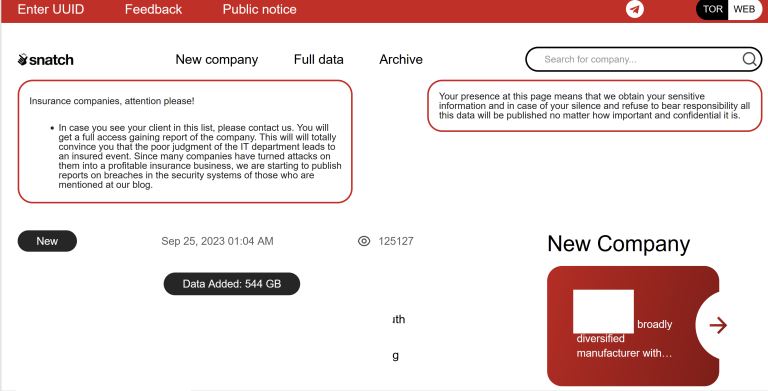
Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and the crime gang’s internal operations. Today, we’ll take a closer look at the history of Snatch, its alleged founder, and their claims that everyone has confused them with a different, older ransomware group by the same name.

According to a September 20, 2023 joint advisory from the FBI and the U.S. Cybersecurity and Infrastructure Security Administration (CISA), Snatch was originally named Team Truniger, based on the nickname of the group’s founder and organizer — Truniger.
The FBI/CISA report says Truniger previously operated as an affiliate of GandCrab, an early ransomware-as-a-service offering that closed up shop after several years and claims to have extorted more than $2 billion from victims. GandCrab dissolved in July 2019, and is thought to have become “REvil,” one of the most ruthless and rapacious Russian ransomware groups of all time.
The government says Snatch used a customized ransomware variant notable for rebooting Microsoft Windows devices into Safe Mode — enabling the ransomware to circumvent detection by antivirus or endpoint protection — and then encrypting files when few services are running.
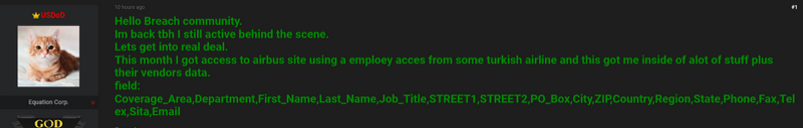
“Snatch threat actors have been observed purchasing previously stolen data from other ransomware variants in an attempt to further exploit victims into paying a ransom to avoid having their data released on Snatch’s extortion blog,” the FBI/CISA alert reads. It continues:
“Prior to deploying the ransomware, Snatch threat actors were observed spending up to three months on a victim’s system. Within this timeframe, Snatch threat actors exploited the victim’s network moving laterally across the victim’s network with RDP for the largest possible deployment of ransomware and searching for files and folders for data exfiltration followed by file encryption.”
New York City-based cyber intelligence firm Flashpoint said the Snatch ransomware group was created in 2018, based on Truniger’s recruitment both on Russian language cybercrime forums and public Russian programming boards. Flashpoint said Truniger recruited “pen testers” for a new, then-unnamed cybercrime group, by posting their private Jabber instant messenger contact details on multiple Russian language coding forums, as well as on Facebook.
“The command requires Windows system administrators,” Truniger’s ads explained. “Experience in backup, increase privileges, mikicatz, network. Details after contacting on jabber: truniger@xmpp[.]jp.”
In at least some of those recruitment ads — like one in 2018 on the forum sysadmins[.]ru –the username promoting Truniger’s contact information was Semen7907. In April 2020, Truniger was banned from two of the top Russian cybercrime forums, where members from both forums confirmed that Semen7907 was one of Truniger’s known aliases.
[SIDE NOTE: Truniger was banned because he purchased credentials to a company from a network access broker on the dark web, and although he promised to share a certain percentage of whatever ransom amount Truniger’s group extracted from the victim, Truniger paid the access broker just a few hundred dollars off of a six-figure ransom]. Continue reading