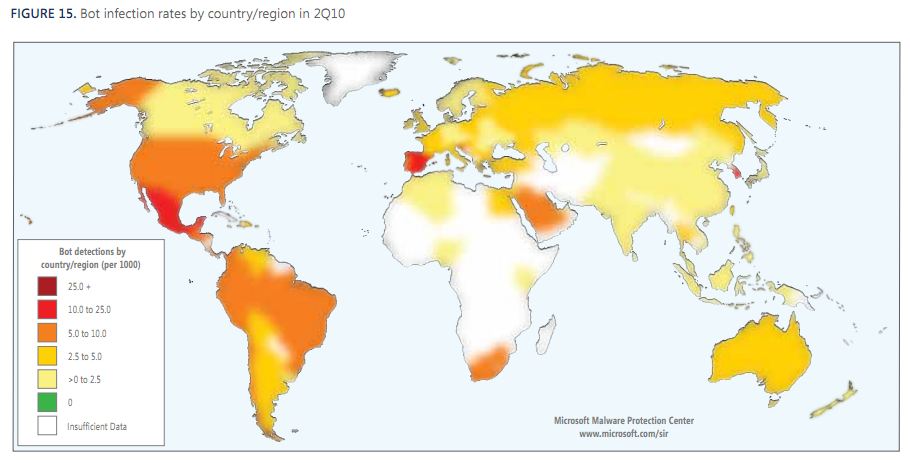
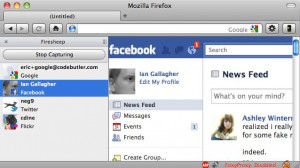
“Firesheep,” a new add-on for Firefox that makes it easier to hijack e-mail and social networking accounts of others who are on the same wired or wireless network, has been getting some rather breathless coverage by the news media, some of whom have characterized this a new threat. In reality, this tool is more of a welcome reminder of some basic but effective steps that Internet users should take to protect their personal information while using public networks.
 Most online services use secure sockets layer (SSL) encryption to scramble the initial login — as indicated by the presence of “https://” instead of “http://” in the address field when the user submits his or her user name and password. But with many sites like Twitter and Facebook, subsequent data exchanges between the user and the site are sent unencrypted and in plain text, potentially exposing that information to anyone else on the network who is running a simple Web traffic snooping program.
Most online services use secure sockets layer (SSL) encryption to scramble the initial login — as indicated by the presence of “https://” instead of “http://” in the address field when the user submits his or her user name and password. But with many sites like Twitter and Facebook, subsequent data exchanges between the user and the site are sent unencrypted and in plain text, potentially exposing that information to anyone else on the network who is running a simple Web traffic snooping program.
Why should we care if post-login data is sent in unencrypted plain text? Most Web-based services use “cookies,” usually small, text-based files placed on the user’s computer, to signify that the user has logged in successfully and that he or she will not be asked to log in again for a specified period of time, usually a few days to a few weeks (although some cookies can be valid indefinitely).
The trouble is that the contents of these cookies frequently are sent unencrypted to and from the user’s computer after the user has logged in. That means that an attacker sniffing Web traffic on the local network can intercept those cookies and re-use them in his own Web browser to post unauthorized Tweets or Facebook entries in that user’s name, for example. This attack could also be used to gain access to someone’s e-mail inbox.
Enter Firesheep, a Firefox add-on released this past weekend at the Toorcon hacker conference in San Diego. Eric Butler, the security researcher who co-authored the tool, explains some of the backstory and why he and a fellow researcher decided to release it:
“This is a widely known problem that has been talked about to death, yet very popular websites continue to fail at protecting their users. The only effective fix for this problem is full end-to-end encryption, known on the web as HTTPS or SSL. Facebook is constantly rolling out new ‘privacy’ features in an endless attempt to quell the screams of unhappy users, but what’s the point when someone can just take over an account entirely?”
In his blog post about Firesheep, I believe Butler somewhat overstates the threat posed by this add-on when he says: “After installing the extension you’ll see a new sidebar. Connect to any busy open wifi network and click the big ‘Start Capturing’ button. Then wait.”