A decade ago, if a desktop computer got infected with malware the chief symptom probably was an intrusive browser toolbar of some kind. Five years ago you were more likely to get whacked by a banking trojan that stole all your passwords and credit card numbers. These days if your mobile or desktop computer is infected what gets installed is likely to be “ransomware” — malicious software that locks your most prized documents, songs and pictures with strong encryption and then requires you to pay for a key to unlock the files.
Here’s some basic advice about where to go, what to do — and what not to do — when you or someone you know gets hit with ransomware.
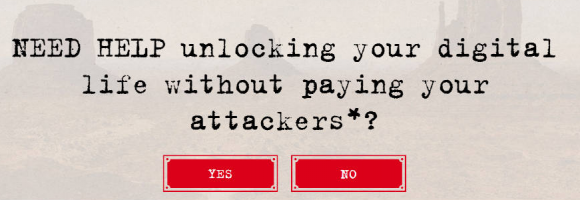
Image: nomoreransom.org
First off — breathe deep and try not to panic. And don’t pay the ransom.
True, this may be easier said than done: In many cases the ransom note that hijacks the victim’s screen is accompanied by a digital clock ominously ticking down the minutes and seconds from 72 hours. When the timer expires, the ransom demand usually goes up or even doubles. Continue to ignore the demands and your files will be gone, kaput, nil, nyet, zilch, done forever, warns the extortion message.
See, the key objective of ransomware is a psychological one — to instill fear, uncertainty and dread in the victim — and to sow the conclusion in the victim’s mind that any solution for restoring full access to all his files involves paying up. Indeed, paying the ransom is often the easiest, fastest and most complete way of reversing a security mistake, such as failing to patch, opening a random emailed document e.g., or clicking a link that showed up unbidden in instant message. Some of the more advanced and professional ransomware operations have included helpful 24/7 web-based tech support.
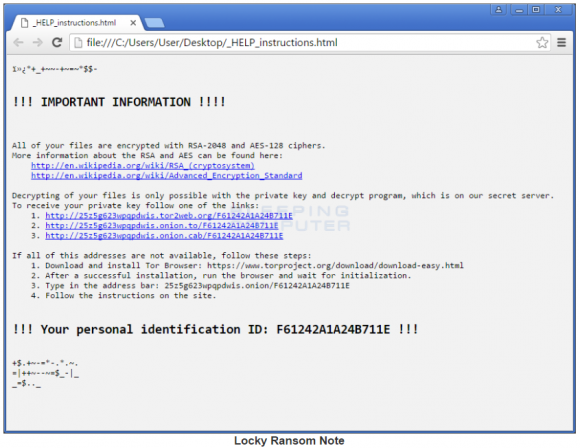
The ransom note from a recent version of the “Locky” ransomware variant. Image: Bleepingcomputer.com.
Paying up is certainly not the cheapest option. The average ransom demanded is approximately $722, according to an analysis published in September by Trend Micro. Interestingly, Trend found the majority of organizations that get infected by ransomware end up paying the ransom. They also found three-quarters of companies which had not suffered a ransomware infection reported they would not pay up when presented with a data ransom demand. Clearly, people tend to see things differently when they’re the ones in the hot seat.
And for those not yet quite confident in the ways of Bitcoin (i.e. most victims), paying up means a crash course in acquiring the virtual currency known as Bitcoin. Some ransomware attackers are friendlier than others in helping victims wade through the process of setting up an account to handle Bitcoin, getting it funded, and figuring out how to pay other people with it. Others just let you figure it all out. The entire ordeal is a trial by fire for sure, but it can also be a very expensive, humbling and aggravating experience.
In the end the extortionist may bargain with you if they’re in a good mood, or if you have a great sob story. But they still want you to know that your choice is a binary one: Pay up, or kiss your sweet files goodbye forever.
This scenario reminds me of the classic short play/silent movie about the villainous landlord and the poor young lady who can’t pay the rent. I imagine the modern version of this play might go something like…
 Villain: You MUST pay the ransom!
Villain: You MUST pay the ransom!
Victim: I CAN’T pay the ransom!
Villain: You MUST pay the ransom!
Victim: I CAN’T pay the ransom!
Hero: I’ll pay the ransom!
Victim: Oh! My hero!
Villain: Curses! Foiled again!
Okay, nobody’s going to pay the ransomware demand for you (that’s only in Hollywood!). But just like the hero in the silent movie, there are quite a few people out there who are in fact working hard to help victims avoid paying the ransom (AND get their files back to boot).
Assuming you don’t have a recent backup you can restore, fear not: With at least some strains of ransomware, the good guys have already worked out a way to break or sidestep the encryption, and they’ve posted the keys needed to unlock these malware variants free of charge online.
But is the strain that hit your device one that experts already know how to crack? Continue reading











 “The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”
“The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”