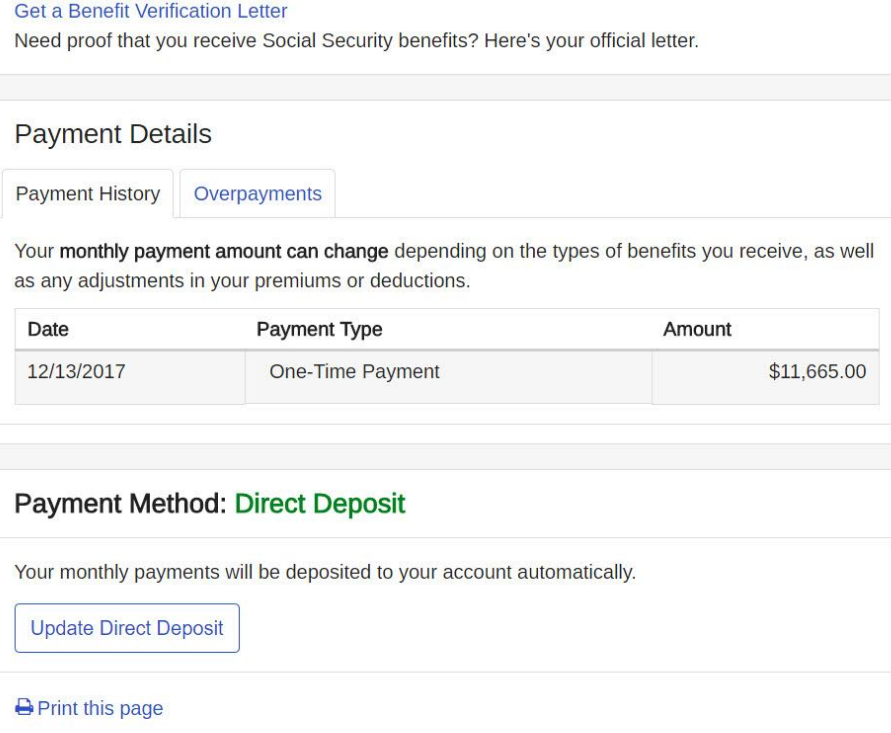
Today, Jan. 29, is officially the first day of the 2018 tax-filing season, also known as the day fraudsters start requesting phony tax refunds in the names of identity theft victims. Want to minimize the chances of getting hit by tax refund fraud this year? File your taxes before the bad guys can!
Tax refund fraud affects hundreds of thousands, if not millions, of U.S. citizens annually. Victims usually first learn of the crime after having their returns rejected because scammers beat them to it. Even those who are not required to file a return can be victims of refund fraud, as can those who are not actually due a refund from the IRS.

According to the IRS, consumer complaints over tax refund fraud have been declining steadily over the years as the IRS and states enact more stringent measures for screening potentially fraudulent applications.
If you file your taxes electronically and the return is rejected, and if you were the victim of identity theft (e.g., if your Social Security number and other information was leaked in the Equifax breach last year), you should submit an Identity Theft Affidavit (Form 14039). The IRS advises that if you suspect you are a victim of identity theft, continue to pay your taxes and file your tax return, even if you must do so by paper.
If the IRS believes you were likely the victim of tax refund fraud in the previous tax year they will likely send you a special filing PIN that needs to be entered along with this year’s return before the filing will be accepted by the IRS electronically. This year marks the third out of the last five that I’ve received one of these PINs from the IRS.
Of course, filing your taxes early to beat the fraudsters requires one to have all of the tax forms needed to do so. As a sole proprietor, this is a great challenge because many companies take their sweet time sending out 1099 forms and such (even though they’re required to do so by Jan. 31).
A great many companies are now turning to online services to deliver tax forms to contractors, employees and others. For example, I have received several notices via email regarding the availability of 1099 forms online; most say they are sending the forms in snail mail, but that if I need them sooner I can get them online if I just create an account or enter some personal information at some third-party site.
Having seen how so many of these sites handle personal information, I’m not terribly interested in volunteering more of it. According to Bankrate, taxpayers can still file their returns even if they don’t yet have all of their 1099s — as long as you have the correct information about how much you earned.
“Unlike a W-2, you generally don’t have to attach 1099s to your tax return,” Bankrate explains. “They are just issued so you’ll know how much to report, with copies going to the IRS so return processors can double-check your entries. As long as you have the correct information, you can put it on your tax form without having the statement in hand.” Continue reading





 Countless organizations rely on a hodgepodge of security software, hardware and services to find and detect cybersecurity intrusions before an incursion by malicious software or hackers has the chance to metastasize into a full-blown data breach.
Countless organizations rely on a hodgepodge of security software, hardware and services to find and detect cybersecurity intrusions before an incursion by malicious software or hackers has the chance to metastasize into a full-blown data breach.



 Last week’s story,
Last week’s story, 