Why Malware Crypting Services Deserve More Scrutiny
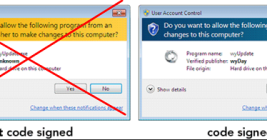
If you operate a cybercrime business that relies on disseminating malicious software, you probably also spend a good deal of time trying to disguise or “crypt” your malware so that it appears benign to antivirus and security products. In fact, the process of “crypting” malware is sufficiently complex and time-consuming that most serious cybercrooks will outsource this critical function to a handful of trusted third parties. This story explores the history and identity behind Cryptor[.]biz, a long-running crypting service that is trusted by some of the biggest names in cybercrime.