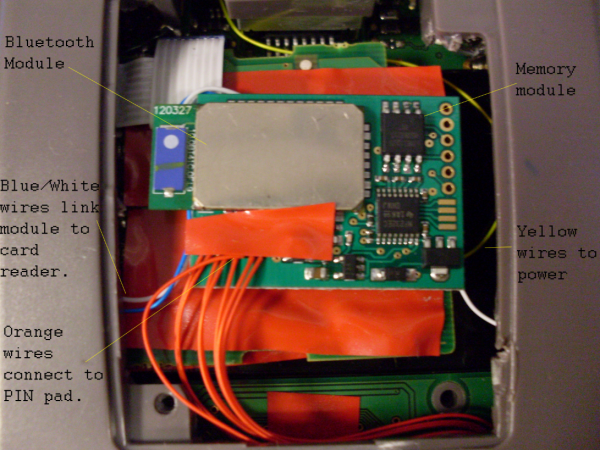
Microsoft and Symantec said Wednesday that they have teamed up to seize control over the “Bamital” botnet, a multi-million dollar crime machine that used malicious software to hijack search results. The two companies are now using that control to alert hundreds of thousands of users whose PCs remain infected with the malware.
 The tech firms said their research shows that in the last two years, more than eight million computers have been attacked by Bamital, and that the botnet’s search hijacking and click fraud schemes affected many major search engines and browsers, including those offered by Microsoft, Yahoo and Google.
The tech firms said their research shows that in the last two years, more than eight million computers have been attacked by Bamital, and that the botnet’s search hijacking and click fraud schemes affected many major search engines and browsers, including those offered by Microsoft, Yahoo and Google.
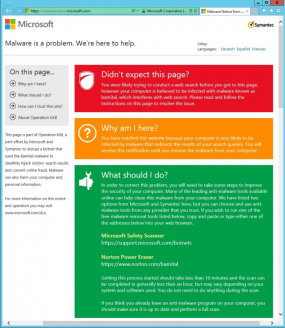
Users of machines infected with Bamital are likely to see a Web page like the one pictured at right the next time they search for something online. That’s because Microsoft convinced a judge at the U.S. District Court for the Eastern District of Virginia to give it control over the infrastructure that Bamital used to coordinate the search hijacking activities of host PCs.
On Wednesday, technicians working on behalf of both Microsoft and Symantec raided data centers at Leaseweb USA in Manassas, Va., and ISPrime in Weekawken, New Jersey, accompanied by U.S. federal marshals. The two companies are now using the botnet’s control channels to communicate with infected PCs and to notify affected users.
According to Microsoft’s lawsuit, Bamital is most often installed via drive-by downloads, which use exploit kits stitched into hacked and malicious Web sites. Microsoft said the bad guys behind the botnet exclusively used the Phoenix Exploit Kit, a malware tool that uses vulnerabilities in Web browsers to silently install malware.
Bamital alters the organic search results on the host machine, redirecting victims away from sites as indexed by the major search providers toward pages that provide advertising and referral commissions to affiliate marketers. Redmond included several examples in its petition to the court, such as when a victim with Bamital searches for Microsoft Halo, and upon clicking the top link in the results is taken to a completely different set of search engine results.
Microsoft said Bamital also orders infected systems to participate in “click fraud,” or to generate automated Internet traffic by instructing those computers — without the owner’s knowledge or intervention — to connect to any Web site chosen by the botmasters. Meanwhile, the owner of the infected computer – even if they were sitting at the computer – would not see the hidden browser.
It’s not hard to see why threats like Bamital are so prevalent: An estimated $12.7 billion was spent on Internet advertising in 2012, and click fraud is taking a huge bite out of the expected returns. Microsoft’s own research indicates that 22 percent of all ad-clicks are fraudulent.