Hospitality giant Hilton Hotels & Resorts recently started offering Hilton HHonors Awards members 1,000 free awards points to those who agreed to change their passwords for the online service prior to April 1, 2015, when the company said the change would become mandatory. Ironically, that same campaign led to the discovery of a simple yet powerful flaw in the site that let anyone hijack a Hilton Honors account just by knowing or guessing its valid 9-digit Hilton Honors account number.
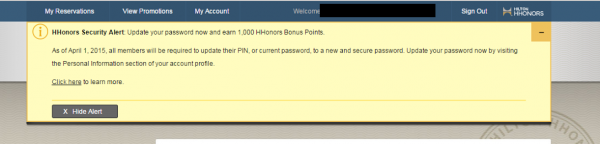
Until it was notified by KrebsOnSecurity about a dangerous flaw in its site, Hilton was offering 1,000 points to customers who changed their passwords before April 1, 2015.
The vulnerability was uncovered by Brandon Potter and JB Snyder, technical security consultant and founder, respectively, at security consulting and testing firm Bancsec. The two found that once they’d logged into a Hilton Honors account, they could hijack any other account just by knowing its account number. All it took was a small amount of changing the site’s HTML content and then reloading the page.
After that, they could see and do everything available to the legitimate holder of that account, such as changing the account password; viewing past and upcoming travel; redeeming Hilton Honors points for travel or hotel reservations worldwide; or having the points sent as cash to prepaid credit cards or transferred to other Hilton Honors accounts. The vulnerability also exposed the customer’s email address, physical address and the last four digits of any credit card on file.
I saw this vulnerability in action after giving Snyder and Potter my own Hilton Honors account number, and seconds later seeing screen shots of them logged into my account. Hours after this author alerted Hilton of the discovery, the Hilton Honors site temporarily stopped allowing users to reset their passwords. The flaw they discovered now appears to be fixed.
“Hilton Worldwide recently confirmed a vulnerability on a section of our Hilton HHonors website, and we took immediate action to remediate the vulnerability,” Hilton wrote in an emailed statement. “As always, we encourage Hilton HHonors members to review their accounts and update their online passwords regularly as a precaution. Hilton Worldwide takes information security very seriously and we are committed to safeguarding our guests’ personal information.” Continue reading