The owner of a Swedish company behind a popular remote administration tool (RAT) implicated in thousands of malware attacks shares the same name as a Swedish man who pleaded guilty in 2015 to co-creating the Blackshades RAT, a similar product that was used to infect more than half a million computers with malware, KrebsOnSecurity has learned.
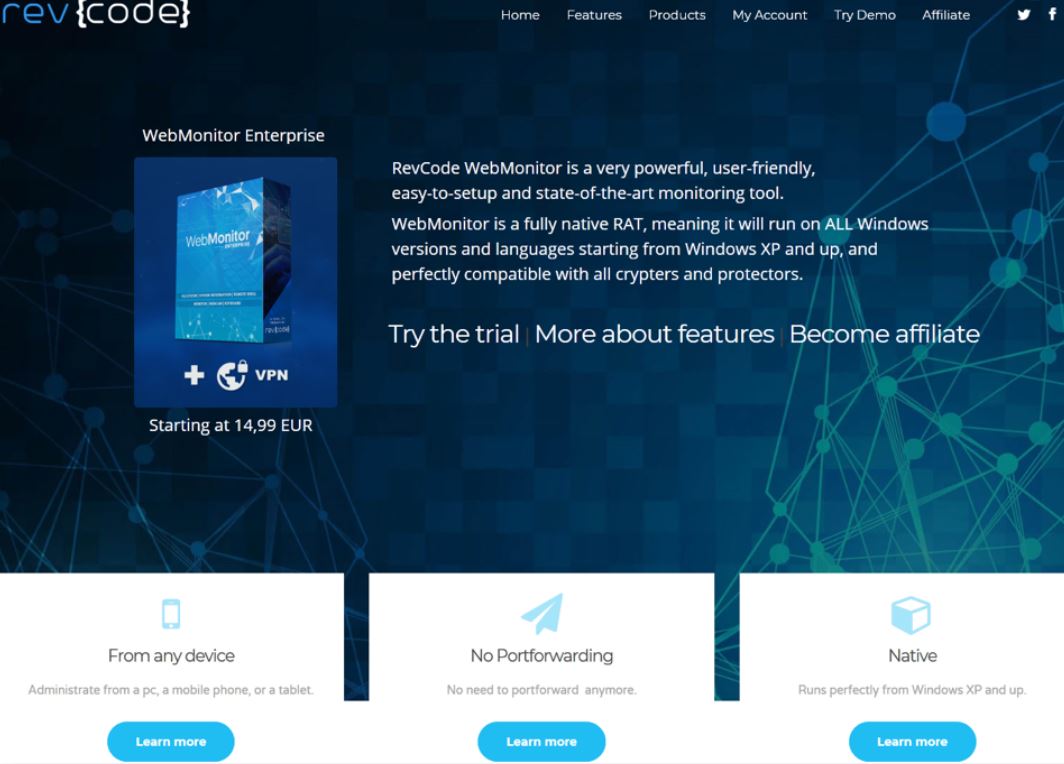
At issue is a program called “WebMonitor,” which was designed to allow users to remotely control a computer (or multiple machines) via a Web browser. The makers of WebMonitor, a company in Sweden called “RevCode,” say their product is legal and legitimate software “that helps firms and personal users handle the security of owned devices.”
But critics say WebMonitor is far more likely to be deployed on “pwned” devices, or those that are surreptitiously hacked. The software is broadly classified as malware by most antivirus companies, likely thanks to an advertised feature list that includes dumping the remote computer’s temporary memory; retrieving passwords from dozens of email programs; snarfing the target’s Wi-Fi credentials; and viewing the target’s Webcam.
In a writeup on WebMonitor published in April 2018, researchers from security firm Palo Alto Networks noted that the product has been primarily advertised on underground hacking forums, and that its developers promoted several qualities of the software likely to appeal to cybercriminals looking to secretly compromise PCs.
For example, RevCode’s website touted the software’s compatibility with all “crypters,” software that can encrypt, obfuscate and manipulate malware to make it harder to detect by antivirus programs. Palo Alto also noted WebMonitor includes the option to suppress any notification boxes that may pop up when the RAT is being installed on a computer.
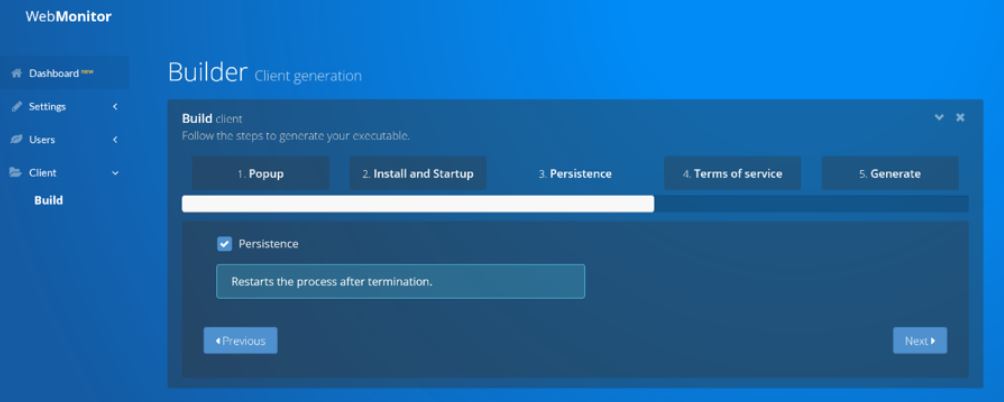
A screenshot of the WebMonitor builder panel.
RevCode maintains it is a legitimate company officially registered in Sweden that obeys all applicable Swedish laws. A few hours of searching online turned up an interesting record at Ratsit AB, a credit information service based in Sweden. That record indicates RevCode is owned by 28-year-old Swedish resident Alex Yücel.
In February 2015, a then 24-year-old Alex Yücel pleaded guilty in a U.S. court to computer hacking and to creating, marketing and selling Blackshades, a RAT that was used to compromise and spy on hundreds of thousands of computers. Arrested in Moldova in 2013 as part of a large-scale, international takedown against Blackshades and hundreds of customers, Yücel became the first person ever to be extradited from Moldova to the United States. Continue reading





 And yet, here I am again writing the second story this week about a possibly serious security breach at an Indian company that provides IT support and outsourcing for a ridiculous number of major U.S. corporations (spoiler alert: the second half of this story actually contains quite a bit of news about the breach investigation).
And yet, here I am again writing the second story this week about a possibly serious security breach at an Indian company that provides IT support and outsourcing for a ridiculous number of major U.S. corporations (spoiler alert: the second half of this story actually contains quite a bit of news about the breach investigation).

 According to security firm
According to security firm  Adobe’s Patch Tuesday includes security updates for its
Adobe’s Patch Tuesday includes security updates for its 

