It’s been just over a year since the world witnessed some of the world’s top online Web sites being taken down for much of the day by “Mirai,” a zombie malware strain that enslaved “Internet of Things” (IoT) devices such as wireless routers, security cameras and digital video recorders for use in large-scale online attacks.
Now, experts are sounding the alarm about the emergence of what appears to be a far more powerful strain of IoT attack malware — variously named “Reaper” and “IoTroop” — that spreads via security holes in IoT software and hardware. And there are indications that over a million organizations may be affected already.
Reaper isn’t attacking anyone yet. For the moment it is apparently content to gather gloom to itself from the darkest reaches of the Internet. But if history is any teacher, we are likely enjoying a period of false calm before another humbling IoT attack wave breaks.

On Oct. 19, 2017, researchers from Israeli security firm CheckPoint announced they’ve been tracking the development of a massive new IoT botnet “forming to create a cyber-storm that could take down the Internet.” CheckPoint said the malware, which it called “IoTroop,” had already infected an estimated one million organizations.
The discovery came almost a year to the day after the Internet witnessed one of the most impactful cyberattacks ever — against online infrastructure firm Dyn at the hands of “Mirai,” an IoT malware strain that first surfaced in the summer of 2016. According to CheckPoint, however, this new IoT malware strain is “evolving and recruiting IoT devices at a far greater pace and with more potential damage than the Mirai botnet of 2016.”
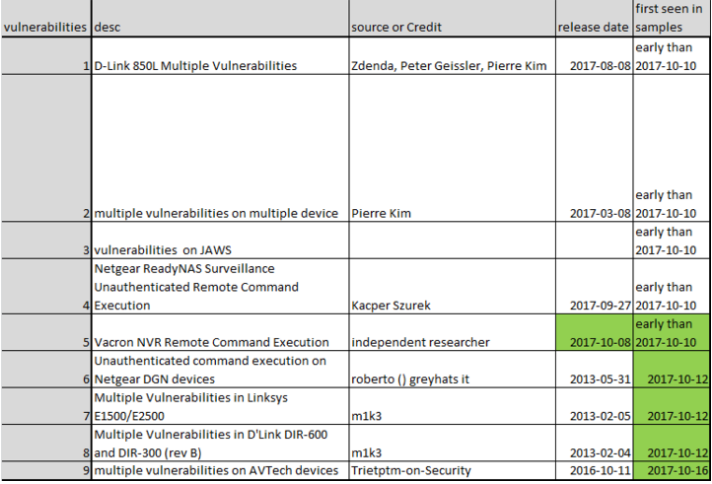
Unlike Mirai — which wriggles into vulnerable IoT devices using factory-default or hard-coded usernames and passwords — this newest IoT threat leverages at least nine known security vulnerabilities across nearly a dozen different device makers, including AVTECH, D-Link, GoAhead, Netgear, and Linksys, among others (click each vendor’s link to view security advisories for the flaws).
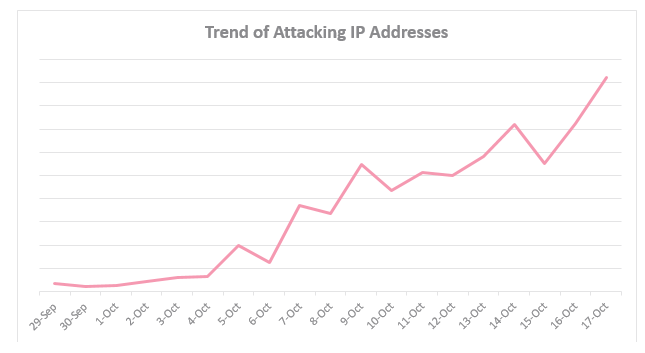
This graphic from CheckPoint charts a steep, recent rise in the number of Internet addresses trying to spread the new IoT malware variant, which CheckPoint calls “IoTroop.”
Both Mirai and IoTroop are computer worms; they are built to spread automatically from one infected device to another. Researchers can’t say for certain what IoTroop will be used for but it is based at least in part on Mirai, which was made to launch distributed denial of service (DDoS) attacks.
