MyPayrollHR, a now defunct cloud-based payroll processing firm based in upstate New York, abruptly ceased operations this past week after stiffing employees at thousands of companies. The ongoing debacle, which allegedly involves malfeasance on the part of the payroll company’s CEO, resulted in countless people having money drained from their bank accounts and has left nearly $35 million worth of payroll and tax payments in legal limbo.
Unlike many stories here about cloud service providers being extorted by hackers for ransomware payouts, this snafu appears to have been something of an inside job. Nevertheless, it is a story worth telling, in part because much of the media coverage of this incident so far has been somewhat disjointed, but also because it should serve as a warning to other payroll providers about how quickly and massively things can go wrong when a trusted partner unexpectedly turns rogue.
Clifton Park, NY-based MyPayrollHR — a subsidiary of ValueWise Corp. — disclosed last week in a rather unceremonious message to some 4,000 clients that it would be shutting its virtual doors and that companies which relied upon it to process payroll payments should kindly look elsewhere for such services going forward.
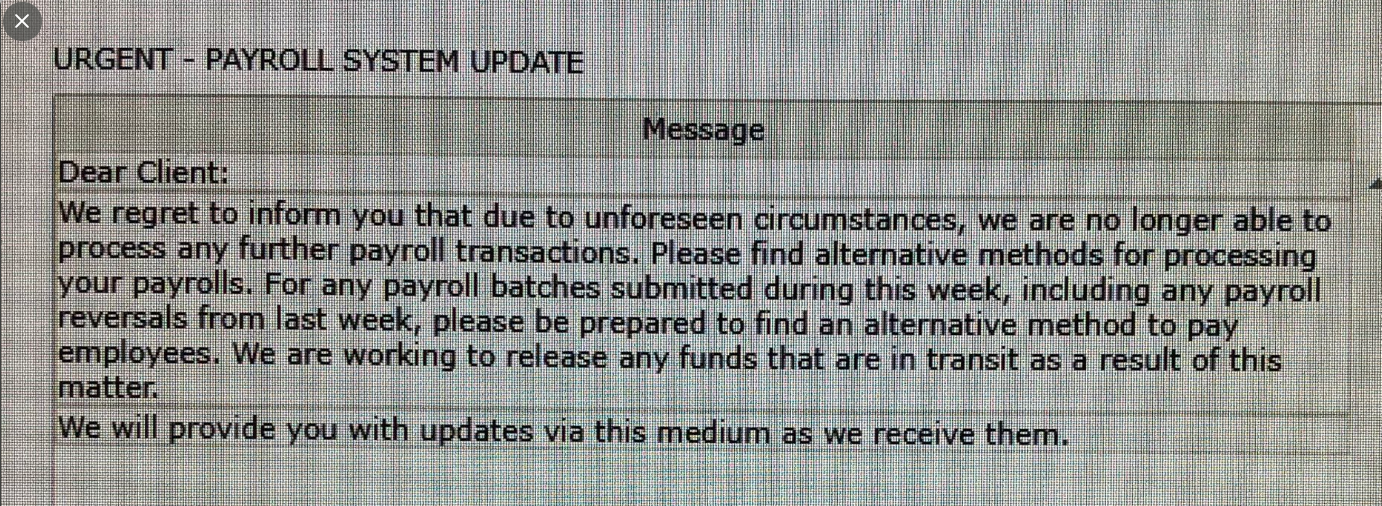
This communique came after employees at companies that depend on MyPayrollHR to receive direct deposits of their bi-weekly payroll payments discovered their bank accounts were instead debited for the amounts they would normally expect to accrue in a given pay period.
To make matters worse, many of those employees found their accounts had been dinged for two payroll periods — a month’s worth of wages — leaving their bank accounts dangerously in the red.
The remainder of this post is a deep-dive into what we know so far about what transpired, and how such an occurrence might be prevented in the future for other payroll processing firms.
A $26 MILLION TEXT FILE
To understand what’s at stake here requires a basic primer on how most of us get paid, which is a surprisingly convoluted process. In a typical scenario, our employer works with at least one third party company to make sure that on every other Friday what we’re owed gets deposited into our bank account.
The company that handled that process for MyPayrollHR is a California firm called Cachet Financial Services. Every other week for more than 12 years, MyPayrollHR has submitted a file to Cachet that told it which employee accounts at which banks should be credited and by how much.
According to interviews with Cachet, the way the process worked ran something like this: MyPayrollHR would send a digital file documenting deposits made by each of these client companies which laid out the amounts owed to each clients’ employees. In turn, those funds from MyPayrollHR client firms then would be deposited into a settlement or holding account maintained by Cachet.
From there, Cachet would take those sums and disburse them into the bank accounts of people whose employers used MyPayrollHR to manage their bi-weekly payroll payments.
But according to Cachet, something odd happened with the instructions file MyPayrollHR submitted on the afternoon of Wednesday, Sept. 4 that had never before transpired: MyPayrollHR requested that all of its clients’ payroll dollars be sent not to Cachet’s holding account but instead to an account at Pioneer Savings Bank that was operated and controlled by MyPayrollHR.
The total amount of this mass payroll deposit was approximately $26 million. Wendy Slavkin, general counsel for Cachet, told KrebsOnSecurity that her client then inquired with Pioneer Savings about the wayward deposit and was told MyPayrollHR’s bank account had been frozen.
Nevertheless, the payroll file submitted by MyPayrollHR instructed financial institutions for its various clients to pull $26 million from Cachet’s holding account — even though the usual deposits from MyPayrollHR’s client banks had not been made. Continue reading



 Two of the bugs quashed in this month’s patch batch (
Two of the bugs quashed in this month’s patch batch (