A large number of banks, credit unions and other financial institutions just pushed customers onto new e-banking platforms that asked them to reset their account passwords by entering a username plus some other static identifier — such as the first six digits of their Social Security number (SSN), or a mix of partial SSN, date of birth and surname. Here’s a closer look at what may be going on (spoiler: small, regional banks and credit unions have grown far too reliant on the whims of just a few major online banking platform providers).

You might think it odd that any self-respecting financial institution would seek to authenticate customers via static data like partial SSN for passwords, and you’d be completely justified for thinking that, too. Nobody has any business using these static identifiers for authentication because they are for sale on most Americans quite cheaply in the cybercrime underground. The Equifax breach might have “refreshed” some of those data stores for identity thieves, but most U.S. adults have had their static details (DOB/SSN/MMN, address, previous address, etc) on sale for years now.
On Feb. 16, KrebsOnSecurity reader Brent Hoeft shared a copy of an email he’d just received from his financial institution Associated Bank, which at $30+ billion in assets happens to be Wisconsin’s largest by asset size.
The notice advised:
“Please read and save this information (including the password below) to prepare for your online and mobile banking upgrade.
Our refreshed online and mobile banking experience is officially launching on Monday, February 26, 2018.
We’re excited to share it with you, and want you to be aware of some important details about the transition.
TEMPORARY PASSWORD
Use this temporary password the first time you sign in after the upgrade. Your temporary password is the first four letters of your last name plus the last four digits of your Social Security Number.
XXXX#### [redacted by me but included in the email]
Note: your password is all lowercase without spaces.
Once the upgrade is complete, you will need your temporary password to begin the re-enrollment process.
• Beginning Monday, February 26, you will need to sign in using your existing user ID and the temporary password included above in this email. Please note that you are only required to reenroll in online or mobile banking but can access both using the same user ID and password.
• Once you sign in, you will be prompted to create a new password and establish other security features. Your user ID will remain the same.”
Hoeft said Associated Bank seems to treat the customer username as a secret, something to be protected along with the password.
“I contacted Associated’s customer service via email and received a far less satisfying explanation that the user name is required for re-activation and, that since [the username] was not provided in the email, the process they are using is in fact secure,” Hoeft said.
After speaking with Hoeft, I tweeted about whether to name and shame the bank before it was too late, or perhaps to try and talk some sense into them privately. Most readers advised that calling attention to the problem before the transition could cause more harm than good, and that at least until after Feb. 26 contacting some of the banks privately was the best idea (which is what I did).
Associated Bank wouldn’t say who their new consumer online banking platform provider was, but they did say it was one of the big ones. I took that to mean either FIS, Fiserv or Jack Henry, which collectively control approximately 70 percent of the market for bank core processors (according to FedFIS.com, Fiserv is by far the largest).
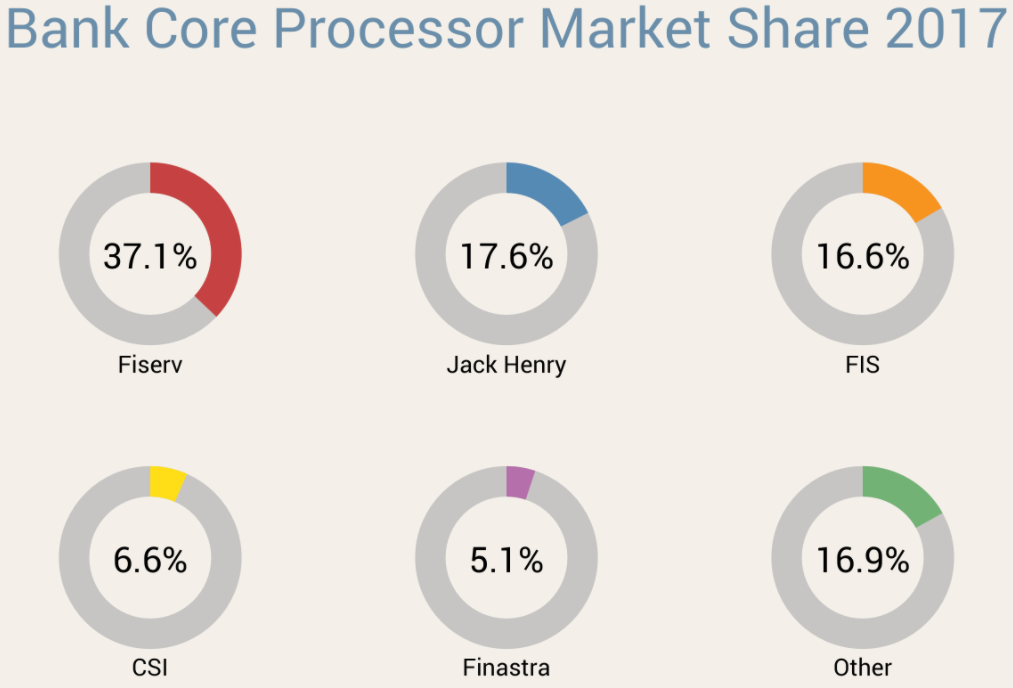
Image: Fedfis.com
