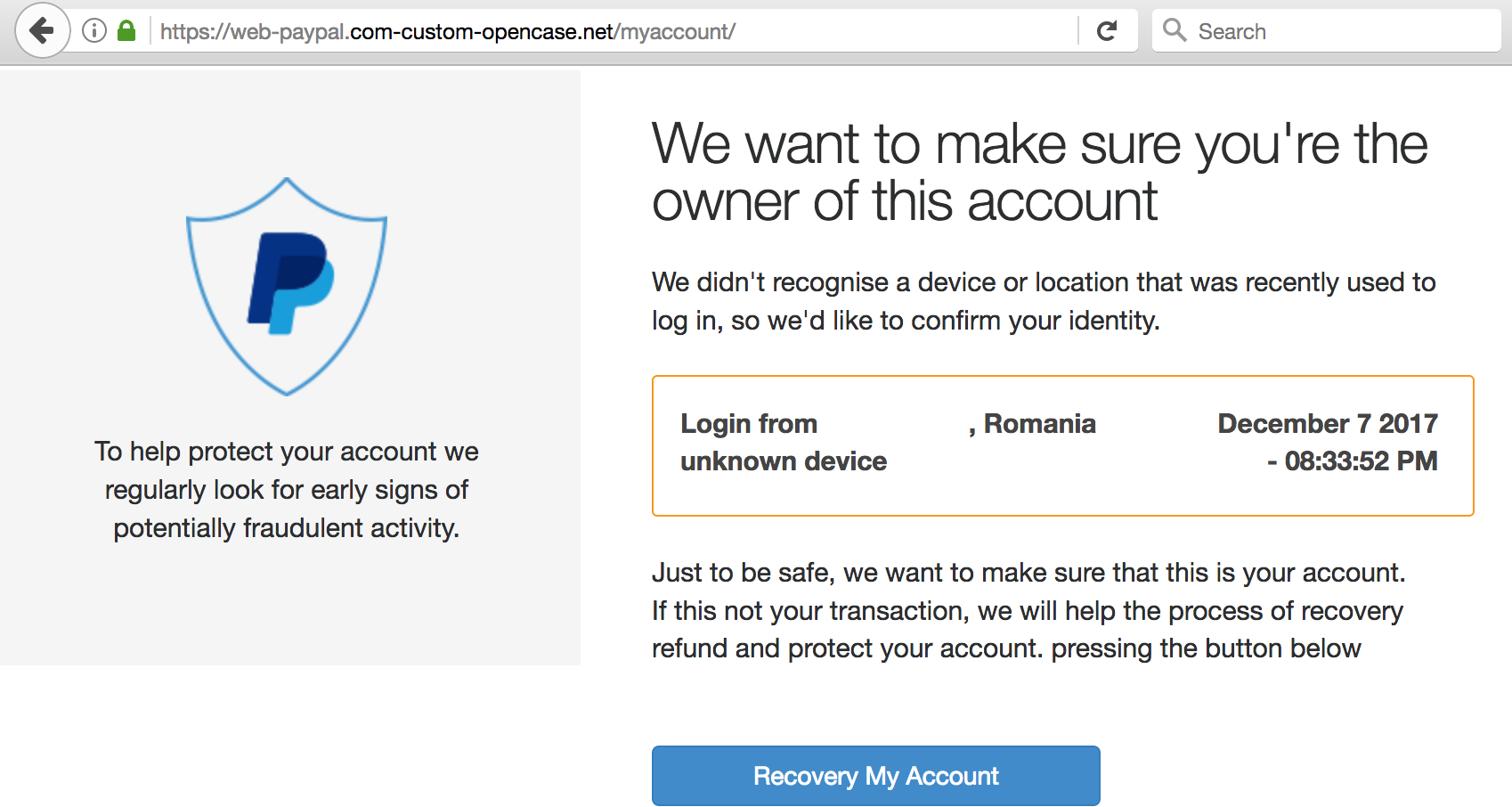
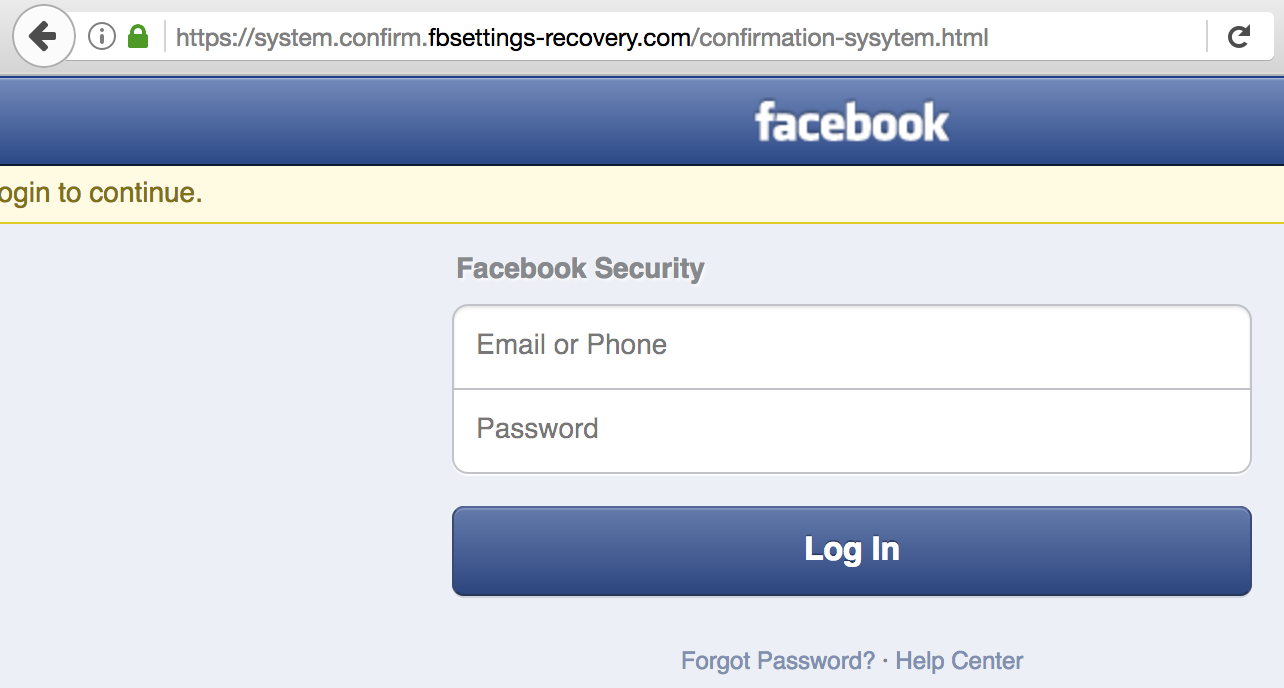
KrebsOnSecurity has sought to call attention to online services which expose sensitive consumer data if the user knows a handful of static details about a person that are broadly for sale in the cybercrime underground, such as name, date of birth, and Social Security Number. Perhaps the most eye-opening example of this is on display at fafsa.ed.gov, the Web site set up by the U.S. Department of Education for anyone interested in applying for federal student financial aid.
Update, Nov. 28, 12:34 p.m. ET: The Education Department says not all of the data elements mentioned below are accessible on a FAFSA applicant if someone merely knows the static details about that person. Read on for their response to this story.
Original story:
Short for the Free Application for Federal Student Aid, FAFSA is an extremely lengthy and detailed form required at all colleges that accept and award federal aid to students.
Visitors to the login page for FAFSA have two options: Enter either the student’s FSA ID and password, or choose “enter the student’s information.” Selecting the latter brings up a prompt to enter the student’s first and last name, followed by their date of birth and Social Security Number.