While DDoS attacks target a single Web site or Internet host, they often result in widespread collateral Internet disruption. IoT malware spreads by scanning the Internet for other vulnerable devices, and sometimes this scanning activity is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet.
However, according to research released Oct. 20 by Chinese security firm Netlab 360, the scanning performed by the new IoT malware strain (Netlab calls it the more memorable “Reaper”) is not very aggressive, and is intended to spread much more deliberately than Mirai. Netlab’s researchers say Reaper partially borrows some Mirai source code, but is significantly different from Mirai in several key behaviors, including an evolution that allows Reaper to more stealthily enlist new recruits and more easily fly under the radar of security tools looking for suspicious activity on the local network.
WARNING SIGNS, AND AN EVOLUTION
Few knew or realized it at the time, but even before the Mirai attacks commenced in August 2016 there were ample warning signs that something big was brewing. Much like the seawater sometimes recedes hundreds of feet from its normal coastline just before a deadly tsunami rushes ashore, cybercriminals spent the summer of 2016 using their state-of-the-art and new Mirai malware to siphon control over poorly-secured IoT devices from other hackers who were using inferior IoT malware strains.
Mirai was designed to wrest control over systems infected with variants of an early IoT malware contagion known as “Qbot” — and it did so with gusto immediately following its injection into the Internet in late July 2016. As documented in great detail in “Who Is Anna Senpai, the Mirai Worm Author?“, the apparent authors of Mirai taunted the many Qbot botmasters in hacker forum postings, promising they had just unleashed a new digital disease that would replace all Qbot infected devices with Mirai.
Mirai’s architects were true to their word: their creation mercilessly seized control over hundreds of thousands of IoT devices, spreading the disease globally and causing total extinction of Qbot variants. Mirai had evolved, and Qbot went the way of the dinosaurs.
On Sept. 20, 2016, KrebsOnSecurity.com was hit with a monster denial-of-service attack from the botnet powered by the first known copy of Mirai. That attack, which clocked in at 620 Gbps, was almost twice the size that my DDoS mitigation firm at the time Akamai had ever mitigated before. They’d been providing my site free protection for years, but when the Mirai attackers didn’t go away and turned up the heat, Akamai said the attack on this site was causing troubles for its paying customers, and it was time to go.
Thankfully, several days later Google brought KrebsOnSecurity into the stable of journalist and activist Web sites that qualify for its Project Shield program, which offers DDoS protection to newsrooms and Web sites facing various forms of online censorship.
The same original Mirai botnet would be used to launch a huge attack — over one terabit of data per second — against French hosting firm OVH. After the media attention paid to this site’s attack and the OVH assault, the Mirai authors released the source code for their creation, spawning dozens of copycat Mirai clones that all competed for the right to infest a finite pool of vulnerable IoT devices.
Probably the largest Mirai clone to rise out of the source code spill was used in a highly disruptive attack on Oct. 20, 2016 against Internet infrastructure giant Dyn (now part of Oracle). Some of the Internet’s biggest destinations — including Twitter, SoundCloud, Spotify and Reddit — were unreachable for large chunks of time that day because Mirai targeted a critical service that Dyn provides these companies.
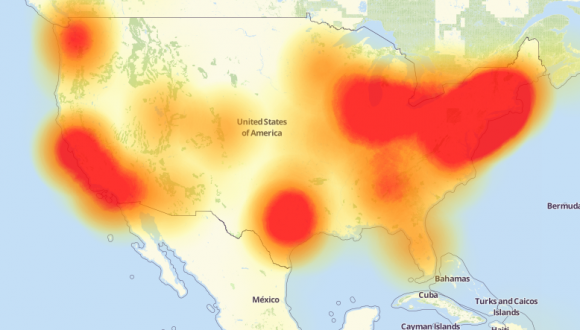
A depiction of the outages caused by the Mirai attacks on Dyn, an Internet infrastructure company. Source: Downdetector.com.
[AUTHOR’S NOTE: Some people believe that the Dyn attack was in retribution for information presented publicly hours before the attack by Dyn researcher Doug Madory. The talk was about research we had worked on together for a story exploring the rather sketchy history of a DDoS mitigation firm that had a talent for annexing Internet address space from its neighbors in a personal grudge match between that mitigation firm and the original Mirai authors and botmasters.]