The bank’s chief information security officer Joe Smits said Associated’s new consumer online banking platform provider required that new and existing customers log in with a username and a temporary password — which was described as choice among secondary, static data elements about customers — such as the first six digits of the customer’s SSN or date of birth.
Smits added that the bank originally started emailing customers the instructions for figuring out their temporary passwords, but then decided US mail would be a safer option and sent the rest out that way. He said only about 15 percent of Associated Bank customers (~50,000) received instructions about their temporary passwords through email.
I followed up with Hoeft to find out how his online banking upgrade went at Associated Bank. He told me that upon visiting the site, it asked for his username and the temporary password (the first four letters of his last name and the last four digits of his SSN).
“After entering that I was told to re-enter my temporary password and then create a new password,” Hoeft said. “I then was asked to select 5 security questions and provide answers. Next I was asked for a verification phone number. Upon entering that I received a text message with a 4 digit verification code. After entering the code it asked me to finish my profile information including name, email and daytime phone. After that it took me right into my online banking account.”
Hoeft said it seems like the “verification” step that was supposed to create an extra security check didn’t really add any security at all.
“If someone were able to get in with the temporary password, they would be able to create a new password, fill out all the security code information, and then provide their phone number to receive the verification code,” Hoeft said. “Armed with the verification code they then would be able to get right into my online banking account.”
OTHER BANKS
A simple search online revealed Associated Bank wasn’t alone: Multiple institutions were moving to a new online banking platform all on the same day: Feb. 26, 2018.
My Credit Union also moved to a new online banking service in February, posting a notice stating that all customers will need to log in with their current username and the last four of their SSN as a temporary password.
Customers Bank, a $10 billion bank with nearly two dozen branches between Boston and Philadelphia, also told customers that starting Feb. 26 they would need to use a temporary password — the last six digits of their Social Security number — to re-enroll in online banking. Here’s part of their advice, which was published in a PDF on the bank’s site:
• You may notice a new co-branded logo for Customers Bank and BankMobile (Division Customers Bank).
• Your existing user name for Online Banking will remain the same within the new system; however, it must be entered as all lowercase letters.
• The first time you log into the new Online Banking system, your temporary password is the last 6-digits of your social security number. Your temporary
password will expire on Friday, April 20, 2018. Please be sure to log in prior to that date.
• Online Banking includes multi-factor authentication which will need to be reestablished as part of the initial sign in to the system.
• Your username and password credentials for Online Banking will be the same for Mobile Banking. Note: Before accessing the new Mobile Banking services,
you must first login to our enhanced Online Banking system to change your password.
• You will also need to enroll your mobile device, either through Online Banking by visiting the Mobile Banking Center option, or directly on the device through the
app. Both options will require additional authentication.
Columbia Bank, which has 140 branches in Washington, Oregon and Idaho, also switched gears on Feb. 26, but used a more sensible approach: Sending customers a new user ID, organization ID and temporary password in two separate mailings.
