Federal authorities in New Jersey announced a series of arrests and indictments of 14 individuals thought to be connected to an online one-stop shop selling embossed, counterfeit credit cards and holographic overlays.
According to documents released by prosecutors in New Jersey and North Carolina, the men ran or otherwise profited from the Web site fakeplastic[dot]net, which specializes in selling high-quality, custom-made counterfeit credit and debit cards, as well as holographic overlays used to create fake driver’s licenses.
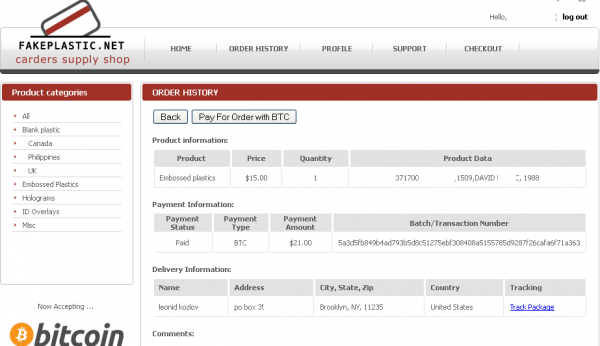
![A customer's purchases from fakeplastic[dot]net, which federal authorities secretly seized on Dec. 5, 2013.](https://krebsonsecurity.com/wp-content/uploads/2014/01/FakePlastic-600x319.png)
A customer’s purchases from fakeplastic[dot]net, which federal authorities secretly seized on Dec. 5, 2013.
The FBI and the U.S. Postal Investigative Service began investigating fakeplastic[dot]net in January 2013. Charged with running the site is 39-year-old Sean Roberson of Palm Bay, Fla. Investigators allege that Roberson began selling counterfeit cards in April 2011, and launched the site in June 2012. Since then, Roberson and two accomplices fulfilled orders for approximately 69,000 counterfeit cards — both embossed and unembossed; more than 35,000 holographic stickers used to make counterfeit cards appear more legitimate; and more than 30,000 state identification card holographic overlays. All of the orders — 36,000 parcels in total — were shipped by the site to customers via the U.S. mail.
Using a conservative estimate of loss of $500 associated with each counterfeit payment card (derived from the federal sentencing guidelines estimation of loss associated with stolen payment card information), prosecutors estimate the losses associated with just the counterfeit payment cards trafficked by Roberson and his conspirators at more than $34.5 million. The complaint against Roberson alleges that he personally made more than $1.7 million from the scheme.
According to the Justice Department, fakeplastic[dot]net was used by various groups of criminals across the country often referred to as “carding” or “cash out” crews. These crews buy stolen payment card numbers and related information – referred to as “track data” or “dumps” – which typically appear on the magnetic stripe on the back of legitimate payment cards. Illegal vendors of that information usually get it through hacking or skimming operations involving the installation of specialized equipment at ATM locations or point-of-sale terminals. The stolen data is ultimately put on a blank card and used to make unauthorized transactions.
“More sophisticated cash out operations use custom-made counterfeit payment cards embossed with the same account numbers that have been encoded on the back of the card, and often acquire fake identification cards in order to reduce the likelihood of detection from law enforcement,” reads a press release issued Thursday by New Jersey U.S. Attorney Paul J. Fishman and U.S. Attorney Anne M. Tompkins for the Western District of North Carolina. “The criminal underground has evolved from fractured, regional operations to an Internet-based market where buyers and sellers across the globe can advertise, purchase and transmit stolen track data. The fakeplastic website brought the physical tools needed by cash out operations to the world of e-commerce, as it eliminated the need for crews to purchase expensive hardware.”
The Justice Department says that by December 2013 — when federal agents quietly assumed control over fakeplastic[dot]net, the site had more than 400 members. Members with access to the fakeplastic website and seeking to purchase counterfeit payment cards could browse the website’s available counterfeit card templates. Members could then choose whether to input specific information to be embossed on the cards and whether they wanted additional authentication features – such as holographic stickers.
OPSEC IS HARD; LET’S GO TO DOLLYWOOD!
As is the case with many an online scam operation, the whole thing falls apart when key members fail to exercise proper operational and personal security habits. After assuming control over the card shop, federal agents made purchases through the site to learn more about the service’s shipping methods. According to charging documents, investigators confirmed that the Fakeplastic Click-N-Ship account used to generate the tracking number associated with the undercover purchases was registered to a “Sam Adams,” with a mailing address for a university in Florida, and that the email address associated with this account was budlighthouse@gmail.com (the “Budlighthouse Gmail Account”).
After obtaining a warrant to inspect that Gmail account, federal investigators discovered that all of the Web site’s order emails were sent to this address and to the address platplus@tormail.net. Tormail is a hidden service on the Tor darkweb network that allows users to send and receive email anonymously to addresses inside and outside of Tor, an anonymity network that is not reachable from the regular Internet and requires the use of special software to reach.
Interestingly, the feds used information gleaned from an incident last summer in which federal agents compromised TorMail as part of an investigation into a child pornography network. To wit:
Between July 22, 2013 and August 2, 2013, in connection with an unrelated criminal investigation, the FBI obtained a copy of a computer server located in France via a Mutual Legal Assistance Treaty request to France, which contained data and information from the Tormail email server, including the content of Tormail e-mail accounts. On or about September 24, 2013, law enforcement obtained a search warrant to search the contents of the Platplus Tormail Account, which resided on the seized Tormail server.









![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)