Fake, positive reviews have infiltrated nearly every corner of life online these days, confusing consumers while offering an unwelcome advantage to fraudsters and sub-par products everywhere. Happily, identifying and tracking these fake reviewer accounts is often the easiest way to spot scams. Here’s the story of how bogus reviews on a counterfeit Microsoft Authenticator browser extension exposed dozens of other extensions that siphoned personal and financial data.
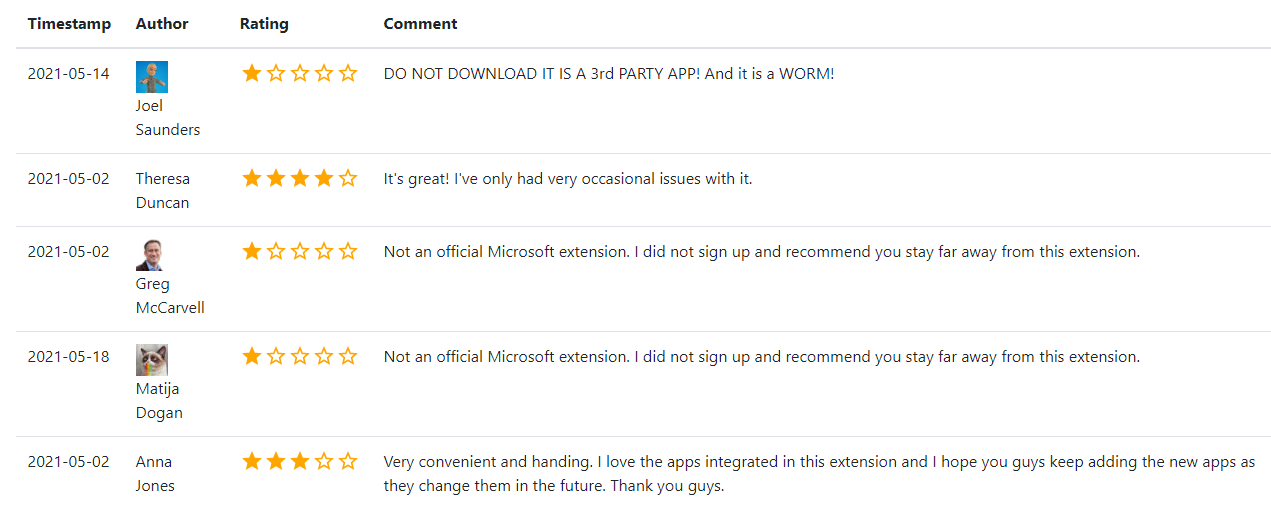
Comments on the fake Microsoft Authenticator browser extension show the reviews for these applications are either positive or very negative — basically calling it out as a scam. Image: chrome-stats.com.
After hearing from a reader about a phony Microsoft Authenticator extension that appeared on the Google Chrome Store, KrebsOnSecurity began looking at the profile of the account that created it. There were a total of five reviews on the extension before it was removed: Three Google users gave it one star, warning people to stay far away from it; but two of the reviewers awarded it between three and four stars.
“It’s great!,” the Google account Theresa Duncan enthused, improbably. “I’ve only had very occasional issues with it.”
“Very convenient and handing,” assessed Anna Jones, incomprehensibly.
Google’s Chrome Store said the email address tied to the account that published the knockoff Microsoft extension also was responsible for one called “iArtbook Digital Painting.” Before it was removed from the Chrome Store, iArtbook had garnered just 22 users and three reviews. As with the knockoff Microsoft extension, all three reviews were positive, and all were authored by accounts with first and last names, like Megan Vance, Olivia Knox, and Alison Graham.
Google’s Chrome Store doesn’t make it easy to search by reviewer. For that I turned to Hao Nguyen, the developer behind chrome-stats.com, which indexes and makes searchable a broad array of attributes about extensions available from Google.
Looking at the Google accounts that left positive reviews on both the now-defunct Microsoft Authenticator and iArtbook extensions, KrebsOnSecurity noticed that each left positive reviews on a handful of other extensions that have since been removed.
