Interview With a Crypto Scam Investment Spammer
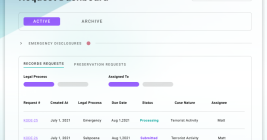
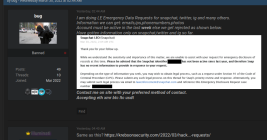
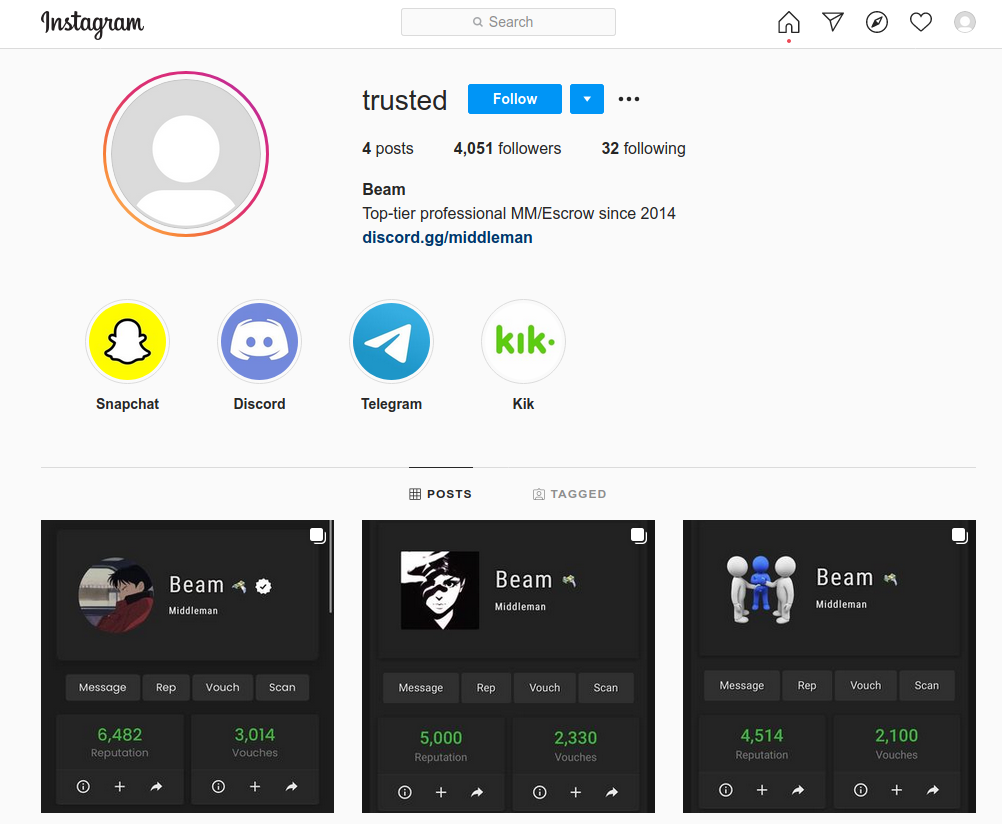
Social networks are constantly battling inauthentic bot accounts that send direct messages to users promoting scam cryptocurrency investment platforms. What follows is an interview with a Russian hacker responsible for a series of aggressive crypto spam campaigns that recently prompted several large Mastodon communities to temporarily halt new registrations. According to the hacker, their spam software has been in private use until the last few weeks, when it was released as open source code.