KrebsOnSecurity recently featured a story about a New Mexico man who stands accused of using the now-defunct vDOS attack-for-hire service to hobble the Web sites of several former employers. That piece stated that I wasn’t aware of any other prosecutions related to vDOS customers, but as it happens there was a prosecution in the United Kingdom earlier this year of a man who’s admitted to both using and helping to administer vDOS. Here’s a look at some open-source clues that may have led to the U.K. man’s arrest.

Jack Chappell, outside of a court hearing in the U.K. earlier this year.
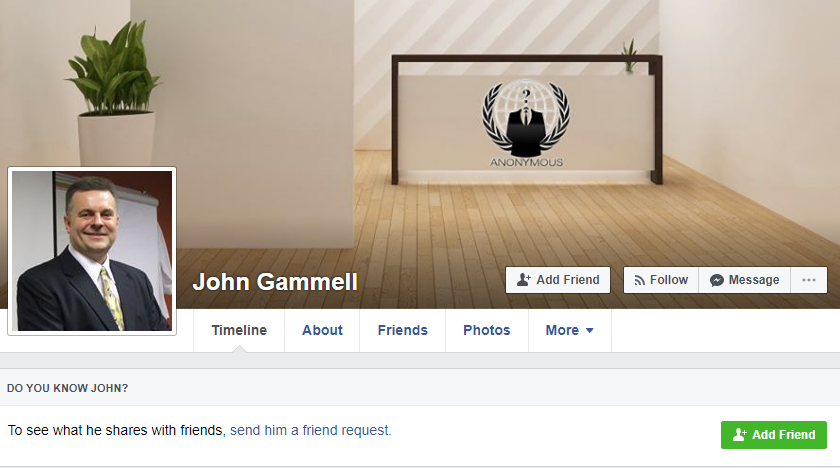
In early July 2017, the West Midlands Police in the U.K. arrested 19-year-old Stockport resident Jack Chappell and charged him with aiding the vDOS co-founders — two Israeli men who were arrested late year and charged with running the service.
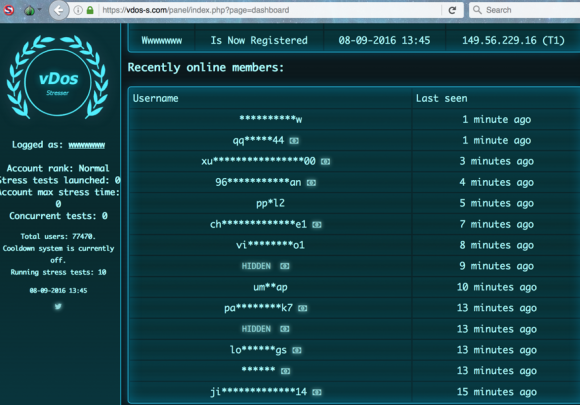
Until its demise in September 2016, vDOS was by far the most popular and powerful attack-for-hire service, allowing even completely unskilled Internet users to launch crippling assaults capable of knocking most Web sites offline. vDOS made more than $600,000 in just two of the four years it was in operation, launching more than 150,000 attacks against thousands of victims (including this site).
For his part, Chappell was charged with assisting in attacks against Web sites for some of the world’s largest companies, including Amazon, BBC, BT, Netflix, T-Mobile, Virgin Media, and Vodafone, between May 1, 2015 and April 30, 2016.
At the end of July 2017, Chappell pleaded guilty to those allegations, as well as charges of helping vDOS launder money from customers wishing to pay for attacks with PayPal accounts.
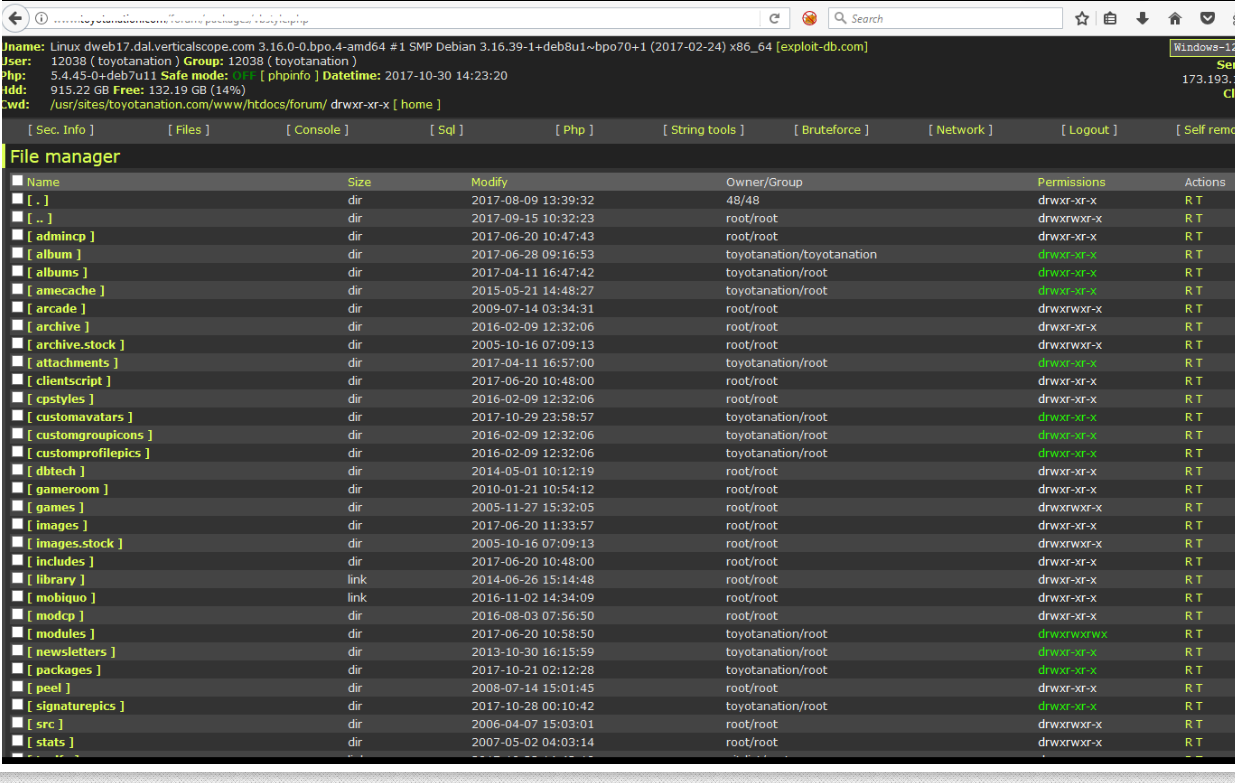
A big factor in that plea was the leak of the vDOS attacks, customer support and payments databases to this author and to U.S. law enforcement officials in the fall of 2016. Those databases provided extremely detailed information about co-conspirators, paying customers and victims.
But as with many other cybercrime investigations, the perpetrator in this case appears to have been caught thanks to a combination of several all-too-common factors, including password re-use, an active presence on the sprawling English-language hacking community Hackforums, and domain names registered in his real name. In combination, these clues provide a crucial bridge between Chappell’s online and real-world identities. Continue reading





 Four
Four

 Most financial institutions will let customers add verbal passwords or personal identification numbers (PINs) that are separate from any other PIN or online banking password you might use, although few will advertise this.
Most financial institutions will let customers add verbal passwords or personal identification numbers (PINs) that are separate from any other PIN or online banking password you might use, although few will advertise this.