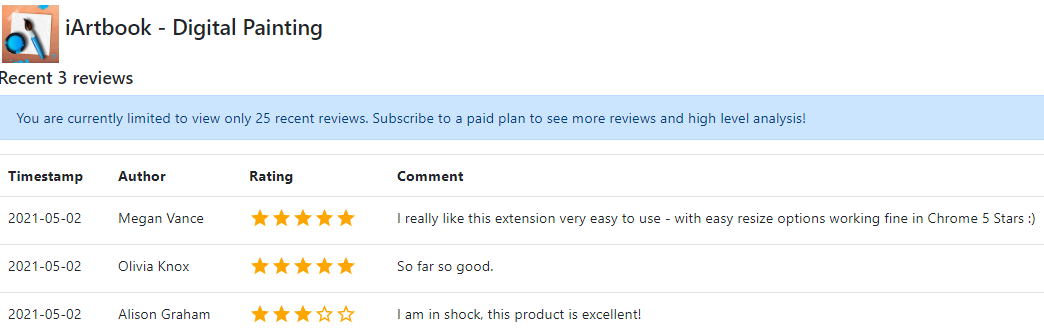
Reviews on the iArtbook extension were all from apparently fake Google accounts that each reviewed two other extensions, one of which was published by the same developer. This same pattern was observed across 45 now-defunct extensions.
Like an ever-expanding venn diagram, a review of the extensions commented on by each new fake reviewer found led to the discovery of even more phony reviewers and extensions. In total, roughly 24 hours worth of digging through chrome-stats.com unearthed more than 100 positive reviews on a network of patently fraudulent extensions.
Those reviews in turn lead to the relatively straightforward identification of:
-39 reviewers who were happy with extensions that spoofed major brands and requested financial data
-45 malicious extensions that collectively had close to 100,000 downloads
-25 developer accounts tied to multiple banned applications
The extensions spoofed a range of consumer brands, including Adobe, Amazon, Facebook, HBO, Microsoft, Roku and Verizon. Scouring the manifests for each of these other extensions in turn revealed that many of the same developers were tied to multiple apps being promoted by the same phony Google accounts.
Some of the fake extensions have only a handful of downloads, but most have hundreds or thousands. A fake Microsoft Teams extension attracted 16,200 downloads in the roughly two months it was available from the Google store. A counterfeit version of CapCut, a professional video editing software suite, claimed nearly 24,000 downloads over a similar time period.
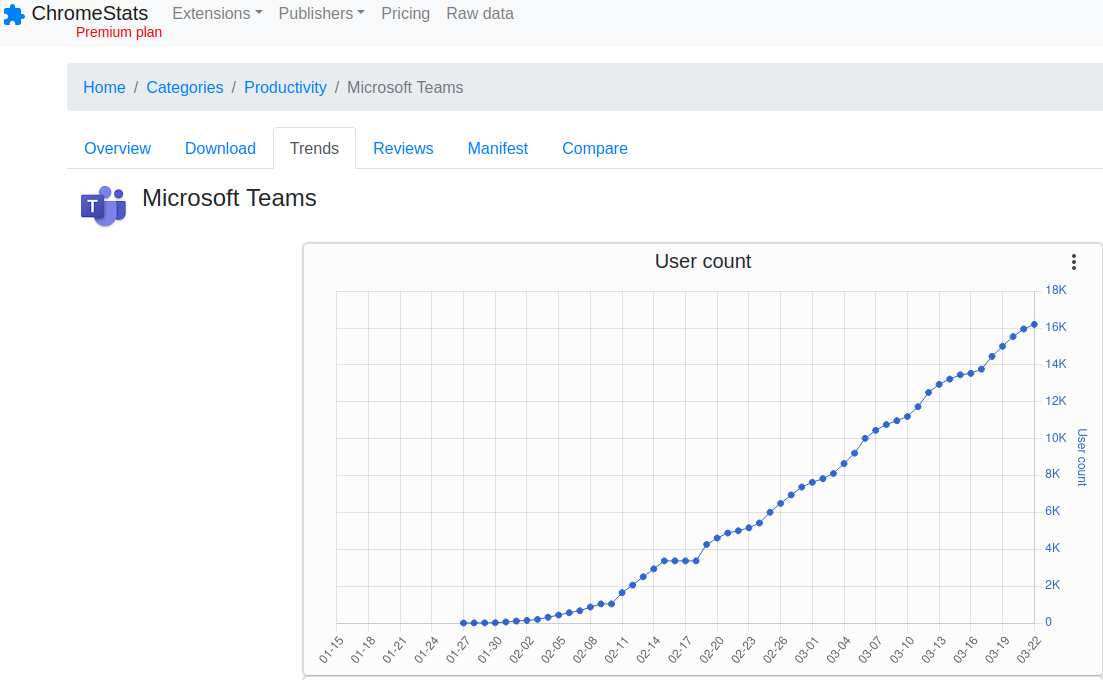
More than 16,000 people downloaded a fake Microsoft Teams browser extension over the roughly two months it was available for download from the Google Chrome store.
Unlike malicious browser extensions that can turn your PC into a botnet or harvest your cookies, none of the extensions examined here request any special permissions from users. Once installed, however, they invariably prompt the user to provide personal and financial data — all the while pretending to be associated with major brand names. Continue reading