It’s a safe bet that whoever is responsible for building this new Reaper IoT botnet will have more than enough firepower capable of executing Dyn-like attacks at Internet pressure points. Attacks like these can cause widespread Internet disruption because they target virtual gateways where third-party infrastructure providers communicate with hordes of customer Web sites, which in turn feed the online habits of countless Internet users.
It’s critical to observe that Reaper may not have been built for launching DDoS attacks: A global network of millions of hacked IoT devices can be used for a variety of purposes — such as serving as a sort of distributed proxy or anonymity network — or building a pool of infected devices that can serve as jumping-off points for exploring and exploiting other devices within compromised corporate networks.
“While some technical aspects lead us to suspect a possible connection to the Mirai botnet, this is an entirely new campaign rapidly spreading throughout the globe,” CheckPoint warns. “It is too early to assess the intentions of the threat actors behind it, but it is vital to have the proper preparations and defense mechanisms in place before an attack strikes.”
AND THE GOOD NEWS IS?
There have been positive developments on the IoT security front: Two possible authors of Mirai have been identified (if not yet charged), and some of Mirai’s biggest botmasters have been arrested and sentenced.
Some of the most deadly DDoS attack-for-hire services on the Internet were either run out of business by Mirai or have been forcibly shuttered in the past year, including vDOS — one of the Internet’s longest-running attack services. The alleged providers of vDOS — two Israeli men first outed by KrebsOnSecurity after their service was massively hacked last year — were later arrested and are currently awaiting trial in Israel for related cybercrime charges.
Using a combination of arrests and interviews, the FBI and its counterparts in Europe have made it clear that patronizing or selling DDoS-for-hire services — often known as “booters” or “stressers” — is illegal activity that can land violators in jail.
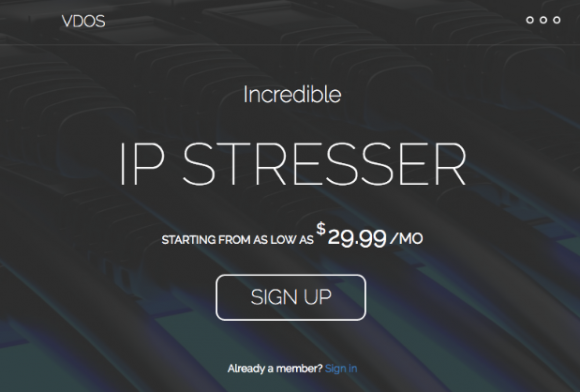
The front page of vDOS, when it was still online last year. vDOS was powered by an IoT botnet similar to Mirai and Reaper.
Public awareness of IoT security is on the rise, with lawmakers in Washington promising legislative action if the tech industry continues to churn out junky IoT hardware that is the Internet-equivalent of toxic waste.
Nevertheless, IoT device makers continue to ship products with either little to no security turned on by default or with ill-advised features which can be used to subvert any built-in security.
WHAT YOU CAN DO
According to Netlab, about half of the security vulnerabilities exploited by Reaper were first detailed in just the past few months, suggesting there may be a great number of unpatched and vulnerable systems in real danger from this new IoT malware strain.
Check to make sure your network isn’t part of the problem: Netlab’s advisory links to specific patches available by vendor, as well as indicators of compromise and the location of various Reaper control networks. CheckPoint’s post breaks down affected devices by version number but doesn’t appear to include links to security advisories or patches.
Please note that many of the affected devices are cameras or DVRs, but there also are quite a few consumer wired/wireless routers listed here (particularly for D-Link and Linksys devices).
One incessant problem with popular IoT devices is the inclusion of peer-to-peer (P2P) networking capability inside countless security cameras, DVRs and other gear. Jake Reynolds, a partner and consultant at Kansas City, Mo.-based Depth Security, published earlier this month research on a serious P2P weakness built into many FLIR/Lorex DVRs and security cameras that could let attackers remotely locate and gain access to vulnerable systems that otherwise are not directly connected to the Internet (FLIR’s updated advisory and patches are here).
