The U.S. federal government is now in the process of sending Economic Impact Payments by direct deposit to millions of Americans. Most who are eligible for payments can expect to have funds direct-deposited into the same bank accounts listed on previous years’ tax filings sometime next week. Today, the Internal Revenue Service (IRS) stood up a site to collect bank account information from the many Americans who don’t usually file a tax return. The question is, will those non-filers have a chance to claim their payments before fraudsters do?

The IRS says the Economic Impact Payment will be $1,200 for individual or head of household filers, and $2,400 for married filing jointly if they are not a dependent of another taxpayer and have a work eligible Social Security number with adjusted gross income up to:
- $75,000 for individuals
- $112,500 for head of household filers and
- $150,000 for married couples filing joint returns
Taxpayers with higher incomes will receive more modest payments (reduced by $5 for each $100 above the $75,000/$112,500/$150,000 thresholds). Most people who who filed a tax return in 2018 and/or 2019 and provided their bank account information for a debit or credit should soon see an Economic Impact Payment direct-deposited into their bank accounts. Likewise, people drawing Social Security payments from the government will receive stimulus payments the same way.
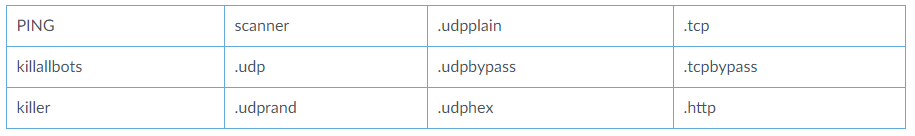
But there are millions of U.S. residents — including low-income workers and certain veterans and individuals with disabilities — who aren’t required to file a tax return but who are still eligible to receive at least a $1,200 stimulus payment. And earlier today, the IRS unveiled a Web site where it is asking those non-filers to provide their bank account information for direct deposits.
However, the possibility that fraudsters may intercept payments to these individuals seems very real, given the relatively lax identification requirements of this non-filer portal and the high incidence of tax refund fraud in years past. Each year, scam artists file phony tax refund requests on millions of Americans, regardless of whether or not the impersonated taxpayer is actually due a refund. In most cases, the victim only finds out when he or she goes to file their taxes and has the return rejected because it has already been filed by scammers.
In this case, fraudsters would simply need to identify the personal information for a pool of Americans who don’t normally file tax returns, which may well include a large number of people who are disabled, poor or simply do not have easy access to a computer or the Internet. Armed with this information, the scammers need only provide the target’s name, address, date of birth and Social Security number, and then supply their own bank account information to claim at least $1,200 in electronic payments.
Unfortunately, SSN and DOB data is not secret, nor is it hard to come by. As noted in countless stories here, there are multiple shops in the cybercrime underground that sell SSN and DOB data on tens of millions of Americans for a few dollars per record.
A review of the Web site set up to accept bank account information for the stimulus payments reveals few other mandatory identity checks to complete the filing process. It appears that all applicants need to provide a mobile phone number and verify they can receive text messages at that number, but beyond that the rest of the identity checks seem to be optional. Continue reading





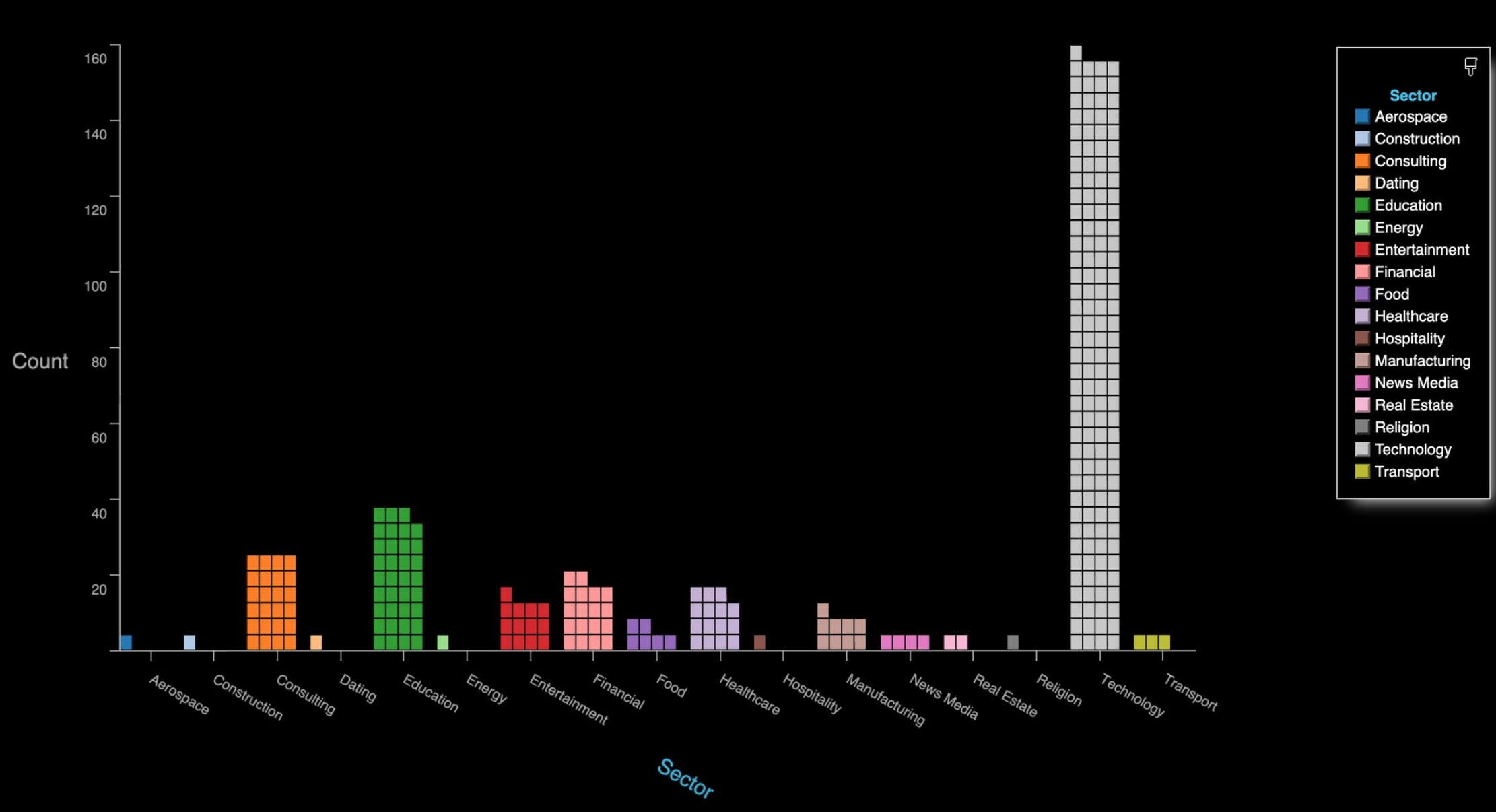


 London-based Finastra has offices in 42 countries and reported more than $2 billion in revenues last year. The company employs more than 10,000 people and has over 9,000 customers across 130 countries — including nearly all of the top 50 banks globally.
London-based Finastra has offices in 42 countries and reported more than $2 billion in revenues last year. The company employs more than 10,000 people and has over 9,000 customers across 130 countries — including nearly all of the top 50 banks globally.