photography work and I used both systems with Photoshop and Lightroom. Honestly, I don’t understand why anyone would use a Mac on purpose much less spend four times what it’s worth to buy one. I once used a generic $500 Acer from Walmart that would smoke any $2000 Mac Pro I ever used. Maybe big corporations don’t use them because their IT departments aren’t full of apple fanboys authorized to blow someone else’s money on overglorified garbage.
“I defy anyone to name me some recognizable software that will only run on Windows these days. ”
MS Access.
Done.
Excel.
Done.
No Mac Office doesn’t count. No proper VBA support.
MS Exchange.
Done.
Solidworks.
Done.
Don’t be silly.
You wanna work, you run Windows
I ran a (small… 12-person) company for 19 years on Linux. No Windows at all. It was eminently practical and saved us buckets of money.
So you’re suggesting that all end users make use of Linux workstations?
Because Linux/*nix/Mac OS’s/software never get hacked?
Compare #’s anytime, you’ll find that a strange brag.
That’s like saying “Chinese cars are safer than American cars because the former haven’t been involved in any of the accidents in the US”.
Well duh, of course they haven’t, nobody drives them.
Like anything else, the #’s mean nothing on their own, they need context.
Not total attacks, unfixed vulns. You’re right in that I didn’t specify.
This has and for always will be the most arrogant statement out there. Small business and specialty shops sometimes don’t have a choice, and the “perfect” worldview is just blind. “Find another vendor.” Sure, let me retrain, and reprogram every piece of software which would cost us more money over the course of 10 years versus just securing my network. Dumb.
Good trick Brian!
It’s a win win. You either get some level of vaccination or screw over some hacker 🙂
It’s not going to keep your pc 100% safe, but it’s better than nothing.
Would adding one of these languages on SERVERS which store vital data be enough? Or, would one need to install on all endpoints in order to protect data residing on servers?
The ransomware typically executes on the local workstation and encrypts data that is connected via mapped drives. In that case, putting these settings on servers wouldn’t have any effect. That being said, the ease with which someone could deploy these keyboards to every Windows machine in an environment seems to make it a win-win to do it to servers and workstations.
@Leann
No offense, but if you’re asking this, somebody else needs to handle it.
Why is it when people say “no offense” they always go on to say something that is offensive?? Is it just a way to try and make themselves sound less rude than they actually are?
Yes
rory, You may be right but Leann is reading Krebs and trying to make a difference in the position he’s been given.
Leann, Implementing this via GPO on everything would be one way to handle it. If you aren’t sure deploy everywhere 🙂
Thanks for your thoughts Andy. I agree, deploying the registry hack via GPO would be pretty easy. Certainly a worthy stop-gap!
Rory…..I appreciate your “concern”. I’m certainly not an information security SME…..but my powers to recognize a jack-ass are quite astute! You might consider keeping your replies productive and/or helpful.
Спасиво! I have to guess at the keyboard layout, though. Over 14 years ago I had 10 days in Ukraine, and I kinda-sorta remember some of the Cyrillic alphabet.
Would using the GoRussian.reg file you linked to have any downsides? Could it confuse a system or a user, or error out when the russian keyboard is in the registry but not actually installed?
Spouse asked an interesting question. Would having one of these keyboards installed on your computer make you subject to further NSA scrutiny, and possible placement on a watch list? I intially dismissed this as her extreme paranoia.
She suffers from a condition of believing everything on the internet is true, even if there are conflicting reports. Drives me nuts. However as soon as I said it was unlikely, I retracted my comment, because “you just never know anymore”. Maybe one of your readers can provide her, and now me, with some reassurance that this would not be the only possible downside.
The number of people with Russian keyboards installed in the US would be so large as to be utterly meaningless monitoring metric.
I don’t see why it would.
That alone isn’t a flag for concern any more than installing an Arabic language as there’s far far too many legitimate use cases that are a total utter and useless waste of resources. The collection methods are based more on sniffing and pattern matching, you have to remember, they’re monitoring literal millions already. Machine filtering is what’s going to do the bulk heavy work of sifting the data. Now, if you go talking about something like “flying a Cessna into the Sears Tower on May 9th 2013 at 19:21Z”, you’ll more likely get flagged, irrelevant of what language. I understand there’s the principal of “muh privacy!” and that’s a heavily debatable topic of “does it matter” (which I’m not getting into, the answer is extremely individualized), but simply changing the language of your computer isn’t going to put you onto a watchlist. That’s like taking someone into custody because they live next to a corner store that was robbed; there’s just nowhere near a viable amount of reason for suspicion.
Let’s go with the radical assumption they do. Now they’re digging through your web traffic history, and trying to build a profile on you. Well, you visited this page and then within a short time after you added a language to your computer. Nothing else of your history is suspicious, you weren’t looking up info of refining uranium, how to make methyl-mercury, how to make explosives, or crazy weird suspicious things (I’m assuming). You have zero connection with known high profile targets. You probably haven’t talked to anyone else on a watch list. Now they’ve wasted resources on a dead end, they’re going to dismiss you unless you do some really crazy weird stuff that gets you flagged again.