In Feb. 2016, KrebsOnSecurity warned about a similar weakness powering the P2P component embedded in countless security cameras made by Foscam. That story noted that while the P2P component was turned on by default, disabling it in the security settings of the device did nothing to actually turn off P2P communications. Being able to do that was only possible after applying a firmware patch Foscam made available after users started complaining. My advice is to stay away from products that advertise P2P functionality.
Another reason IoT devices are ripe for exploitation by worms like Reaper and Mirai is that vendors infrequently release security updates for their firmware, and when they do there’s often no easy method available to notify users. Also, these updates are notoriously hard to do and easy to screw up, often leaving the unwary and unlearned with an oversized paperweight after a botched firmware update. So if it’s time to update your device, do it slowly and carefully.
What’s interesting about Reaper is that it is currently built to live harmoniously with Mirai. It’s not immediately clear whether the two IoT malware strains compete for any of the same devices, although some overlaps are bound to occur — particularly as the Reaper authors add new functionality and spreading mechanisms (both Netlab and Checkpoint say the Reaper code appears to be a work-in-progress).
That new Reaper functionality could well include the ability to seek out and supplant Mirai infections (much like Mirai did with Qbot), which would help Reaper to grow to even more terrifying numbers.
No matter what innovation Reaper brings, I’m hopeful that the knowledge being shared within the security community about how to defend against the Mirai attacks today will prove useful in ultimately helping to blunt any attacks from Reaper tomorrow. <Fingers crossed>
Speaking of calms before storms, KrebsOnSecurity.com soon will get its first major facelift since its inception in Dec. 2009. The changes are more structural than cosmetic; we’re striving to make the site more friendly to mobile devices, while maintaining the simple, almost minimalist look and feel of this site. I’ll make another announcement as we get closer to the switch (just so everyone doesn’t freak out and report the site’s been hacked).




Thanks for this info Krebs, as always.
My kingdom, my kingdom for a y-axis label on the first CheckPoint plot!
The rest of the article is certainly concerning, but without scale and labeling, all we know from that graph is that something is going up on a daily basis.
His kingdom, his kingdom for an x-axis label on the first CheckPoint plot!
His kingdoom! Her kingdoom for an x-axis labull on th second CheckPoint plot!
meaningless comments!
He was not 100% clear in the his post, but he was commenting on the lack of numbers for part of the graph. If there is anything you don’t understand here, just ask. Many of us are glad to help…
That was exactly my first thought – unlabeled graphs can’t be interpreted.
The book “How to Lie with Statistics” by Darrell Huff (ISBN: 978-0-393-31072-6) addresses this very point, along with other statistical shenanigans.
Have researchers been able to identify C&Cs and involved domain names ?
We need a “patch or die” worm.
Recruits a botnet of unpatched and unpatchable devices, then permanently bricks every single one.
A few rounds of that and the message might sink in.
I am not recommending anyone does this because they will go to prison, but I still wish someone would.
Ben, you’re not the 1st 1 to wish 4 such. Problem is, the Gov’t doesn’t seem to care, manufacturers of the IoT devices don’t seem to care, ISP don’t seem to care, people who own the devices don’t seem to care, yet everyone gets all bent out of shape when things go wrong. Well, do something about the problem “before” it becomes a problem! Patch, change passwords, buy more reliable Iot’s. But I do hope some 12 yr old decides to stop the problem (he won’t go to jail, will he?).
I’ve noticed more probes of my ports for a few months, nothing major like last year though. But I’m seeing lots of probes from w/i the US (probably slaved PC’s), including one I never saw in a decade of probe logs – Microsoft Media Server (MMS). I’m getting port probes way beyond just telnet, maybe something is up.
Unfortunately thanks to widespread use of netnannies and similar childproofing our 12 year olds aren’t as technical as the generation before them.
When you shove them into padded rooms for their entire childhood, you can’t be surprised that all they know are padded rooms.