ANALYSIS
My tweet about whether to name Associated Bank attracted the attention of at least two banking industry security regulators, each of whom spoke with KrebsOnSecurity on condition of not being identified by name or regulatory agency.
Both said their agencies would be using the above examples in briefings with member institutions as instructional on how not to do online banking securely. Both also said small to mid-sized banks are massively beholden to their platform providers, and many banks simply accept the defaults instead of pushing for stronger alternatives.
“I have a lot of communications directly with the chief information security officers, chief security officers, and chief information officers in many institutions,” one regulator said. “Many of them have massively dumbed down their password requirements. A lot of smaller institutions often don’t understand the risk involved in online banking, which is why they try to outsource the whole thing to someone else. But they can’t outsource accountability.”
One of the regulators I spoke with suggested that all of the banks they’d seen transitioning to a new online banking platform on Feb. 26 were customers of Fiserv — the nation’s largest online banking platform provider.
Fiserv did not respond to specific questions for this story, saying only in a written statement that: “Fiserv regularly partners with financial institutions to provide capabilities that help mitigate and manage risk, enhance the customer experience, and allow banks to remain competitive. A variety of methodologies are used by institutions to enroll and authenticate new users onto online banking platforms, and password authentication is one of multiple layers of security used to protect customers.”
Both banking industry regulators I spoke with said a basic problem is that many smaller institutions unfortunately still treat usernames as secret codes. I have railed against this practice for years, but far too many banks treat customer usernames as part of their security, even though most customers pick something very close to the first part of their email address (before the “@” sign). I’ve even skewered some of the airline industry giants for doing the same (United does this with its super-secret frequent flyer account number).
“I think this will be an opportunity for us to coach them on that,” one banking regulator said. “This process has to involve random password generation and that needs to be standard operating procedure. If you can shortcut security just by supplying static data like SSN, it’s all screwed. Some of these organizations have had such poor control structure for so long they don’t even understand how bad it is.”
The other regulator said another challenge is how long banks should wait before disabling accounts if consumers don’t log in to the new online banking system.
“What they’re going to do is set up all these users on this brand new system and give them default passwords,” the regulator said. “Some individuals will log into their bank account every day, others once a month and sometimes quite randomly. So, how are they going to control that window of opportunity? At some point, maybe after a couple of weeks, they need to just disable those other accounts and have people start from scratch.”
The first regulator said it appears many banks (and their platform providers) are singularly focused on making these transitions as seamless and painless as possible for the financial institution and its customers.
“I think they’re looking at making it easier for their customers and lessening the fallout as they get fewer angry and frustrated calls,” the regulator said. “That’s their incentive more than anything else.”
WHAT CAN YOU DO?
While it may appear that banks are more afraid of calls from their customers than of fallout from identity thieves and hackers, remember that you the consumer can shop with your wallet, and should move your funds to another bank if you’re unhappy with the security practices of your current institution.
Also, don’t re-use passwords. In fact, wherever possible don’t use passwords at all. Instead, choose passphrases over passwords (remember, length is key). Unfortunately, passphrases may not be possible because some banks have chosen to truncate passwords after a certain number of characters, and to disallow special symbols.
If you’re the kind of person who likes to use the same password across multiple sites, then a password manager is definitely for you. That’s because password managers pick strong, long and secure passwords for you and the only thing you have to remember is a single master password.
Please consider any two-step or two-factor authentication options your financial institution may offer, and be sure to take full advantage of that when it’s available. Also, ask your bank to require a unique verbal password before discussing any of your account details over the phone; this prevents someone from calling in to your bank and convincing a customer service rep that he’s you just because he can regurgitate your static personal details.
Finally, take steps to prevent your security from being backdoored by your mobile provider: Check out last week’s tips on blocking mobile number port-out scams, which thieves sometimes use in cashing out hacked bank accounts.




I found this comment funny: “Also, ask your bank to require a unique verbal password before discussing any of your account details over the phone”
Capitol One just sent me a letter saying that effective in March, they were removing this option.
Are retirement account providers in a similar boat (i.e., Fidelity, Vanguard, Schwab, etc.)?