Thank you for your comments. Our paranoia level dropped significantly. Mine from about 10 on the scale of 1 to 100. I don’t think we will ever be able to talk her down below 90.
Do yourself a favor.
DON’T read “This is How They Tell Me The World Ends” by Nicole Perlroth.
Your paranoia will never drop below 100 again.
Mine never will.
When PRINTERS can be hacked to phone home to the NSA about anything and everything–well, I never expected that.
It is not far-fetched to believe that the NSA has compromised every single router on earth. They have a hard time dealing with all the data. That’s what AI is for. Have a look at any box and ask yourself “Is this ACTUALLY patched against EternalBlue?” Usually. Now ask “Is every single box on the network patched against EternalBlue?” Probably not. And one is all it takes.
They don’t look for pidly sh!t like that at NSA and “decide” to keep tabs on you. Xkeyscore may give you a +1 at most.
They don’t keep track of all Russians in the world, they keep track of everybody they can see. Being Russian != threat.
If you have a specific history or associations or traffic or environment they’re interested in, it won’t be the language.
Either way “they” keep tabs on everything in this ranked criteria way, not just Russians or Chinese or Iranians.
I entirely doubt and hope for your sake that your wife is not that interesting to them on any level.
Haven’t your heard? The most serious existential threat facing the US is not Russia, it is the Climate. So, the NSA won’t be looking for a Russian language pack on your computer. However, if you have the Accuweather app installed, you might have a couple guys with black umbrellas show up at your door one day.
I feel I need to correct a few things here. First of all, saying Romania has “favorable” relations with Russia is an overstatement to the fullest, given the recent dignitary expulsion game between the two countries.
Secondly, what you’re picturing there is the “Romanian(Moldova)” keyboard layout, one specifically for the country known as Moldova, so it would easily infect my one Windows device using “Romanian(Programmers)” keyboard layout, the exclusion solely applies to Moldavians instead.
I second what Codin said.
I’m glad someone typed it already so I don’t have to.
I was going to say the same. Furthermore, to say that Georgia has a friendly attitude towards Kremlin shows a severe lack of knowledge about recent history (the two countries were briefly at war in 2008, and the present-day relationship between them is still sour). Also, the CIS is not composed of former “Soviet satellites”, but of former Soviet republics (i.e. which were part of the USSR). The author of this blog post seems to be quite young and with no memories from before ’89.
What of us running on the Mac OS? Is this relevant?
Right. For my family history work, I added keyboard settings on my iMac for a half dozen western European languages.
I wonder whether including the other languages mentioned above would help at all?
The real Win-Win scenario would be if we could to change the code in the malware and remove the refence to some of the Eastern European countries. Then Russia would have some skin in the game…
This is not a “host” of Eastern European countries — only 3 (and part of Russia) are in Eastern Europe. 8 (and most of Russia) are in Asia.
A truly Russian/CIS system will have only a Russian/CIS keyboard, and in the odd case it does have an English keyboard, that will be listed 2nd. It seems rather trivial to me that Darkside would just check to see if the default keyboard is English or Russian. I guess a decent defense might be to reinstall Windows with the Russian keyboard as default and then add English, but I doubt many English-speaking people could navigate a Windows install in Russian.
Correct. And correct again.
I live in Russia, and I have never encountered a computer without an English keyboard here
They will start using IP geolocation instead, so this only buys a very brief respite.
Now that this trick on the lose, I assume those hackers will “update” their malwares to detect the system language of the Windoze…. more safe for their “apps” lol
I worry about our three electric grids being sabotaged by Russia, N Korea or China, they are biding their time as to when it will happen, not if. We are doing nothing about it.
Texas is more than capable of destroying its own electric grid without any outside interference except for a winter cold spell (who knew it would get cold in winter?).
Having worked on and designed grid control networks I fail to see how exactly they would be easily infected, there is no internet and the majority of them uses protocols that Joe hacker has never heard of like LAT etc and dumb terminals there isn’t a windows or Mac to be seen in a properly build grid control network nor is there internet
Stuxnet, anyone? That got by air-gapping–and got back out again too and attacked the wider world.
PLC controllers can get hacked.
And ask the Ukrainians how fun it is when the Russkies crash the grid.
They’ve been there, done that.
Twice.
“hit the Windows key and the space bar at the same time”
Should be win + shift, not space.
Just tried your solution and nothing happened. Windows + Spacebar works fine.
Win + shift open the Windows Start menu by default.
By that approach cover all the bases and install Russian, Chinese, Korean and Farsi. Now you just have to worry about offensive software which only affects clients where Russian, Chinese, Korean and Farsi are installed. Or employ the more simplistic solution, don’t use Windows. Then keep worrying about the fleshy thing between the monitor and keyboard.
Well, the North Koreans would gladly attack your machine if it smells South Korean…
How about Russian Linux/UNIX Malware? Is there such thing and does it use the same check?
