Tag Archives: Namecheap
.US Harbors Prolific Malicious Link Shortening Service
The top-level domain for the United States — .US — is home to thousands of newly-registered domains tied to a malicious link shortening service that facilitates malware and phishing scams, new research suggests. The findings come close on the heels of a report that identified .US domains as among the most prevalent in phishing attacks over the past year.
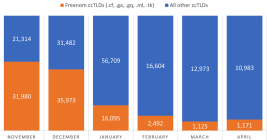
Phishing Domains Tanked After Meta Sued Freenom
The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from social networking giant Meta, which alleged the free domain name provider has a long history of ignoring abuse complaints about phishing websites while monetizing traffic to those abusive domains.
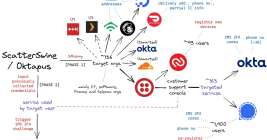
GoDaddy Employees Used in Attacks on Multiple Cryptocurrency Services
Bad .Men at .Work. Please Don’t .Click
Web site names ending in new top-level domains (TLDs) like .men, .work and .click are some of the riskiest and spammy-est on the Internet, according to experts who track such concentrations of badness online. Not that there still aren’t a whole mess of nasty .com, .net and .biz domains out there, but relative to their size (i.e. overall number of domains) these newer TLDs are far dicier to visit than most online destinations.
Carders Park Piles of Cash at Joker’s Stash
A steady stream of card breaches at retailers, restaurants and hotels has flooded underground markets with a historic glut of stolen debit and credit card data. Today there are at least hundreds of sites online selling stolen account data, yet only a handful of them actively court bulk buyers and organized crime rings. Faced with a buyer’s market, these elite shops set themselves apart by focusing on loyalty programs, frequent-buyer discounts, money-back guarantees and just plain old good customer service.