Last week, I wrote about a “bulletproof hosting” provider that offers dodgy Web hosting that is insulated from takedown by abuse complaints or requests from Western law enforcement agencies. Today, I’ll look at one of that bulletproof provider’s biggest clients: Captchabot.com, a service that automates the solving of “CAPTCHAs,” those annoying agglomerations of squiggly numbers and letters that many online services require users to solve to help ensure that new accounts are not being auto-created by a computer.
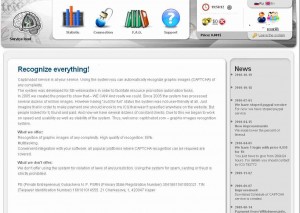 These so-called reverse Turing Tests can be exasperating for legitimate users, but these days they are little more than a speed bump for those who specialize in mass-creating bogus new accounts at popular online destinations like Facebook, MySpace, YouTube for use in spreading spyware and pimping spammy Web sites.
These so-called reverse Turing Tests can be exasperating for legitimate users, but these days they are little more than a speed bump for those who specialize in mass-creating bogus new accounts at popular online destinations like Facebook, MySpace, YouTube for use in spreading spyware and pimping spammy Web sites.
That’s thanks largely to services like Captchabot, which automate the solving of CAPTCHAs with the help of low-paid workers in China, India and Eastern Europe who earn pennies per hour deciphering the puzzles.
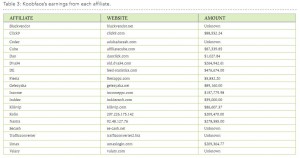
Captchabot charges clients based on how many thousand CAPTCHAs they ask the service solve: $1 buys about 1,000 solved CAPTCHAs. The service claims at least an 80 percent success rate, and customers only pay for CAPTCHAs that are solved correctly.
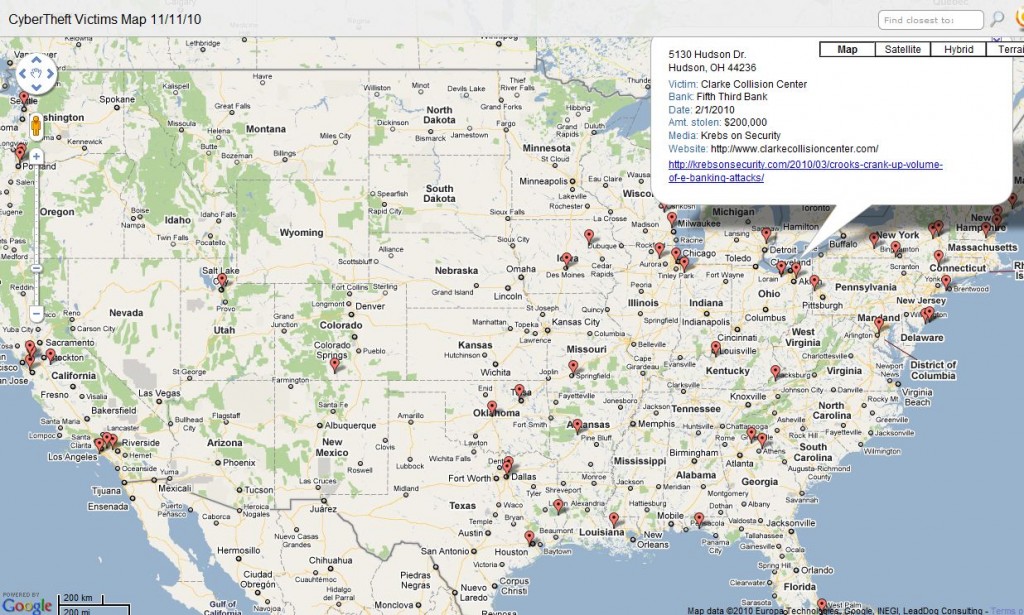
In their seminal paper (PDF) on CAPTCHA-solving services, researchers at UC San Diego earlier this year tried to estimate how many employees it would take to solve the daily workload of CAPTCHAs fed to the various services. The researchers guessed that Captchabot.com would need to have between 130 and 200 workers available more or less around the clock (for a look at how these services performed against CAPTCHAs required by MySpace, Google, Wikipedia and others, see this graphic.)
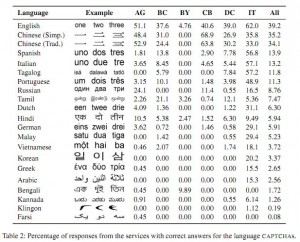 The researchers also sought to learn where most of the puzzle-solving workers resided, so they fed Captchabot and other services a variety of CAPTCHAs from different languages. The results, shown in the screen shot here, indicated that most of the workers were Chinese, English and Russian speakers.
The researchers also sought to learn where most of the puzzle-solving workers resided, so they fed Captchabot and other services a variety of CAPTCHAs from different languages. The results, shown in the screen shot here, indicated that most of the workers were Chinese, English and Russian speakers.
I contacted the owner of Captchabot.com, a hacker named Mirko Res, via online chat to see if I could fine-tune the UCSD estimates on the number of workers employed by the service, but he was unwilling to give an exact figure (“under NDA,” he explained). He did say, however, that the majority of the workers employed by his service live in Belarus, and that workers are only passed puzzles that can’t be solved by the service’s automated CAPTCHA-guessing algorithm.
“They using it for legal Webspam, like blog comments,” Res said of his operation’s customers. In fact, a widely-used forum- and blog-spamming tool known as XRumer relies exclusively on Captchabot to deliver its CAPTCHA-cracking capability.