A 21-year-old Illinois man was sentenced last week to 13 months in prison for running multiple DDoS-for-hire services that launched millions of attacks over several years. This individual’s sentencing comes more than five years after KrebsOnSecurity interviewed both the defendant and his father and urged the latter to take a more active interest in his son’s online activities.
The jail time was handed down to Sergiy P. Usatyuk of Orland Park, Ill., who pleaded guilty in February to one count of conspiracy to cause damage to Internet-connected computers and owning, administering and supporting illegal “booter” or “stresser” services designed to knock Web sites offline, including exostress[.]in, quezstresser[.]com, betabooter[.]com, databooter[.]com, instabooter[.]com, polystress[.]com and zstress[.]net.
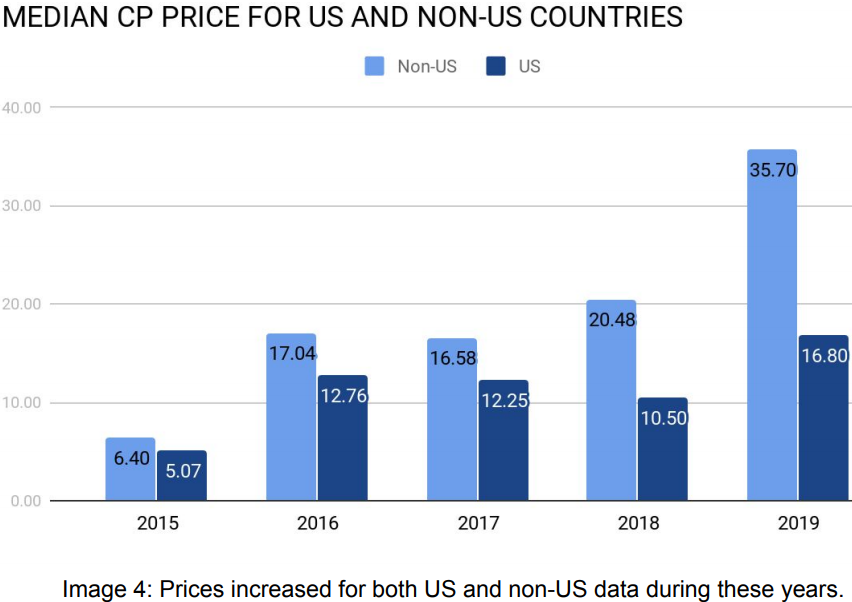
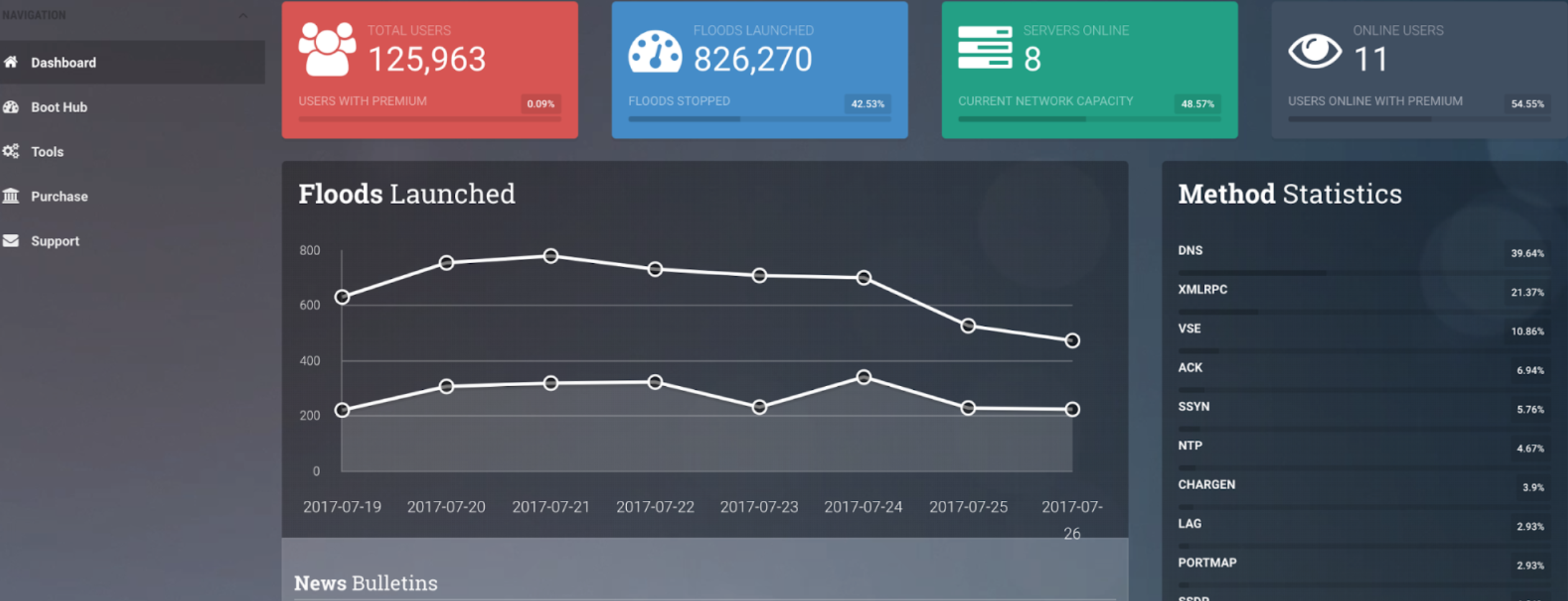
According to the U.S. Justice Department, in just the first 13 months of the 27-month long conspiracy, Usatyuk’s booter users ordered approximately 3,829,812 DDoS attacks. As of September 12, 2017, ExoStresser advertised on its website that this one booter service had launched 1,367,610 DDoS attacks, and caused targets to suffer 109,186.4 hours of network downtime (-4,549 days).
Usatyuk — operating under the hacker aliases “Andrew Quez” and “Brian Martinez,” among others — admitted developing, controlling and operating the aforementioned booter services from around August 2015 through November 2017. But Usatyuk’s involvement in the DDoS-for-hire space very much predates that period.