As long as people are making money, they will not care
brickerbot may interest you
Paul – “brickerbot may interest you”
Just did a bit of reading on Brickerbot. I can see the carnage it could cause as it doesn’t discriminate between an unsecured but vital piece of equipment in a hospital and the average IoT camera. Both get bricked.
“Strong password protection” is the key that manufacturers can offer consumers of IoT devices, unlocking such a device would require the same key, much harder to do.
I have no IoT dog in this fight so I don’t care but it can still affect me via, say, that hospital device if I’m a patient! I hope that if anything good comes out of this new mess, it’s that manufacturers and end users will finally take steps to help prevent Webageddon from making the Internet useless for everyone.
I reacted to the Equifax breach by freezing my credit with all potential access points for the bad guys. Better to do something now rather than wait and see if I’m going to be affected. Something about a ounce of prevention being worth a pound of cure.
If I do buy an Iot device, you can be sure it will be one that offers strong password protection, one that at least tries to prevent the pound of cure approach. More expensive up front perhaps, but cheaper in the long run.
It will do nothing. they are using the smart meter on your house to control anything in it. I know because I have been dealing with it involuntarily for about 17 years (since 2004). I have a iPhone 6s with sprint service, Verizon home internet suite with security and still they are either not interested in things they can fix then and there so the gapping security hole gets ignored to a Krebs-like security researcher finds and then reports the problem. I’ve sent the screenshot of the “springboard” on my iPhone and they were stumped. the actual springboard icon is missing. I tried to explain that the ITouch feature is not working correctly never heard anything yet.
I wish you well with the web site changes.
Oh and thanks for the article as well.. Appreciate the work you do.
Two of my clients suffered their DVR’s being recruited to the Mirai Botnet earlier this year. AVTECH have been unresponsive and as a short-term fix, unexpected ports were configured prevent the devices being compromised. Each compromised device had an IP address applied in the 10.*.*.* range (I can’t remember the actual configuration). The devices went off line and the performance, even at the local console was severely degraded. The problem for my clients is that they require access to these DVR’s as a key business requirement. They haven’t been hacked since the ports were changed but reading further I see that the new variant of this attack no longer requires the admin password to commandeer the device. Does anyone know if it is possible to detect if they have been compromised?
Reconsider cheering on brickerbot!
There probably is no economic answer to unsecured devices, except to disable them.
https://arstechnica.com/information-technology/2017/04/brickerbot-the-permanent-denial-of-service-botnet-is-back-with-a-vengeance/
What port(s) do IOTs use? Perhaps something could be done to beef up security at that level.
Thanks, Brian!
Regards,
Short non technical answer:
They use all ports.
That’s not a solution.
How vulnerable are self-funded and installed Orwell Telescreens Amazon Echo, Echo Look, Tap, etc. to hacking? Did they do the smart things security-wise?
Looks like we’re going to see a familiar face on the IoT vulnerability subject next week on Vice channel’s Cyberwar series.
Yup, recorded that in late spring. Will be great to see what they’ve done with it. I’ve enjoyed the series.
@kerbonsecurity did you ever follow up on the 503C you where thinking of setting up in 2016? ‘The Center for the Defense of Internet Journalism’ for those in the journalism community that may require protection from large attacks such as the one you endured?
Thanks,
Hi Brian, thanks for the article !
Just as a note: “CheckPoint” is two words, “Check Point”.
Please add a vertical axis scale to the graph of “Trending Attack IP Addresses.” Would like see order of magnitude – use log-scale.
Since several people have commented on this, I went to Check Point to find their graph – and they do not have a vertical axis on it, so it would be difficult for Brian to provide one. Looks like it is Check Point that needs to define the scale on their graph.
It appears a firmware update is available for the Linksys e1500 router after the identified vulnerabilities. Hopefully it can mitigate these vulnerabilities. Thanks for bringing this to our attention Mr Krebs.
If this is big enough and does enough damage, it might be the wake up call that is needed to get the everyone to take IOT security seriously.
Wow, that chart! The one from Checkpoint… It’s so… Meaningless.
I see horizontal lines, but they don’t mean anything.
While other readers comment that the article is good, it’s slop like this (and previous editing problems) that make me stop reading and just skip for the point. Get it together Krebs, and hire an editor.