Losing funds from a bank account because of these practices would be very, very bad, but losing funds from a retirement account would be absolutely catastrophic for most folks.
Hey Brian
Your homepage is not reachable….too many redirects.
Those stories as direct URL from your twitter work just fine.
Cheers oliver
Are there any banks using the YubiKey? YubiKey is inexpensive especially in quantity and it is easy to use. Although there is a problem with Chrome (no suprise there) Google should have a fix shortly, so they say.
HSBC will give you a hardware token. If you do get the hardware token, you do not need a password to login, only the token. The token is like the old RSA ones from way back, it has an LCD display, you put in your pin code and it returns a number that you physically type into the web or mobile login screens.
Not a yubikey, but WAY better than most banks. You would have to physically steal my hardware device AND know my 4 digit pin.
… or just beat you over the head until you give up the device and your pin.
Yeah, I’ve been alive for 50-odd years and never had my home broken into nor been mugged. Time to stop living a life of fear and start worrying about threats that actually have a realistic chance of occurring to you, like identity theft and fraud committed in your name.
These tokens are better than static passwords, but you should know they are not designed to offer protection against man in the middle type attacks:
https://en.wikipedia.org/wiki/RSA_SecurID
If Google, Dropbox, Facebook and others can implement FIDO (Fast Identity Online) so their customers can use YubiKey or Fetian keys, why can’t banks and other financial institutions?
The FIDO Alliance has great documentation on how FIDO works and even source code so it can be implemented fairly easily.
Banks really need to implement FIDO 2FA if they are really serious about security.
The fact that they have option for 2FA doesn’t mean anything w.r.t. account security.
For example, I’m using Verisign softtoken with Fidelity. When I switched phone and needed to change to new token, I did it over a phone and their authentication questions were ridiculous.
A bit social engineering and your 2FA is easily removed from account.
Vanguard can use a Yubikey.
They also use an SMS. I successfully used a Google Voice number (not used anywhere else) to receive the SMS from Vanguard.
I like that they use a Yubikey, but because of the SS7 vulnerability, I wish they would deprecate the SMS and use a Authy/GoogleAuthenticator time-based-pseudo-random-number second factor authentication.
-T
Small to mid-sized banks ARE massively beholden to the processors to provide online banking. But the statement “A lot of smaller institutions often don’t understand the risk involved in online banking, which is why they try to outsource the whole thing to someone else. But they can’t outsource accountability.” is ridiculous. We understand the risk more than anyone. We outsource because we do not have the ability and frankly would have no business attempting to create our own online banking system. We face constant frustration as we try to get those processors to improve their authentication methods.
I wonder if you can file a complaint about this with your local bank regulator? Does this fit the criteria for e.g. a complaint to http://www.dbo.ca.gov/Consumers/consumer_services.asp
My takeaway from this is one should choose usernames that are very hard to guess. In this case, the username was more important to maintaining security( if you can call it that ) then the joke of a password. In effect, the the username WAS the password.
As for voting with ones feet , I don’t see what good that would do. Without inside information, how does anyone really know how good any given institutions security is, it’s a black hole. We only know after the fact in the case of the really bad actors(Equifax, et al).
I know for awhile my bank (PNC) issued you a default username when you signed up for online banking and it was your full SSN. In fairness, this was over a decade ago and I was able to change it after awhile. Now, new users get to pick their username but there is password restrictions so no passphrases.
My bank used to offer a normal username & password but apparently someone held one too many focus groups because they expanded all accounts to accept multiple forms of usernames, like credit card numbers, bank account numbers, SSN, the trusty old username, and hell if I know what else (probably including email address because everyone loves using an email address as account names now). So now all I’ve got is the longest string of gobbledigook characters they’ll let me set protecting my account, because the username field is worthless given all the easily uncovered data they accept.
Some financial institutions are friendlier to password managers than others. Many don’t allow drag and drop to the username field or password field. Some actively interfere with pasting in a username by having “Username” gray-texted into the input box.
Also, some don’t play well with at least older DVD versions of puppy linux.
Re: “… Some financial institutions are friendlier to password managers than others … Some actively interfere with pasting … ”
A VERY GOOD point
This is one of my bigger security-related gripes too.
