Microsoft Patch Tuesday, December 2023 Edition
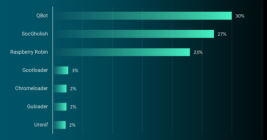
The final Patch Tuesday of 2023 is upon us, with Microsoft Corp. today releasing fixes for a relatively small number of security holes in its Windows operating systems and other software. Even more unusual, there are no known “zero-day” threats targeting any of the vulnerabilities in December’s patch batch. Still, four of the updates pushed out today address “critical” vulnerabilities that Microsoft says can be exploited by malware or malcontents to seize complete control over a vulnerable Windows device with little or no help from users.