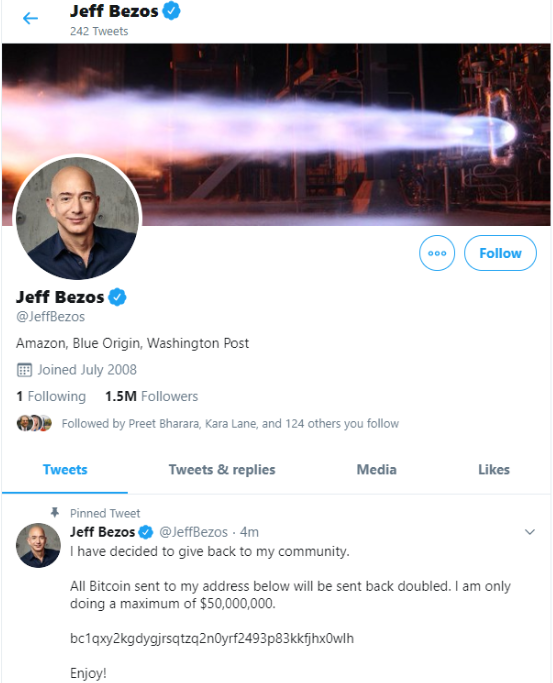
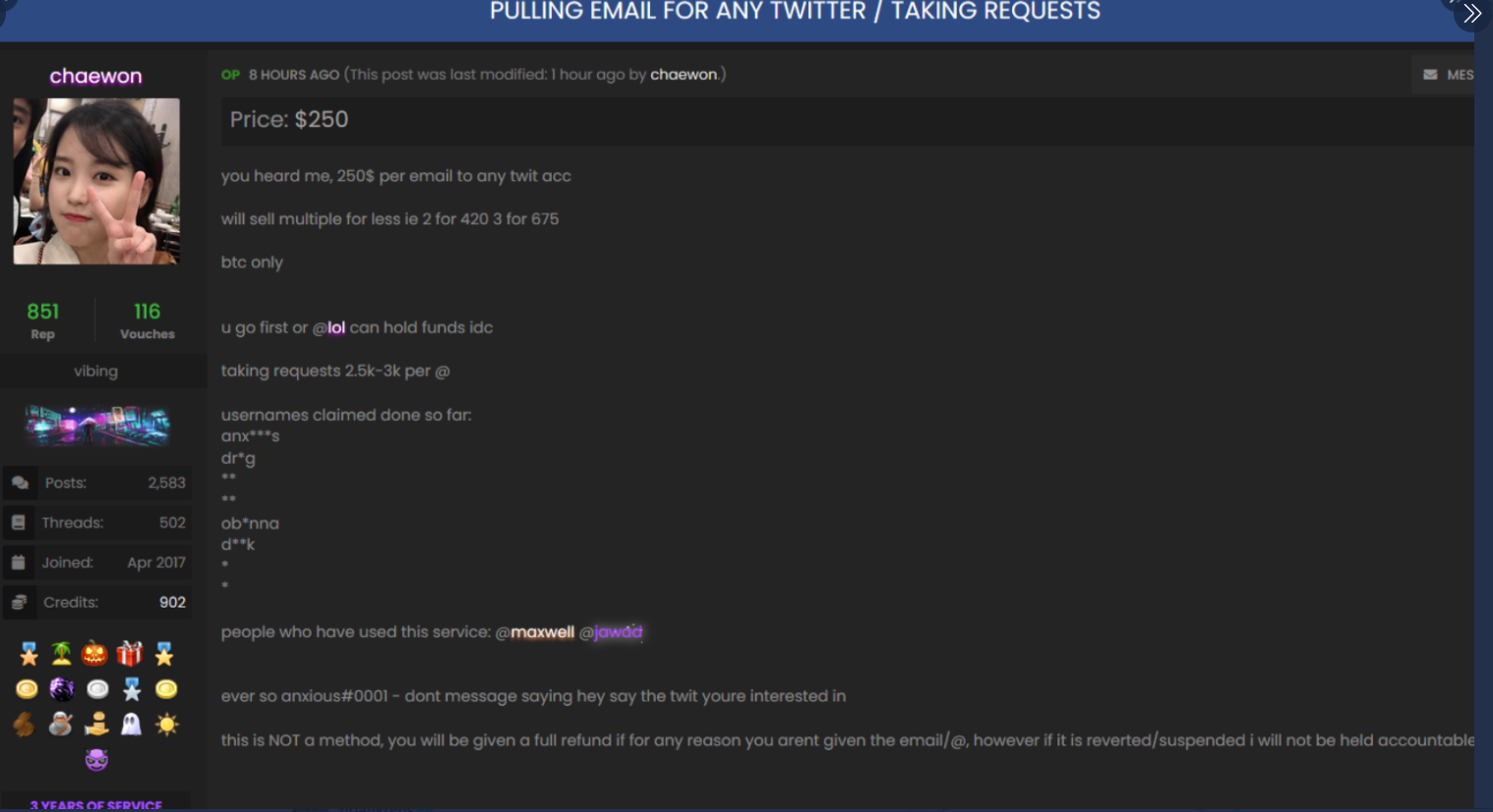
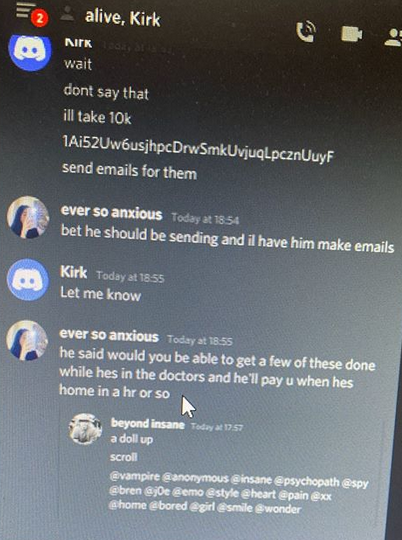
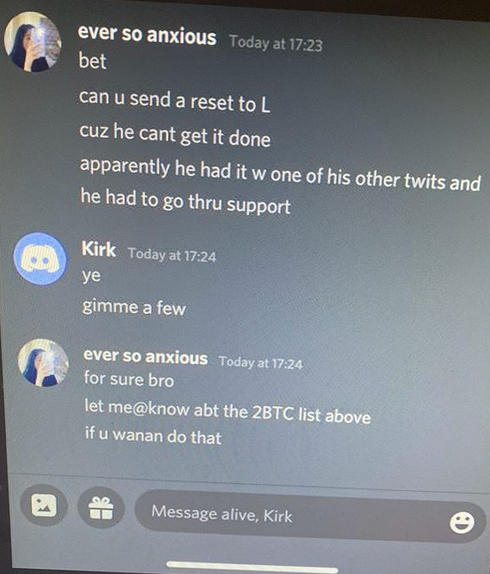
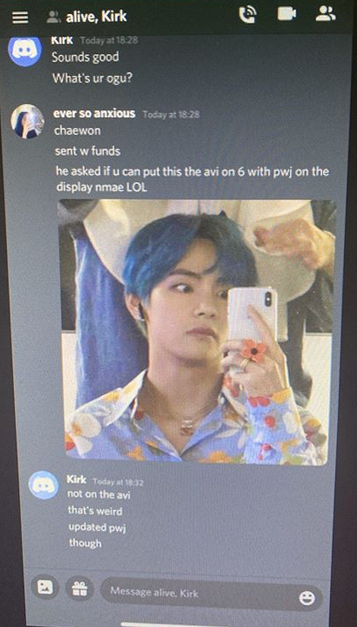
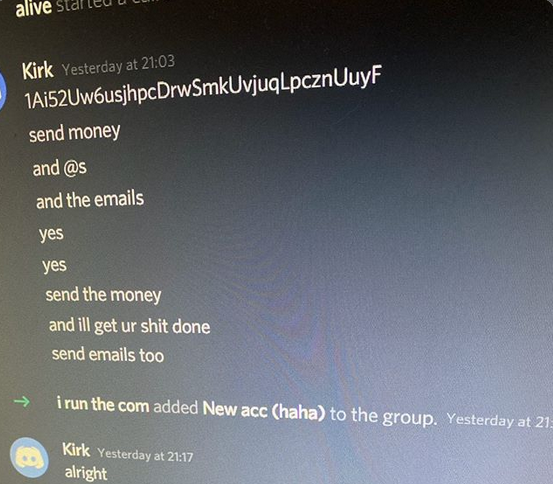
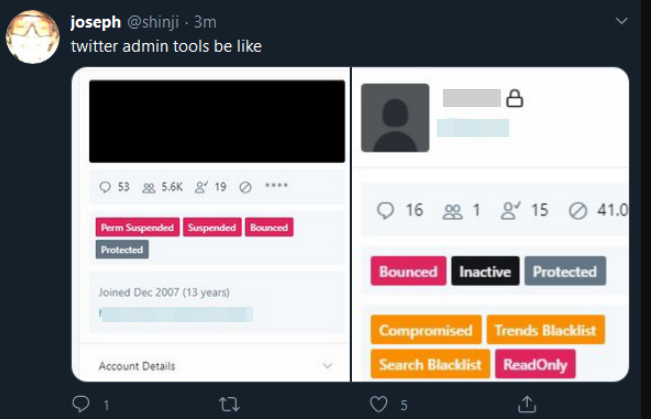
Perhaps fittingly, a Web-streamed court hearing for the 17-year-old alleged mastermind of the July 15 mass hack against Twitter was cut short this morning after mischief makers injected a pornographic video clip into the proceeding.