Hoping for some feedback, I installed the registry hack by Unit221B by double clicking on .reg file with install successful confirmation. I then verified enclosed keys were added to registry. Rebooted machine.
However, Windows+shift or +space bar do not invoke pop up/language toggle as suggested. Am I incorrect in assuming that this toggle should be available due to registry hack only, not actually having Russian language pack installed?
No. As it says in the Github entry, if you use the registry hack then “alt+shift” toggles the language setting.
https://github.com/Unit221B/Russian
Double-click the reg file hit alt-shift to switch from your main keyboard language and russian.
Folks should be advised that many of the Microsoft KB advisories for patches or updates mentioned that they will need to be re-installed if additional languages are added. For years many patch advisory documents contained the warning:
“Important If you install a language pack after you install this update, you must reinstall this update.”
So BEWARE that rushing off and adding a language to your Windows systems might have unintended consequences with regards to patches and updates. I’m not sure if security could be compromised, or it will be odd languaged / localization functional issues.
Unless this is false, this is a good reason to not install the reg patch, right?
This is indeed true.,
A simple DuckDuckGo search for the string:
“Important If you install a language pack after you install this update, you must reinstall this update.”
(including the quotation marks) will reveal the scope and details on the Microsoft patches and updates that could be affected by adding a language pack.
My perspective on the topic is that the risk of possibly introducing problems with previously installed security related patches is greater than any theoretical benefit of this supposed protection.
That being said, I’m sure that someone will question why adding a language pack would affect a security patch. I agree that it SHOULD not be that way. However this is Microsoft, and there is the re-install advisement in so many advisories. Without thorough testing to prove otherwise, I would take Microsoft at their word.
Brian,
You/we should ask Microsoft to make this part of their patch tuesday updates!!
Lots of malware will not work if it looks like it is in a virtual machine once installed. The HitmanPro.Alert AV program takes advantage of this, and upon installation, makes the user’s computer look like it is a virtual machine.
Ukraine hasn’t been involved in the CIS since the Maidan coup.
So they have to change their code, still fun to think they have been inconvenienced a little.
Good idea! Then you’ll be hacked by the CIA instead. 🙂
That’s all fine and well until one of the 3 letter agencies decides they wanna release a virus that targets Russian computers.
I am afraid the trick doesn’t work.
Before encryption, DarkSide checks for the language of the Operating System by using GetSystemDefaultUILanguage() and GetUserDefaultLangID() functions. It skips encryption if any of the languages identified by Cybereason is returned by one of those two functions.
Those functions are used to cover extensively old and new versions of Windows.
GetSystemDefaultUILanguage is a deprecated function, used on Windows before and including 8, which reports the language used during installation, and it never changes. So if you used one of those languages during installation, it could work; however, you have to install Windows in Russian, and only later switch it to English 🙂
GetUserDefaultLangID instead is a newer function, that returns the current language of the user, the same that is retrieved by default from Control Panel. Again, if you are not currently using Russian or another of those languages above, it’s worthless.
I am afraid, simply adding a fake keyboard is not going to help. Nice try though 🙂
Thank you Marco! Exactly! I was scrolling through comments trying to find SOMEONE, ANYONE, who actually knows this, and I am glad that there was someone who finally pointed this out.
Additionally, people should read the Intel 471 report “REvil Ransomware-as-a-Service: An analysis of a ransomware affiliate operation” from March 31, 2020. It shows that yeah, there is a list of whitelisted keyboards, BUT clearly states that “For the check to succeed and REvil to exit, both a whitelisted system language and a whitelisted keyboard layout must be present. Otherwise, the ransomware continues its execution normally.”
I see too many subpar individuals with high-paying jobs in the industry because they are great at networking and promoting themselves on Twitter. Sure, it’s the case with almost every industry, but in this industry there are tangible consequences.
Brian, your blog has been and will always be one of the top infosec resources on my list, but I feel like this piece was a little weaker than usual.
> former Soviet satellites that all currently have favorable relations with the Kremlin, including Azerbaijan, Belarus, Georgia, Romania, Turkmenistan, Ukraine and Uzbekistan.
Just an FYI, as of today, Ukraine does not have any favorable relations with the Kremlin. In fact there is a war going on between this two countries.
“all currently have favorable relations with the Kremlin, including Azerbaijan, Belarus, Georgia, Romania, Turkmenistan, Ukraine and Uzbekistan.”
It’s not exactly the case. There is a war between Russia and Ukraine. Ukraine is not a member of CIS. Georgia is not a member of CIS as well.
The same can be told about Romania (they do however tend to be friendlier with Moldova actually, uses the same language but used to be in the former USSR).
What about the other „services“ that find windows machines with Cyrillic keyboards an interesting target?
There is a versed saying in Russian cybersecurity industry which I already posted in the Twitter thread, but decided to cite here as well for the blog readers’ enjoyment:
Кто рабо́тает по “ру”, к тем прихо́дят поутру́ ‘those [cybercriminals] who work against RU[ssian websites/services] get visited in the mornings [by the police]’