In February 2014, KrebsOnSecurity reached out to Usatyuk’s father Peter Usatyuk, an assistant professor at the University of Illinois at Chicago. I did so because a brief amount of sleuthing on Hackforums[.]net revealed that his then 15-year-old son Sergiy — who at the time went by the nicknames “Rasbora” and “Mr. Booter Master” — was heavily involved in helping to launch crippling DDoS attacks.
I phoned Usatyuk the elder because Sergiy’s alter egos had been posting evidence on Hackforums and elsewhere that he’d just hit KrebsOnSecurity.com with a 200 Gbps DDoS attack, which was then considered a fairly impressive DDoS assault.
“I am writing you after our phone conversation just to confirm that you may call evening time/weekend to talk to my son Sergio regarding to your reasons,” Peter Usatyuk wrote in an email to this author on Feb. 13, 2014. “I also have [a] major concern what my 15 yo son [is] doing. If you think that is any kind of illegal work, please, let me know.” Continue reading





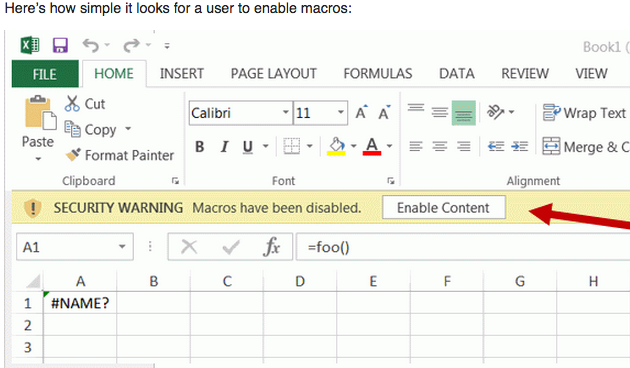
 More than a dozen of the flaws tackled in this month’s release are rated “critical,” meaning they involve weaknesses that could be exploited to install malware without any action on the part of the user, except for perhaps browsing to a hacked or malicious Web site or opening a booby-trapped file attachment.
More than a dozen of the flaws tackled in this month’s release are rated “critical,” meaning they involve weaknesses that could be exploited to install malware without any action on the part of the user, except for perhaps browsing to a hacked or malicious Web site or opening a booby-trapped file attachment.