17-year-old Graham Clark of Tampa, Fla. was among those charged in the July 15 Twitter hack. Image: Hillsborough County Sheriff’s Office.
The incident occurred at a bond hearing held via the videoconferencing service Zoom by the Hillsborough County, Fla. criminal court in the case of Graham Clark. The 17-year-old from Tampa was arrested earlier this month on suspicion of social engineering his way into Twitter’s internal computer systems and tweeting out a bitcoin scam through the accounts of high-profile Twitter users.
Notice of the hearing was available via public records filed with the Florida state attorney’s office. The notice specified the Zoom meeting time and ID number, essentially allowing anyone to participate in the proceeding.
Even before the hearing officially began it was clear that the event would likely be “zoom bombed.” That’s because while participants were muted by default, they were free to unmute their microphones and transmit their own video streams to the channel.
Sure enough, less than a minute had passed before one attendee not party to the case interrupted a discussion between Clark’s attorney and the judge by streaming a live video of himself adjusting his face mask. Just a few minutes later, someone began interjecting loud music.
It became clear that presiding Judge Christopher C. Nash was personally in charge of administering the video hearing when, after roughly 15 seconds worth of random chatter interrupted the prosecution’s response, Nash told participants he was removing the troublemakers as quickly as he could.

Judge Nash, visibly annoyed immediately after one of the many disruptions to today’s hearing.
What transpired a minute later was almost inevitable given the permissive settings of this particular Zoom conference call: Someone streamed a graphic video clip from Pornhub for approximately 15 seconds before Judge Nash abruptly terminated the broadcast.
With the ongoing pestilence that is the COVID-19 pandemic, the nation’s state and federal courts have largely been forced to conduct proceedings remotely via videoconferencing services. While Zoom and others do offer settings that can prevent participants from injecting their own audio and video into the stream unless invited to do so, those settings evidently were not enabled in today’s meeting.
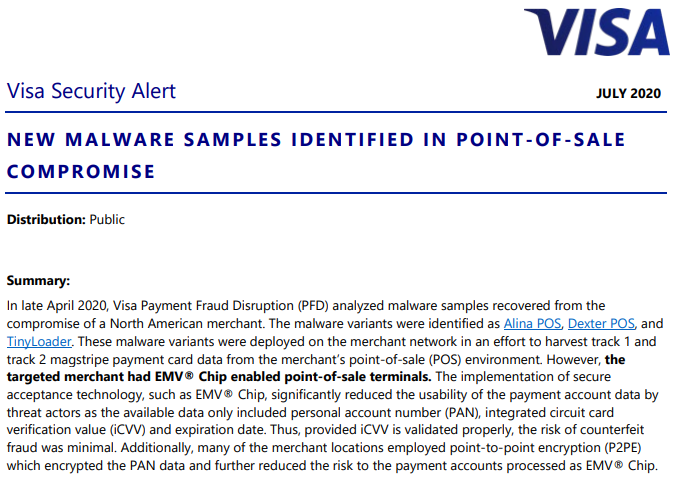
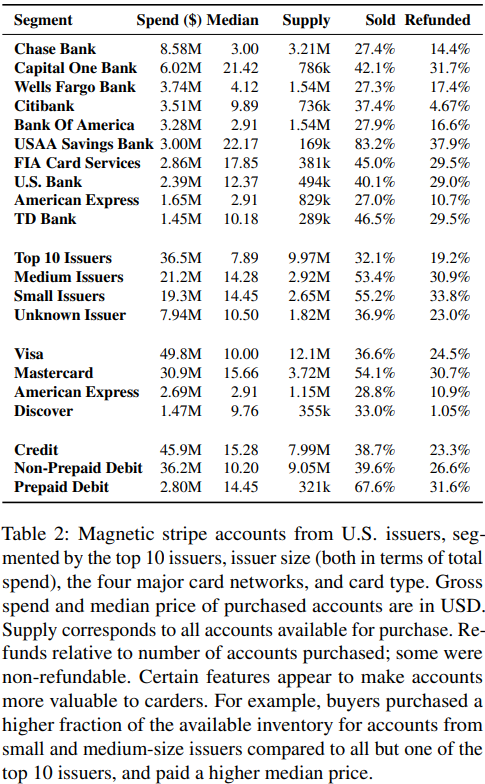
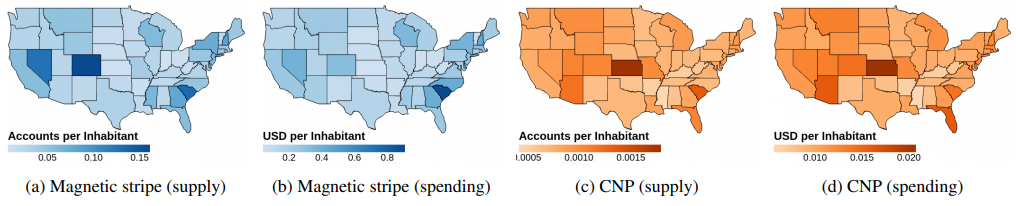
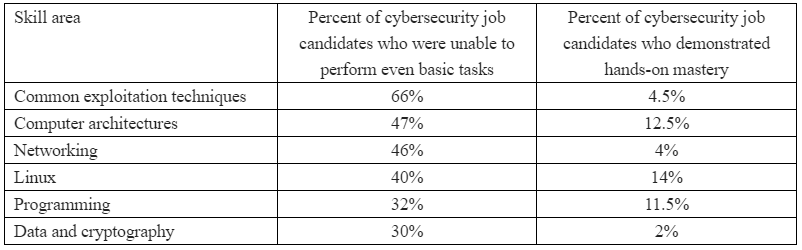
At issue before the court today was a defense motion to modify the amount of the defendant’s bond, which has been set at $750,000. The prosecution had argued that Clark should be required to show that any funds used toward securing that bond were gained lawfully, and were not merely the proceeds from his alleged participation in the Twitter bitcoin scam or some other form of cybercrime.

Florida State Attorney Andrew Warren’s reaction as a Pornhub clip began streaming to everyone in today’s Zoom proceeding.