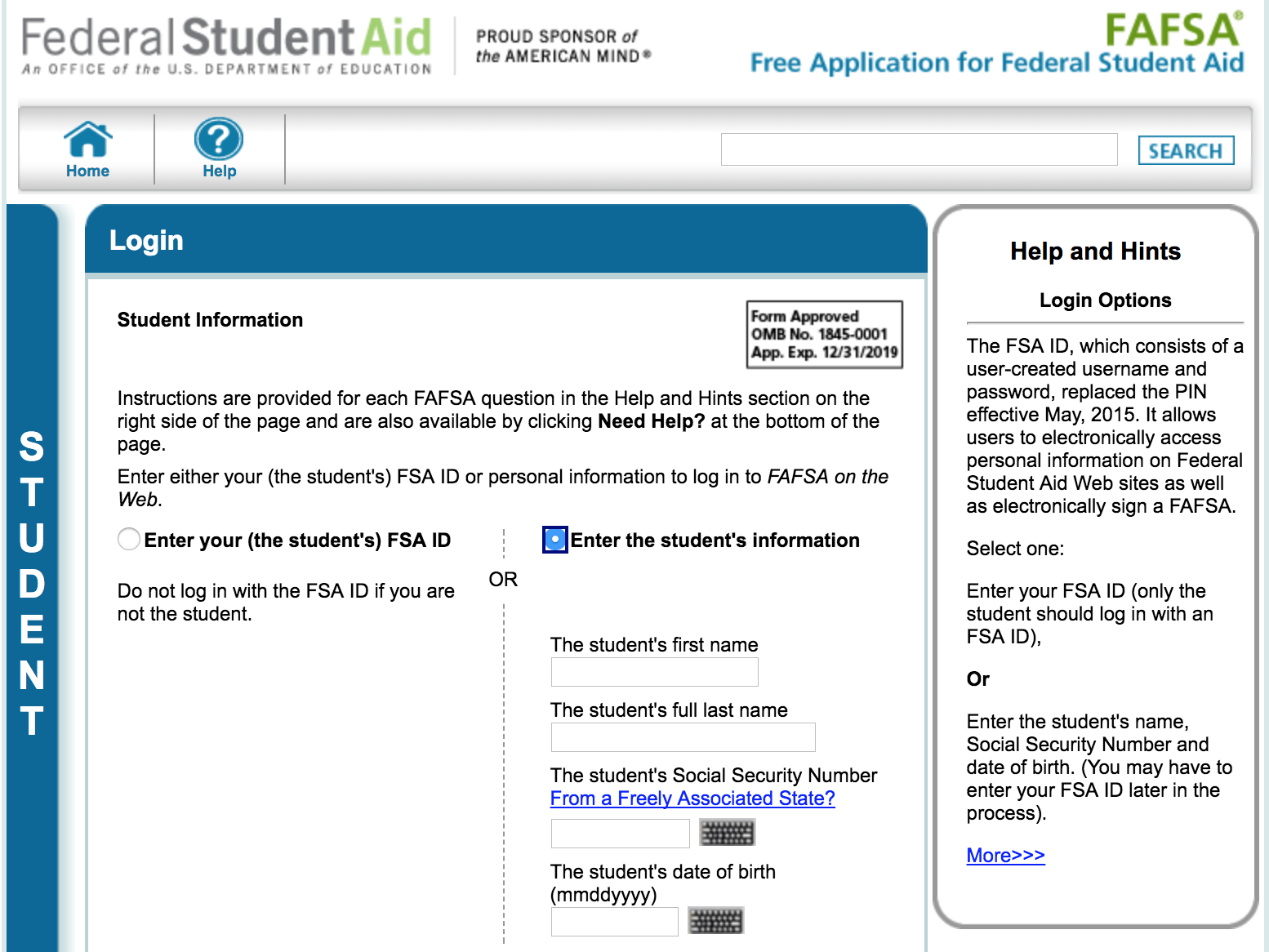
Anyone who successfully supplies that information on a student who has applied for financial aid through FAFSA then gets to see a virtual colonoscopy of personal information on that individual and their family’s finances — including almost 200 different data elements.
The information returned includes all of these data fields:
1. Student’s Last Name:
2. Student’s First Name:
3. Student’s Middle Initial:
4. Student’s Permanent Mailing Address:
5. Student’s Permanent City:
6. Student’s Permanent State:
7. Student’s Permanent ZIP Code:
8. Student’s Social Security Number:
9. Student’s Date of Birth:
10. Student’s Telephone Number:
11. Student’s Driver’s License Number:
12. Student’s Driver’s License State:
13. Student’s E-mail Address:
14. Student’s Citizenship Status:
15. Student’s Alien Registration Number:
16. Student’s Marital Status:
17. Student’s Marital Status Date:
18. Student’s State of Legal Residence:
19. Was Student a Legal Resident Before January 1, 2012?
20. Student’s Legal Residence Date:
21. Is the Student Male or Female?
22. Register Student With Selective Service System?
23. Drug Conviction Affecting Eligibility?
24. Parent 1 Educational Level:
25. Parent 2 Educational Level:
26. High School or Equivalent Completed?
27a. Student’s High School Name:
27b. Student’s High School City:
27c. Student’s High School State:
28. First Bachelor’s Degree before 2017-2018 School Year?
29. Student’s Grade Level in College in 2017-2018:
30. Type of Degree/Certificate:
31. Interested in Work-study?
32. Student Filed 2015 Income Tax Return?
33. Student’s Type of 2015 Tax Form Used:
34. Student’s 2015 Tax Return Filing Status:
35. Student Eligible to File a 1040A or 1040EZ?
36. Student’s 2015 Adjusted Gross Income:
37. Student’s 2015 U.S. Income Tax Paid:
38. Student’s 2015 Exemptions Claimed:
39. Student’s 2015 Income Earned from Work:
40. Spouse’s 2015 Income Earned from Work:
41. Student’s Total of Cash, Savings, and Checking Accounts:
42. Student’s Net Worth of Current Investments:
43. Student’s Net Worth of Businesses/Investment Farms:
44a. Student’s Education Credits:
44b. Student’s Child Support Paid:
44c. Student’s Taxable Earnings from Need-Based Employment Programs:
44d. Student’s College Grant and Scholarship Aid Reported in AGI:
44e. Student’s Taxable Combat Pay Reported in AGI:
44f. Student’s Cooperative Education Earnings:
45a. Student’s Payments to Tax-Deferred Pensions & Retirement Savings:
45b. Student’s Deductible Payments to IRA/Keogh/Other:
45c. Student’s Child Support Received:
45d. Student’s Tax Exempt Interest Income:
45e. Student’s Untaxed Portions of IRA Distributions:
45f. Student’s Untaxed Portions of Pensions:
45g. Student’s Housing, Food, & Living Allowances:
45h. Student’s Veterans Noneducation Benefits:
45i. Student’s Other Untaxed Income or Benefits:
45j. Money Received or Paid on Student’s Behalf:
46. Student Born Before January 1, 1994?
47. Is Student Married?
48. Working on Master’s or Doctorate in 2017-2018?
49. Is Student on Active Duty in U.S. Armed Forces?
50. Is Student a Veteran?
51. Does Student Have Children He/She Supports?
52. Does Student Have Dependents Other than Children/Spouse?
53. Parents Deceased?/Student Ward of Court?/In Foster Care?
54. Is or Was Student an Emancipated Minor?
55. Is or Was Student in Legal Guardianship?
56. Is Student an Unaccompanied Homeless Youth as Determined by High School/Homeless Liaison?
57. Is Student an Unaccompanied Homeless Youth as Determined by HUD?
58. Is Student an Unaccompanied Homeless Youth as Determined by Director of Homeless Youth Center?
59. Parents’ Marital Status:
60. Parents’ Marital Status Date:
61. Parent 1 (Father’s/Mother’s/Stepparent’s) Social Security Number:
62. Parent 1 (Father’s/Mother’s/Stepparent’s) Last Name:
63. Parent 1 (Father’s/Mother’s/Stepparent’s) First Name Initial:
64. Parent 1 (Father’s/Mother’s/Stepparent’s) Date of Birth:
65. Parent 2 (Father’s/Mother’s/Stepparent’s) Social Security Number:
66. Parent 2 (Father’s/Mother’s/Stepparent’s) Last Name:
67. Parent 2 (Father’s/Mother’s/Stepparent’s) First Name Initial:
68. Parent 2 (Father’s/Mother’s/Stepparent’s) Date of Birth:
69. Parents’ E-mail Address:
70. Parents’ State of Legal Residence:
71. Were Parents Legal Residents Before January 1, 2012?
72. Parents’ Legal Residence Date:
73. Parents’ Number of Family Members in 2017-2018:
74. Parents’ Number in College in 2017-2018 (Parents Excluded):
75. Parents Received Medicaid or Supplemental Security Income?
76. Parents Received SNAP?
77. Parents Received Free/Reduced Price Lunch?
78. Parents Received TANF?
79. Parents Received WIC?
80. Parents Filed 2015 Income Tax Return?
81. Parents’ Type of 2015 Tax Form Used:
82. Parents’ 2015 Tax Return Filing Status:
83. Parents Eligible to File a 1040A or 1040EZ?
84. Is Parent a Dislocated Worker?
85. Parents’ 2015 Adjusted Gross Income:
86. Parents’ 2015 U.S. Income Tax Paid:
87. Parents’ 2015 Exemptions Claimed:
88. Parent 1 (Father’s/Mother’s/Stepparent’s) 2015 Income Earned from Work:
89. Parent 2 (Father’s/Mother’s/Stepparent’s) 2015 Income Earned from Work:
90. Parents’ Total of Cash, Savings, and Checking Accounts:
91. Parents’ Net Worth of Current Investments:
92. Parents’ Net Worth of Businesses/Investment Farms:
93a. Parents’ Education Credits:
93b. Parents’ Child Support Paid:
93c. Parents’ Taxable Earnings from Need-Based Employment Programs:
93d. Parents’ College Grant and Scholarship Aid Reported in AGI:
93e. Parents’ Taxable Combat Pay Reported in AGI:
93f. Parents’ Cooperative Education Earnings:
94a. Parents’ Payments to Tax-Deferred Pensions & Retirement Savings:
94b. Parents’ Deductible Payments to IRA/Keogh/Other:
94c. Parents’ Child Support Received:
94d. Parents’ Tax Exempt Interest Income:
94e. Parents’ Untaxed Portions of IRA Distributions:
94f. Parents’ Untaxed Portions of Pensions:
94g. Parents’ Housing, Food, & Living Allowances:
94h. Parents’ Veterans Noneducation Benefits:
94i. Parents’ Other Untaxed Income or Benefits:
95. Student’s Number of Family Members in 2017-2018:
96. Student’s Number in College in 2017-2018:
97. Student Received Medicaid or Supplemental Security Income?
98. Student Received SNAP?
99. Student Received Free/Reduced Price Lunch?
100. Student Received TANF?
101. Student Received WIC?
102. Is Student or Spouse a Dislocated Worker?
103a. First Federal School Code:
103b. First Housing Plans:
103c. Second Federal School Code:
103d. Second Housing Plans:
103e. Third Federal School Code:
103f. Third Housing Plans:
103g. Fourth Federal School Code:
103h. Fourth Housing Plans:
103i. Fifth Federal School Code:
103j. Fifth Housing Plans:
103k. Sixth Federal School Code:
103l. Sixth Housing Plans:
103m. Seventh Federal School Code:
103n. Seventh Housing Plans:
103o. Eighth Federal School Code:
103p. Eighth Housing Plans:
103q. Ninth Federal School Code:
103r. Ninth Housing Plans:
103s. Tenth Federal School Code:
103t. Tenth Housing Plans:
104. Date Completed:
105. Signed By:
106. Preparer’s Social Security Number:
107. Preparer’s Employer Identification Number (EIN):
108. Preparer’s Signature:
According to the Education Department, nearly 20 million students filled out this form in the 2015/2016 application cycle.
Update: The process described above was based on a demonstration this author saw while sharing a screen with a KrebsOnSecurity reader who had a family member apply for aid through FAFSA. But an Education Department spokesperson took strong exception to my experience, saying that while someone armed with an applicant’s SSN and date of birth would be able to view some of the less sensitive data elements related to an application that has already been submitted and processed, seeing the more sensitive data requires and additional authentication step.
The spokesperson said the data is displayed across several pages that require manual advancement, and that before the pages with financial data are shown the visitor is prompted to supply a username and password that all users are required to create when they start the application process. The agency said that without those credentials, the system should not display the rest of the data.
In cases where a student has saved but not completed an application, the spokesperson said, the applicant is prompted to create a “save key,” or temporary password that needs to be supplied before the financial data is displayed.
