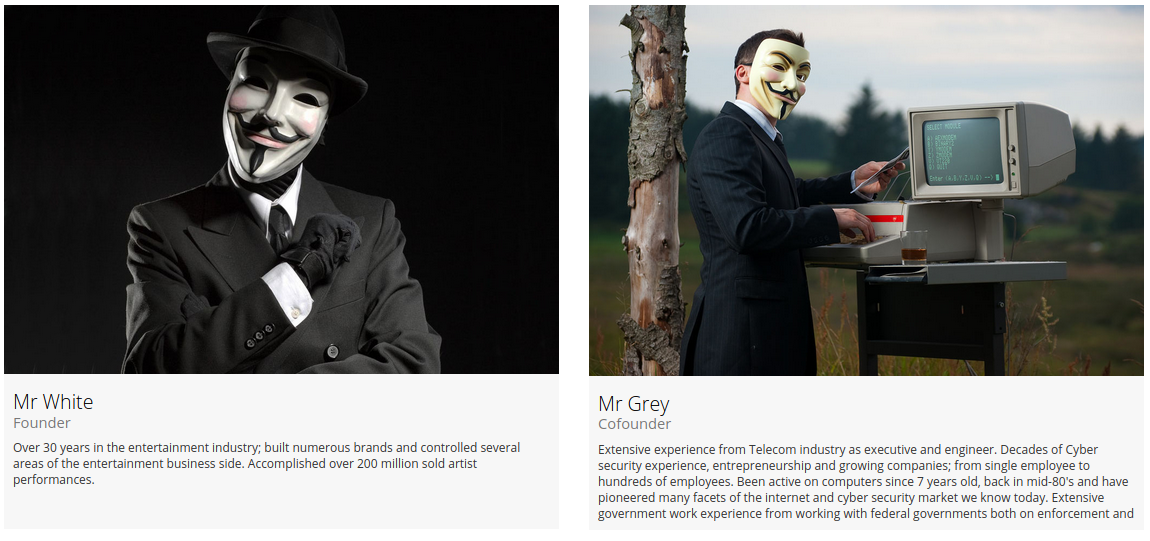
RedTorch Formed from Ashes of Norse Corp.
Remember Norse Corp., the company behind the interactive “pew-pew” cyber attack map shown in the image blow? Norse imploded rather suddenly in 2016 following a series of managerial missteps and funding debacles. Now, the founders of Norse have launched a new company with a somewhat different vision: RedTorch, which for the past two years has marketed a mix of services to high end celebrity clients, including spying and anti-spying tools and services.