Mr. Clark’s attorneys disagreed, and spent most of the uninterrupted time in today’s hearing explaining why their client could safely be released under a much smaller bond and close supervision restrictions.
On Sunday, The New York Times published an in-depth look into Clark’s wayward path from a small-time cheater and hustler in online games like Minecraft to big-boy schemes involving SIM swapping, a form of fraud that involves social engineering employees at mobile phone companies to gain control over a target’s phone number and any financial, email and social media accounts associated with that number.
According to The Times, Clark was suspected of being involved in a 2019 SIM swapping incident which led to the theft of 164 bitcoins from Gregg Bennett, a tech investor in the Seattle area. That theft would have been worth around $856,000 at the time; these days 164 bitcoins is worth approximately $1.8 million.
The Times said that soon after the theft, Bennett received an extortion note signed by Scrim, one of the hacker handles alleged to have been used by Clark. From that story:
“We just want the remainder of the funds in the Bittrex,” Scrim wrote, referring to the Bitcoin exchange from which the coins had been taken. “We are always one step ahead and this is your easiest option.”
In April, the Secret Service seized 100 Bitcoins from Mr. Clark, according to government forfeiture documents. A few weeks later, Mr. Bennett received a letter from the Secret Service saying they had recovered 100 of his Bitcoins, citing the same code that was assigned to the coins seized from Mr. Clark.
Florida prosecutor Darrell Dirks was in the middle of explaining to the judge that investigators are still in the process of discovering the extent of Clark’s alleged illegal hacking activities since the Secret Service returned the 100 bitcoin when the porn clip was injected into the Zoom conference.
Ultimately, Judge Nash decided to keep the bond amount as is, but to remove the condition that Clark prove the source of the funds.
Clark has been charged with 30 felony counts and is being tried as an adult. Federal prosecutors also have charged two other young men suspected of playing roles in the Twitter hack, including a 22-year-old from Orlando, Fla. and a 19-year-old from the United Kingdom.





 The leaked Blacklist customer database points to various companies you might expect to see using automated calling systems to generate business, including real estate and life insurance providers, credit repair companies and a long list of online advertising firms and individual digital marketing specialists.
The leaked Blacklist customer database points to various companies you might expect to see using automated calling systems to generate business, including real estate and life insurance providers, credit repair companies and a long list of online advertising firms and individual digital marketing specialists.