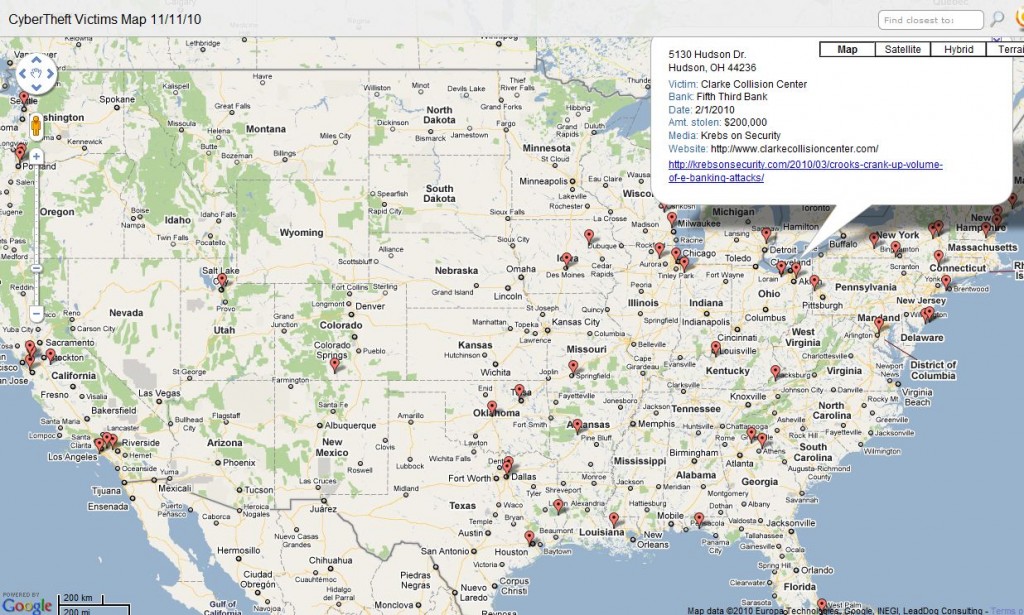
Hacked and malicious sites designed to steal data from unsuspecting users via malware and phishing are a dime a dozen, often located in the United States, and are a key target for takedown by ISPs and security researchers. But when online miscreants seek stability in their Web projects, they often turn to so-called “bulletproof hosting” providers, mini-ISPs that specialize in offering services that are largely immune from takedown requests and pressure from Western law enforcement agencies.
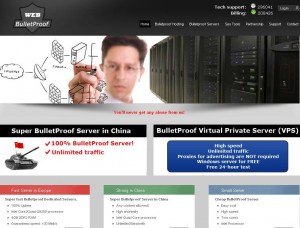 Until recently, you more or less had gain access to and lurk on the right underground forums to be able to rent services from bulletproof hosting providers. These days, it’s becoming easier to find these badware havens advertising out in the open. Last week, I traced the activities of one particular service frequented by criminals back to a bulletproof provider whose slogan says it all: “You’ll Never Get Any Abuse From Us!”
Until recently, you more or less had gain access to and lurk on the right underground forums to be able to rent services from bulletproof hosting providers. These days, it’s becoming easier to find these badware havens advertising out in the open. Last week, I traced the activities of one particular service frequented by criminals back to a bulletproof provider whose slogan says it all: “You’ll Never Get Any Abuse From Us!”
Of course, just how insulated this particular provider’s services are and how much illicit activity you can get away with while using them depends largely on how much you’re willing to shell out each month. For example, an entry level “default bulletproof server” allows customers to host things like rogue online pharmacies, replica, gambling, and MP3 sites for $270 per month. But this service level bars customers from hosting nastier content, such as malware, spyware, adware, exploits, viruses, and phishing sites.
 Upgrade to the “Super BulletProof Virtual Dedicated Servers in China” — and pay almost $500 a month — and the only activities that are prohibited are sending spam and hosting any type of porn.
Upgrade to the “Super BulletProof Virtual Dedicated Servers in China” — and pay almost $500 a month — and the only activities that are prohibited are sending spam and hosting any type of porn.
The provider pictured here also upsells potential customers by offering a variety of handy add-on services. For extra coin each month, one can rent a bulletproof server with a license for XRumer, a black hat search engine manipulation tool that automates the registration of new Web forum accounts and the spamming of links on those forums, all in a bid to boost the search engine rankings of the spamvertized site. If you operate a blog and have had to deal with what appear to be automated, link-filled comments, chances are good that XRumer was involved in some way.
For a $20 one-time setup fee, your server will come pre-packaged with links for forums that XRumer is able to spam, including thousands of Web pages in top-level domains that are often given more ranking weight by search engines, such as .edu, .gov and .mil.
[EPSB]
Have you seen:
Earn a Diploma from Scam U…Since the dawn of the Internet, tutorials showing would-be scammers how to fleece others have been available online. But for novices who can’t be bothered to scour the Net for these far flung but free resources, the tricks of the trade now can be learned through the equivalent of community college classes in e-thievery, or or via intensive, one-on-one online apprenticeships.
[/EPSB]
![]() Adobe on Tuesday issued a critical update to patch at least two security holes in its PDF Reader and Acrobat software, including one flaw that was publicly disclosed earlier this month.
Adobe on Tuesday issued a critical update to patch at least two security holes in its PDF Reader and Acrobat software, including one flaw that was publicly disclosed earlier this month.