More than likely it was intentionally left off by CP so the authors couldn’t use it to determine the source(s) of their data.
Whatever amount they note will not accurately match the real-world installations, so by correlating groups of systems you can do simple math to determine which groups CP has access to and shut down their insight into your botnet.
Unless you’re paying Brian to provide you with information, you’re not in a position to make demands. Its kind of like people who use an open source project then make demands to the author – sorry but it doesn’t work that way.
Thank you Seymour!!!!! I agree with you. Brian does a great service for us…maybe we need to exert a little of our own effort to get a better understanding rather than putting a demand we have no right to do on Brian.
Complain to Checkpoint, not Krebs. It’s identical to what’s on the Checkpoint site, as noted.
The CheckPoint graph offers a rough summary of number of sources of infection worldwide.
The Y-axis represents number of organizations infected, with increments of 100,000, and the X-axis is the time over which this was discovered, starting “the last few days of September.” September 29th is the first coordinate labeled.
Thanks for that, Louise. That helps a lot.
Thanks for keeping an eye on this, Brian. I wonder about “smart” tvs, seems like they could be similarly vulnerable. And the lucky hacker might get an earful of archived voice commands…
Brian,
Thanks for the very thought provoking post.
You have prompted me to start investigating yet another IoT device in my home. The satellite receiver in my living room advertises itself as a WiFi connection point. I have no idea of its security settings, who can see it, who it talks to, or who can access it….
At the very least, find the default password and change it. Ideally if you don’t use the WAP, disable it.
Y AXIS LABEL WHY YOU NO HAVE?!?!?!?!?!?!?!
graph fail. with great fail. in the fail fail.
Always a good idea to read through the earlier comments before posting yours. Might save you a bit of time. Also embarrassment. 🙂
BrickerBot sounds interesting, but I agree with the comment against it. There are better and safer ways to “fix” the Internet.
I would rather see a bot that finds a problem send a notice to the tech contact on the domain name (if there is one), and record the date and time of the problem. After some period of time the bot can return to see if the problem has been fixed, and if not contact the other domain contacts.
If there is no domain involved, then using IP WHOIS the person or organization for the IP block can be notified. Failing that, I would try The upstream provider. At some point if the problem is not fixed and especially if an IP range contains many problems, that segment should be isolated or added to a black list.
If we can’t fix this, I foresee a future where we have two Internets, one public and one private. The private Internet will be something we pay for where the providers have a way to enforce any rules they see fit to establish. On it, you can expect to be really safe and unoffended with no parental restrictions needed.
With regard to IOT, no problem for me: I’ve never trusted the idea of remote access of stuff in my home. If I can remote control, someone else can remote control.
Our government and utility providers should also remember that if they can remote control something, bad guys can remote control, too.
Brian, please don’t make this site adaptive to devices. I REALLY HATE WHEN WEBSITES feed me their mobile versions, even when I’m using a small screen. And one thing I have liked on this site is that it works perfectly, identically, and consistently with or without Javascript.
Thanks for the heads up! I did not see Apple’s AirPort Listed, so for this I am thankful! It never hurts to be watchful, especially with the current WPA2 Threat, which is mild as compared to your report above! The hit just keep on rolling! Thank heaven for krebsonsecurity.com !
Considering the new push for money from Amazon with their “Amazon Key”, I wonder how long before it becomes a “prime” (pun intended) target for hackers. Not on my wish list but I’m sure the NSA would like all of us to have one, would make it so much easier to keep an eye/ear on us 😉
Haven’t even read the article yet. I just love the little IT men in the pic.
For God’s sake, Brian. “Impactful” is not a word. Your English teacher would have slapped you. Degradation by respected journalists of the English language is as slippery a slope as our slide into the cyber netherworld.
-Bob
Bob,
There’s nothing incorrect about the word impactful. Can’t help it if someone told you some time ago that it was not a word, but I assure you it is. Languages are living organisms that change over time. Maybe if your own vocabulary wasn’t so fossilized, you’d recognize this. Merriam-Webster agrees it’s a word, btw: https://www.merriam-webster.com/dictionary/impactful