Incessantly annoying and fraudulent robocalls. Corrupt wireless company employees taking hundreds of thousands of dollars in bribes to unlock and hijack mobile phone service. Wireless providers selling real-time customer location data, despite repeated promises to the contrary. A noticeable uptick in SIM-swapping attacks that lead to multi-million dollar cyberheists.
If you are somehow under the impression that you — the customer — are in control over the security, privacy and integrity of your mobile phone service, think again. And you’d be forgiven if you assumed the major wireless carriers or federal regulators had their hands firmly on the wheel.

No, a series of recent court cases and unfortunate developments highlight the sad reality that the wireless industry today has all but ceded control over this vital national resource to cybercriminals, scammers, corrupt employees and plain old corporate greed.
On Tuesday, Google announced that an unceasing deluge of automated robocalls had doomed a feature of its Google Voice service that sends transcripts of voicemails via text message.
Google said “certain carriers” are blocking the delivery of these messages because all too often the transcripts resulted from unsolicited robocalls, and that as a result the feature would be discontinued by Aug. 9. This is especially rich given that one big reason people use Google Voice in the first place is to screen unwanted communications from robocalls, mainly because the major wireless carriers have shown themselves incapable or else unwilling to do much to stem the tide of robocalls targeting their customers.
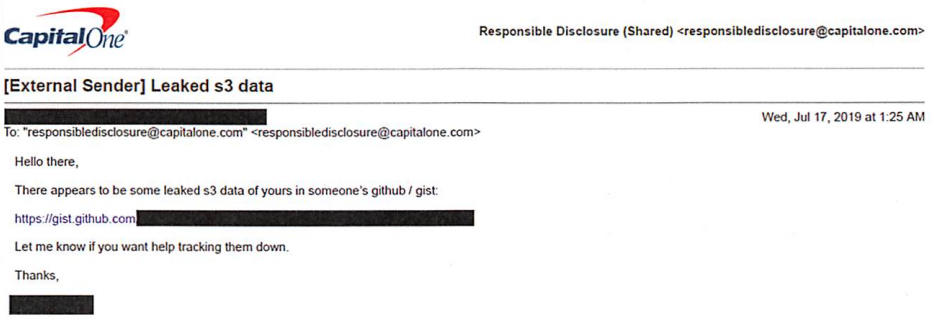
AT&T in particular has had a rough month. In July, the Electronic Frontier Foundation (EFF) filed a class action lawsuit on behalf of AT&T customers in California to stop the telecom giant and two data location aggregators from allowing numerous entities — including bounty hunters, car dealerships, landlords and stalkers — to access wireless customers’ real-time locations without authorization.
And on Monday, the U.S. Justice Department revealed that a Pakistani man was arrested and extradited to the United States to face charges of bribing numerous AT&T call-center employees to install malicious software and unauthorized hardware as part of a scheme to fraudulently unlock cell phones.
Ars Technica reports the scam resulted in millions of phones being removed from AT&T service and/or payment plans, and that the accused allegedly paid insiders hundreds of thousands of dollars to assist in the process.
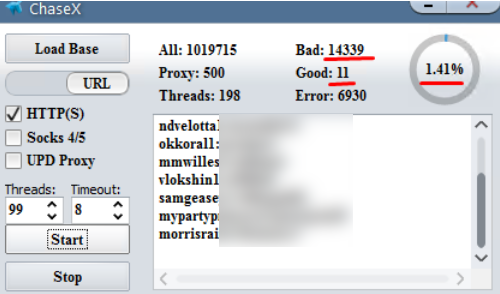
We should all probably be thankful that the defendant in this case wasn’t using his considerable access to aid criminals who specialize in conducting unauthorized SIM swaps, an extraordinarily invasive form of fraud in which scammers bribe or trick employees at mobile phone stores into seizing control of the target’s phone number and diverting all texts and phone calls to the attacker’s mobile device.
Late last month, a federal judge in New York rejected a request by AT&T to dismiss a $224 million lawsuit over a SIM-swapping incident that led to $24 million in stolen cryptocurrency.
The defendant in that case, 21-year-old Manhattan resident Nicholas Truglia, is alleged to have stolen more than $80 million from victims of SIM swapping, but he is only one of many individuals involved in this incredibly easy, increasingly common and lucrative scheme. The plaintiff in that case alleges that he was SIM-swapped on two different occasions, both allegedly involving crooked or else clueless employees at AT&T wireless stores.
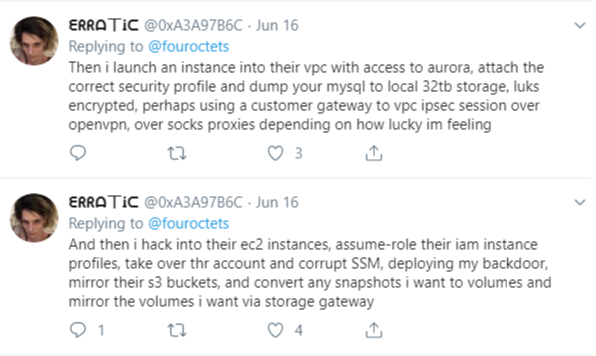
And let’s not forget about all the times various hackers figured out ways to remotely use a carrier’s own internal systems for looking up personal and account information on wireless subscribers.
So what the fresh hell is going on here? And is there any hope that lawmakers or regulators will do anything about these persistent problems? Gigi Sohn, a distinguished fellow at the Georgetown Institute for Technology Law and Policy, said the answer — at least in this administration — is probably a big “no.”
“The takeaway here is the complete and total abdication of any oversight of the mobile wireless industry,” Sohn told KrebsOnSecurity. “Our enforcement agencies aren’t doing anything on these topics right now, and we have a complete and total breakdown of oversight of these incredibly powerful and important companies.” Continue reading