Continue reading →
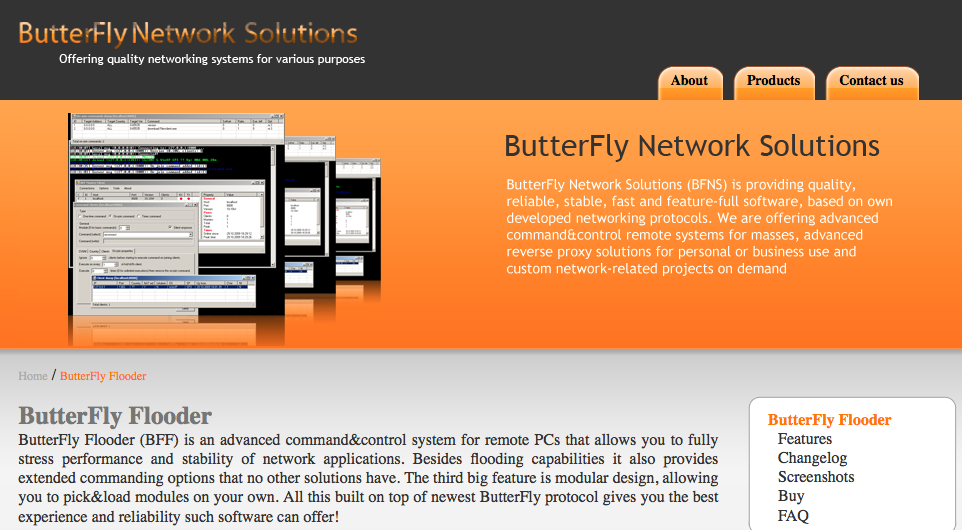
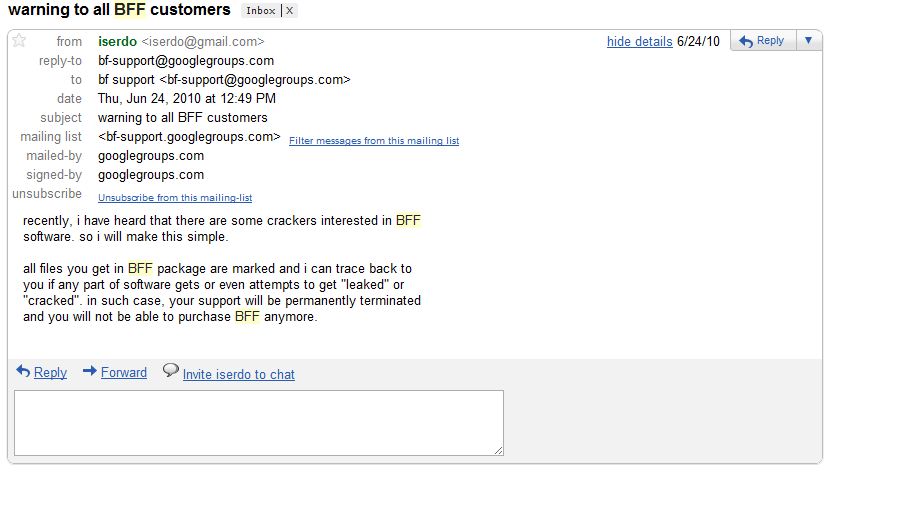
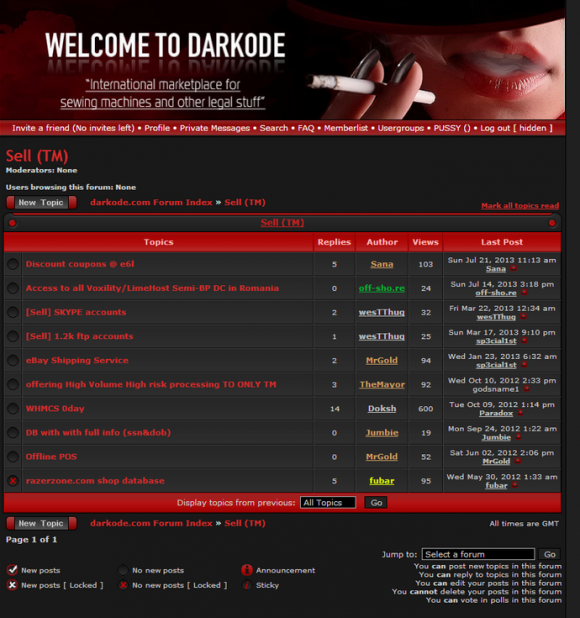




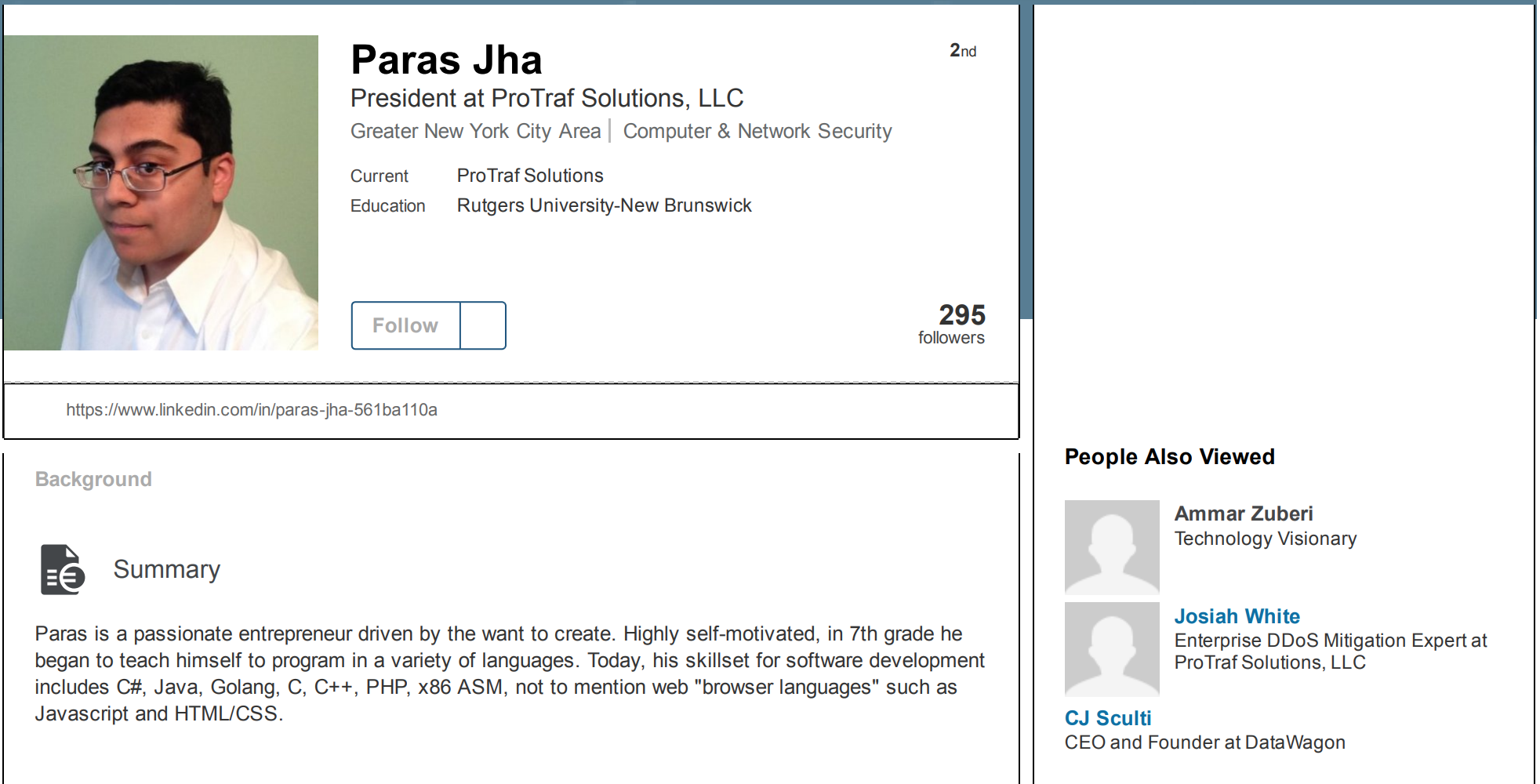
 The December patch batch addresses more than 30 vulnerabilities in Windows and related software. As per usual, a huge chunk of the updates from Microsoft tackle security problems with the Web browsers built into Windows.
The December patch batch addresses more than 30 vulnerabilities in Windows and related software. As per usual, a huge chunk of the updates from Microsoft tackle security problems with the Web browsers built into Windows.