Krebs, you should now call out IHG’s rewards website (https://www.ihg.com/rewardsclub/us/en/sign-in/?fwdest=/rewardsclub/us/en/account-mgmt/home) which asks only for email as username, 4 digit PIN, and last name to get in. Such lax security and I’m sure someone will figure out to exploit this and redeem everyone’s points for gift cards :). I’ve notified them and they’ve failed to do anything, even after being breached with malware on their systems. You’d think they’d learn!!
Re: “… Also, don’t re-use passwords … ”
I’d go one further …
… DON’T REUSE USER NAMES.
Moreso than the banks, blame the cores and online banking vendors. Most banks don’t develop their own online banking platforms, it’s simply from a vendor. And oftentimes, the core can pretty much dictate that you use their platform. So yes, while they are ultimately responsible, they’re also at the mercy of crappy software they are forced to use.
And before anyone says, ‘well, they should just switch cores’ – LOLOL. Every process a bank has, all of their training, different services and options, all are tied to the core, which are all very different in how they do things. It’s like swapping out all of your Windows users to Linux, overnight. Sure it will eventually work, but for an industry that is very sensitive to reputation damage, it would be beyond awful.
https://www.xudongz.com/blog/2017/idn-phishing/
Thanks for plagurisinf my aticikamnckds
My credit union did the exact same thing – likely beholden to the large service provider handling transactions. It is a joke that we allow financial institutions to rely on a simple username and password – no 2-factor which has been around for decades….let alone email users the temporary password scheme and some details about the platform upgrade. Continually dismayed that our info security/protection laws and regulations for banks are so weak.
My 2 cents — In general, only the top 20 banks develop and run their own on-line banking platforms. They are generally security-forward and careful to build secure solutions.
The rest of the Banks and Credit Unions (14,000+) are beholden to the giants (Fiserv, FIS, JH, Q2). Only the regulators can force the necessary change to the software platforms to keep them secure. No single Bank or CU has enough voice to get it done.
Internally, customer service fights against strong security because it is too challenging for many customers. Complex passwords, MFA, following detailed instructions, etc., is too much for many customers (especially for older customers). But these same customers have plenty of time and are happy to tie-up call centers with 30 minute + service calls.
Ultimately, strategies like Wells Fargo’s, where step-up authentication is required for higher risk transactions (like online wires) makes the most sense to balance security with usability.
To confirm Jon’s point as someone who works in the Financial Services Industry, the vast majority of institutions do not have the resources to build out own Internet Banking applications. However, that being said, we do have the responsibility to ensure they are secure. The standard for security and what regulators look at is based on the following FFIEC guidance:
https://www.fdic.gov/news/news/financial/2011/fil11050.html
If you read it, you will find that multi-factor authentication and layered security controls are now required for all online banking environments at all financial institutions. There is clearly room for interpretation as to what that means but the expectation is there and this is what regulators should be looking for.
If your financial institution does not use multi-factor authentication that meets the guidelines then they are not compliant with the regulation. All of the major online banking service providers support these requirements at this point so there is really no excuse not to have them implemented. If they are not implemented, it is at the direction of the financial institution, not the service provider.
To address the other comments about using tokens and other security hardware, you have to also be realistic about users. Most of our users are not reading Krebs and are technical enough to understand or want to understand hardware tokens and other advanced forms of two factor authentication. Just because it makes sense to this group doesn’t mean it will to the 94 year old bank customer who just wants to check their balance. All of these security updates need to be balanced between the risk to an account holder versus the ability of them to use the security mechanism in place.
Brian,
Your breakdown of core processors is way wrong. Just a heads up if this is important. The two largest providers, First Data and TSYS, are not even on the chart.
Richard,
It’s not my breakdown. I reference a source for that information in the story.
Also, the story is about the platforms used by small to mid-sized financial institutions. While TSYS and First Data are indeed huge and process a lot of transactions, none of the institutions I mentioned in the story use them, and I’d wager few smaller banks and credit unions do for their customer-facing online banking platforms.